156-915.80 Dumps - Grab Out For [NEW-2021] CheckPoint Exam
156-915.80 Exam Dumps PDF Guaranteed Success with Accurate & Updated Questions
Check Point CCSE Exam Certification Details:
| Duration | 90 mins |
| Books / Training | CCSE Training |
| Exam Price | $250 (USD) |
| Passing Score | 70% |
| Sample Questions | Check Point CCSE Sample Questions |
| Exam Code | 156-915.80 |
| Number of Questions | 90 |
| Schedule Exam | Pearson VUE |
| Exam Name | Check Point Certified Security Expert (CCSE) R80 Update |
NEW QUESTION 150
What's true about Troubleshooting option in the IPS profile properties?
- A. Temporarily set all active protections to Detect
- B. Temporarily change the active protection profile to "Default_Protection"
- C. Temporarily will disable IPS kernel engine
- D. Temporarily set all protections to track (log) in SmartView Tracker
Answer: D
NEW QUESTION 151
Which of the following commands shows the status of processes?
- A. cpwd -l
- B. cpwd_admin -l
- C. cpwd admin_list
- D. cpwd_admin list
Answer: D
NEW QUESTION 152
Which file defines the fields for each object used in the file objects.C (color, num/string, default value...)?
- A. $FWDIR/conf/classes.C
- B. $FWDIR/conf/fields.C
- C. $FWDIR/conf/table.C
- D. $FWDIR/conf/scheam.C
Answer: A
NEW QUESTION 153
Which of the following is a new R80.10 Gateway feature that had not been available in R77.X and older?
- A. Limits the upload and download throughout for streaming media in the company to 1 Gbps.
- B. The rule base can be built of layers, each containing a set of the security rules. Layers are inspected in the order in which they are defined, allowing control over the rule base flow and which security functionalities take precedence.
- C. Sub Policies are sets of rules that can be created and attached to specific rules. If the rule is matched, inspection will continue in the sub policy attached to it rather than in the next rule
- D. Time object to a rule to make the rule active only during specified times.
Answer: B
Explanation:
Explanation/Reference: http://slideplayer.com/slide/12183998/
NEW QUESTION 154
VPN Tunnel Sharing can be configured with any of the options below, EXCEPT One:
- A. Host-based
- B. Gateway-based
- C. IP range based
- D. Subnet-based
Answer: C
Explanation:
VPN Tunnel Sharing provides interoperability and scalability by controlling the number of VPN tunnels created between peer Security Gateways. There are three available settings:
* One VPN tunnel per each pair of hosts
* One VPN tunnel per subnet pair
* One VPN tunnel per Security Gateway pair
Reference: https://sc1.checkpoint.com/documents/R77/CP_R77_VPN_AdminGuide/14018.htm
NEW QUESTION 155
What is the command to show SecureXL status?
- A. fwaccel status
- B. fwaccel stat
- C. fwaccel stats -m
- D. fwaccel -s
Answer: B
Explanation:
To check overall SecureXL status:
[Expert@HostName]# fwaccel stat
Reference: https://supportcenter.checkpoint.com/supportcenter/portal?
eventSubmit_doGoviewsolutiondetails=&solutionid=sk41397
NEW QUESTION 156
CPD is a core Check Point process that does all of the following EXCEPT:
- A. Policy installation
- B. SIC (Secure Internal Communication) functions
- C. AMON status pull from the Gateway
- D. Management High Availability (HA) sync
Answer: D
NEW QUESTION 157
Which Check Point software blades could be enforced under Threat Prevention profile using Check Point R80.10 SmartConsole application?
- A. Firewall, IPS, Anti-Bot, Anti-Virus, Threat Emulation
- B. IPS, Anti-Bot, Anti-Virus, Threat Emulation, Threat Extraction
- C. Firewall, IPS, Threat Emulation, Application Control
- D. IPS, Anti-Bot, URL Filtering, Application Control, Threat Emulation
Answer: B
NEW QUESTION 158
Which one of these features is NOT associated with the Check Point URL Filtering and Application Control Blade?
- A. Use UserCheck to help users understand that certain websites are against the company's security policy.
- B. Make rules to allow or block applications and Internet sites for individual applications, categories, and risk levels.
- C. Configure rules to limit the available network bandwidth for specified users or groups.
- D. Detects and blocks malware by correlating multiple detection engines before users are affected.
Answer: D
Explanation:
Use the URL Filtering and Application Control Software Blades to:
Create a Granular Policy - Make rules to allow or block applications and Internet sites for individual applications, categories, and risk levels. You can also create an HTTPS policy that enables Security Gateways to inspect HTTPS traffic and prevent security risks related to the SSL protocol.
Manage Bandwidth Consumption - Configure rules to limit the available network bandwidth for specified users or groups. You can define separate limits for uploading and downloading.
