NSE6_FWF-6.4 Certification Exam Dumps Questions in here [Dec-2021]
Updated NSE6_FWF-6.4 Exam Practice Test Questions
NEW QUESTION 15
How are wireless clients assigned to a dynamic VLAN configured for hash mode?
- A. Using the current number of wireless clients connected to the SSID and the group the FortiAP is a member of
- B. Using the current number of wireless clients connected to the SSID and the number of VLANs available in the pool
- C. Using the current number of wireless clients connected to the SSID and the number of clients allocated to each of the VLANs
- D. Using the current number of wireless clients connected to the SSID and the number of IPs available in the least busy VLAN
Answer: B
Explanation:
VLAN from the VLAN pool based on a hash of the current number of SSID clients and the number of entries in the VLAN pool.
NEW QUESTION 16
A tunnel mode wireless network is configured on a FortiGate wireless controller.
Which task must be completed before the wireless network can be used?
- A. Security Fabric and HTTPS must be enabled on the wireless network interface
- B. The wireless network interface must be assigned a Layer 3 address
- C. The wireless network to Internet firewall policy must be configured
- D. The new network must be manually assigned to a FortiAP profile.
Answer: C
Explanation:
A FortiGate unit is an industry leading enterprise firewall. In addition to consolidating all the functions of a network firewall, IPS, anti-malware, VPN, WAN optimization, Web filtering, and application control in a single platform, FortiGate also has an integrated Wi-Fi controller.
NEW QUESTION 17
When configuring a wireless network for dynamic VLAN allocation, which three IETF attributes must be supplied by the radius server? (Choose three.)
- A. 83 Tunnel-Preference
- B. 65 Tunnel-Medium-Type
- C. 81 Tunnel-Private-Group-ID
- D. 64 Tunnel-Type
- E. 58 Egress-VLAN-Name
Answer: B,C,D
Explanation:
The RADIUS user attributes used for the VLAN ID assignment are:
IETF 64 (Tunnel Type)-Set this to VLAN.
IETF 65 (Tunnel Medium Type)-Set this to 802
IETF 81 (Tunnel Private Group ID)-Set this to VLAN ID.
NEW QUESTION 18
Six APs are located in a remotely based branch office and are managed by a centrally hosted FortiGate. Multiple wireless users frequently connect and roam between the APs in the remote office.
The network they connect to, is secured with WPA2-PSK. As currently configured, the WAN connection between the branch office and the centrally hosted FortiGate is unreliable.
Which configuration would enable the most reliable wireless connectivity for the remote clients?
- A. Configure a tunnel mode wireless network and enable split tunneling to the local network
- B. Configure a bridge mode wireless network and enable the Local standalone configuration option
- C. Configure a bridge mode wireless network and enable the Local authentication configuration option
- D. Install supported FortiAP and configure a bridge mode wireless network
Answer: A
NEW QUESTION 19
When using FortiPresence as a captive portal, which two types of public authentication services can be used to access guest Wi-Fi? (Choose two.)
- A. Social networks authentication
- B. Short message service authentication
- C. Hardware security token authentication
- D. Software security token authentication
Answer: A,C
Explanation:
This information along with the social network authentication logins with Facebook, Google, Instagram, LinkedIn, or FortiPresence using your WiFi.
Captive Portal configurations for social media logins and internet access. You can add and manage sites using the integrated Google maps and manoeuvre your hardware infrastructure easily.
NEW QUESTION 20
What is the first discovery method used by FortiAP to locate the FortiGate wireless controller in the default configuration?
- A. Static
- B. Multicast
- C. DHCP
- D. Broadcast
Answer: C
NEW QUESTION 21
Which two statements about background rogue scanning are correct? (Choose two.)
- A. When detecting rogue APs, a dedicated radio configured for background scanning can suppress the rogue AP
- B. A dedicated radio configured for background scanning can detect rogue devices on all other channels in its configured frequency band
- C. Background rogue scanning requires DARRP to be enabled on the AP instance
- D. A dedicated radio configured for background scanning can support the connection of wireless clients
Answer: A,D
Explanation:
To enable rogue AP scanning
NEW QUESTION 22
Which two configurations are compatible for Wireless Single Sign-On (WSSO)? (Choose two.)
- A. A VAP configured for WPA2 or 3 Enterprise
- B. A VAP configured for captive portal authentication
- C. A VAP configured to authenticate locally on FortiGate
- D. A VAP configured to authenticate using a radius server
Answer: A,D
Explanation:
In the SSID choose WPA2-Enterprise authentication.
WSSO is RADIUS-based authentication that passes the user's user group memberships to the FortiGate.
NEW QUESTION 23
When configuring Auto TX Power control on an AP radio, which two statements best describe how the radio responds? (Choose two.)
- A. When the AP detects any interference from a trusted neighboring AP stronger that -70 dBm, it will reduce its transmission power until it reaches the minimum configured TX power limit.
- B. When the AP detects any other wireless signal stronger that -70 dBm, it will reduce its transmission power until it reaches the minimum configured TX power limit.
- C. When the AP detects PF Interference from an unknown source such as a cordless phone with a signal stronger that -70 dBm, it will increase its transmission power until it reaches the maximum configured TX power limit.
- D. When the AP detects any wireless client signal weaker than -70 dBm, it will reduce its transmission power until it reaches the maximum configured TX power limit.
Answer: B,D
NEW QUESTION 24
Refer to the exhibits.
Exhibit A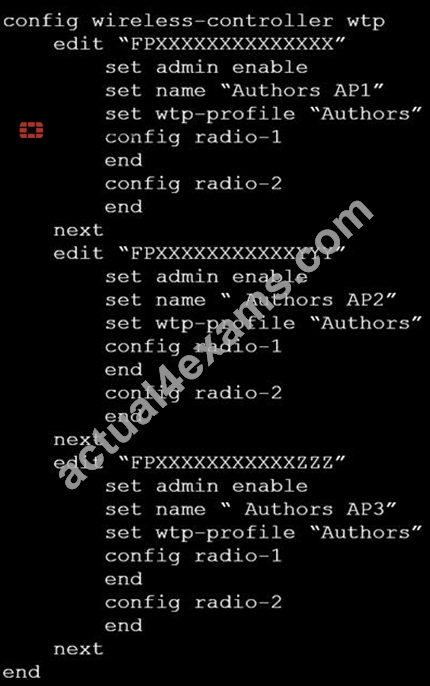
Exhibit B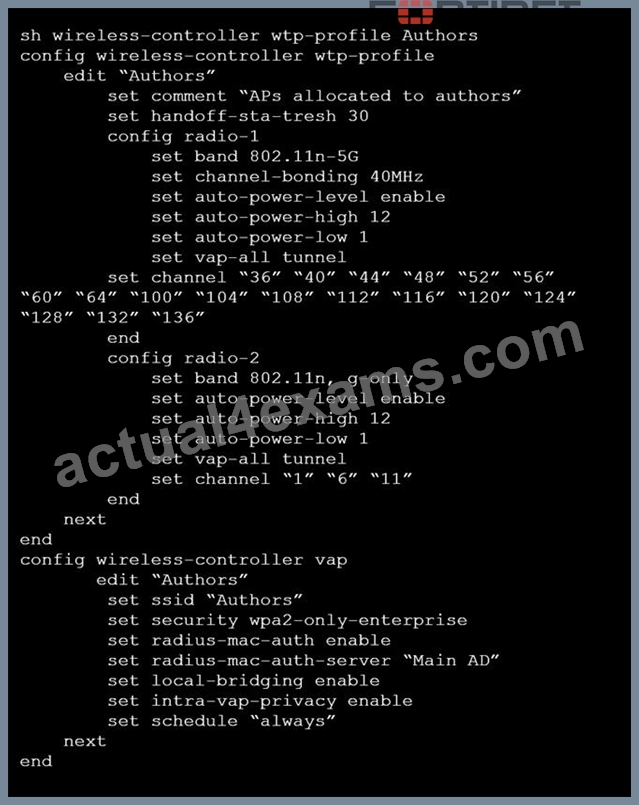
A wireless network has been created to support a group of users in a specific area of a building. The wireless network is configured but users are unable to connect to it. The exhibits show the relevant controller configuration for the APs and the wireless network.
Which two configuration changes will resolve the issue? (Choose two.)
- A. Disable intra-vap-privacy for the Authors vap-wireless network
- B. For both interfaces in the wtp-profile, configure set vaps to be "Authors"
- C. For both interfaces in the wtp-profile, configure vap-all to be manual
- D. Increase the transmission power of the AP radio interfaces
Answer: A,C
NEW QUESTION 25
Which two phases are part of the process to plan a wireless design project? (Choose two.)
- A. Project information phase
- B. Site survey phase
- C. Installation phase
- D. Hardware selection phase
Answer: B,C
Explanation:
Reference:
https://www.automation.com/en-us/articles/2015-2/wireless-device-network-planning-and-design
NEW QUESTION 26
Which statement is correct about security profiles on FortiAP devices?
- A. FortiGate performs inspection the wireless traffic
- B. Security profiles on FortiAP devices can use FortiGate subscription to inspect the traffic
- C. Disable DTLS on FortiAP
- D. Only bridge mode SSIDs can apply the security profiles
Answer: D
NEW QUESTION 27
......
Verified NSE6_FWF-6.4 dumps Q&As 100% Pass in First Attempt Guaranteed Updated Dump: https://drive.google.com/open?id=1mqvg1n0SYo0akNSaKxhdB2QMunL-0i9D
Pass NSE 6 Network Security Specialist NSE6_FWF-6.4 Exam With 30 Questions: https://www.actual4exams.com/NSE6_FWF-6.4-valid-dump.html