Keep Your Policies Updated - The Application Database is updated regularly, which helps you makes sure that your Internet security policy has the newest applications and website categories. Security Gateways connect to the Check Point Online Web Service to identify new social networking widgets and website categories.
Communicate with Users - UserCheck objects add flexibility to URL Filtering and Application Control and let the Security Gateways communicate with users. UserCheck helps users understand that certain websites are against the company's security policy. It also tells users about the changes in Internet policy related to websites and applications.
NEW QUESTION 159
You run cphaprob -a if. When you review the output, you find the word DOWN. What does DOWN mean?
- A. The physical interface is administratively set to DOWN.
- B. CCP pakets couldn't be sent to or didn't arrive from neighbor member.
- C. The cluster link is down.
- D. The physical interface is down.
Answer: B
NEW QUESTION 160
When running a query on your logs, to find records for user Toni with machine IP of 10.0.4.210 but exclude her tablet IP of 10.0.4.76, which of the following query syntax would you use?
- A. To** AND 10.0.4.210 NOT 10.0.4.76
- B. Ton* AND 10.0.4.210 NOT 10.0.4.75
- C. Toni? AND 10.0.4.210 NOT 10.0.4.76
- D. "Toni" AND 10.0.4.210 NOT 10.0.4.76
Answer: A
NEW QUESTION 161
In SmartEvent, what are the different types of automatic reactions that the administrator can configure?
- A. Mail, Block Source, Block Event Activity, External Script, SNMP Trap
- B. Mail, Block Source, Block Event Activity, Packet Capture, SNMP Trap
- C. Mail, Block Source, Block Destination, Block Services, SNMP Trap
- D. Mail, Block Source, Block Destination, External Script, SNMP Trap
Answer: A
Explanation:
Explanation
These are the types of Automatic Reactions:
References:
NEW QUESTION 162
When using Monitored circuit VRRP, what is a priority delta?
- A. When an interface fails the priority delta is subtracted from the priority
- B. When an interface fails the priority changes to the priority delta
- C. When an interface fails the delta claims the priority
- D. When an interface fails the priority delta decides if the other interfaces takes over
Answer: A
NEW QUESTION 163
CORRECT TEXT
Fill in the blank.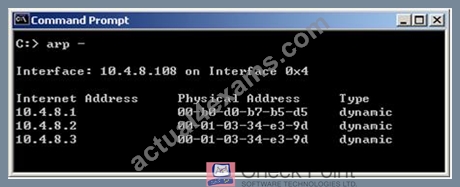
In New Mode HA, the internal cluster IP VIP address is 10.4.8.3. The internal interfaces on two members are 10.4.8.1 and 10.4.8.2 Internal host 10.4.8.108 pings 10.4.8.3, and receives replies. Review the ARP table from the internal Windows host 10.4.8.108.
According to the output, which member is the standby machine?
Answer:
Explanation:
10.4.8.1
NEW QUESTION 164
What can you do to see the current number of kernel instances in a system with CoreXL enabled?
- A. Execute command cpconfig
- B. Browse to Secure Platform Web GUI
- C. Only Check Point support personnel can access that information
- D. Execute SmarDashboard client
Answer: A
NEW QUESTION 165
When using GAiA, it might be necessary to temporarily change the MAC address of the interface eth 0 to
00:0C:29:12:34:56. After restarting the network the old MAC address should be active. How do you configure this change?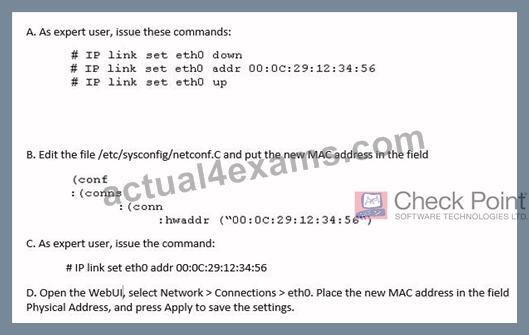
- A. Option C
- B. Option A
- C. Option B
- D. Option D
Answer: B
NEW QUESTION 166
Which is not a blade option when configuring SmartEvent?
- A. SmartEvent Server
- B. Correlation Unit
- C. Log Server
- D. SmartEvent Unit
Answer: D
Explanation:
Explanation
On the Management tab, enable these Software Blades:
* Logging & Status
* SmartEvent Server
* SmartEvent Correlation Unit
NEW QUESTION 167
......
Certification Path
The Check Point Certified Security Expert Update - R80 (CCSE) 156-915.80 Exam certification path includes only one 156-915.80 certification exam.
Get New 156-915.80 Certification Practice Test Questions Exam Dumps: https://www.actual4exams.com/156-915.80-valid-dump.html

