2022 Updated CompTIA SYO-501 Dumps PDF - Want To Pass SYO-501 Fast
SYO-501 Practice Exam Dumps - 99% Marks In CompTIA Exam
Which Skills Will You Obtain from CompTIA Security+ Certification?
You will earn 5 core skills from the Security+ certification including the following:
- Governance, risk, and compliance.
- Architecture and design;
- Attacks, threats, and vulnerabilities;
- Operations and incident response;
- Implementation;
Architecture as well as Design
This objective will determine if you understand the role of IT frameworks, secure configuration guides, and best practices. Besides, it will also emphasize the skills listed below:
- Summary of the cloud and virtualization techniques;
- The significance of secure concepts of staging deployment;
- Security implications associated with embedded systems.
- Significance of physical security controls;
- The implementation of reliable concepts of network architecture;
- The pros of using automation and resiliency methods;
- Utilizing reliable systems design;
NEW QUESTION 218
When configuring settings in a mandatory access control environment, which of the following specifies the subjects that can access specific data objects?
- A. Administrator
- B. System
- C. User
- D. Owner
Answer: A
Explanation:
Explanation
NEW QUESTION 219
A security team has downloaded a public database of the largest collection of password dumps on the Internet.
This collection contains the cleartext credentials of every major breach for the last four years. The security team pulls and compares users' credentials to the database and discovers that more than 30% of the users were still using passwords discovered in this list. Which of the following would be the BEST combination to reduce the risks discovered?
- A. Group policy, password history, password encryption
- B. Password complexity, least privilege, password reuse
- C. Password length, password encryption, password complexity
- D. Password reuse, password complexity, password expiration
Answer: D
NEW QUESTION 220
The web platform team is deploying a new web application During testing, the team notices the web application is unable to create a TLS connection to the API gateway. The administrator created a firewall rule that permit TLS traffic from the web application server to the API gateway. However, the firewall logs show all traffic is being dropped. Which of the following is MOST likely causing the issue'
- A. The TLS connection is running over a non-standard port
- B. The API gateway and web server use TLS certificate pinning
- C. The web application server and API gateway cannot negotiate a TLS cipher suite
- D. The API gateway requires configuration changes to allow TLS connections from the new servers
Answer: A
NEW QUESTION 221
A help desk is troubleshooting user reports that the corporate website is presenting untrusted certificate errors to employees and customers when they visit the website. Which of the following is the MOST likely cause of this error, provided the certificate has not expired?
- A. The valid period for the certificate has passed, and a new certificate has not been issued
- B. The certificate was self signed, and the CA was not imported by employees or customers
- C. The root CA has revoked the certificate of the intermediate CA
- D. The key escrow server has blocked the certificate from being validated
Answer: C
NEW QUESTION 222
A security consultant was asked to revise the security baselines that are utilized by a large organization.
Although the company provides different platforms for its staff, including desktops, laptops, and mobile devices, the applications do not vary by platform. Which of the following should the consultant recommend?
(Select Two).
- A. Apply application whitelisting.
- B. Apply patch management on a daily basis.
- C. Apply default configurations of all operating systems
- D. Disable default accounts and/or passwords.
- E. Allow full functionality for all applications that are accessed remotely
Answer: B,D
NEW QUESTION 223
A security administrator is creating a subnet on one of the corporate firewall interfaces to use as a DMZ which is expected to accommodate at most 14 physical hosts.
Which of the following subnets would BEST meet the requirements?
- A. 192.168.0.16 255.25.255.248
- B. 192.168.0.16/28
- C. 192.168.1.50 255.255.25.240
- D. 192.168.2.32/27
Answer: B
Explanation:
Explanation
NEW QUESTION 224
An employee in the finance department receives an email, which appears to come from the Chief Financial Officer (CFO), instructing the employee to immediately wire a large sum of money to a vendor. Which of the following BEST describes the principles of social engineering used?
(Choose two.)
- A. Familiarity
- B. Scarcity
- C. Consensus
- D. Authority
- E. Urgency
Answer: D,E
NEW QUESTION 225
A security administrator has been tasked with implementing controls that meet management goals. Drag and drop the appropriate control used to accomplish the account management goal. Options may be used once or not at all.
Answer:
Explanation: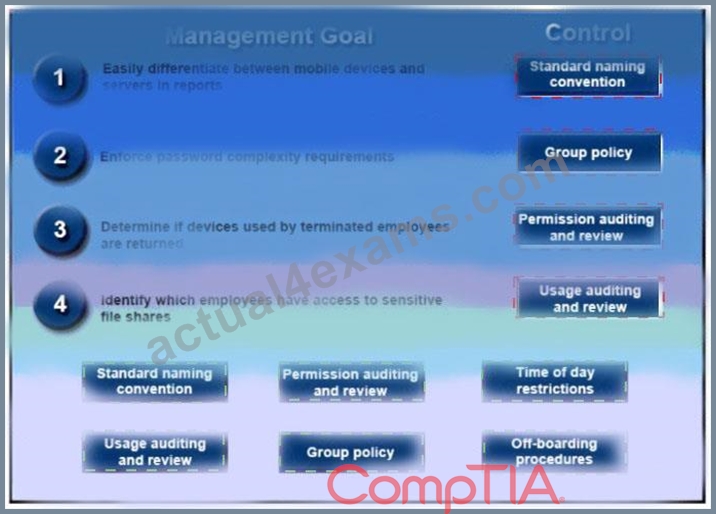
Explanation
NEW QUESTION 226
Which of the following BEST describes a security exploit for which a vendor patch is not readily available?
- A. Zero-day
- B. Race condition
- C. Integer overflow
- D. End of life
Answer: A
NEW QUESTION 227
You have been tasked with designing a security plan for your company. Drag and drop the appropriate security controls on the floor plan.
Instructions: All objects must be used and all place holders must be filled. Order does not matter. When you have completed the simulation, please select the Done button to submit.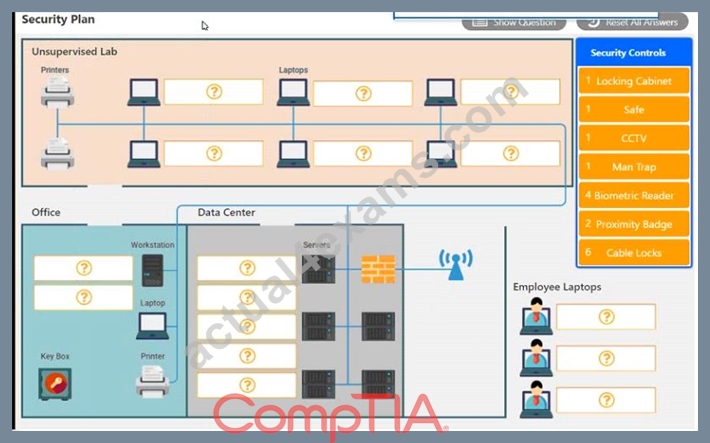
Answer:
Explanation: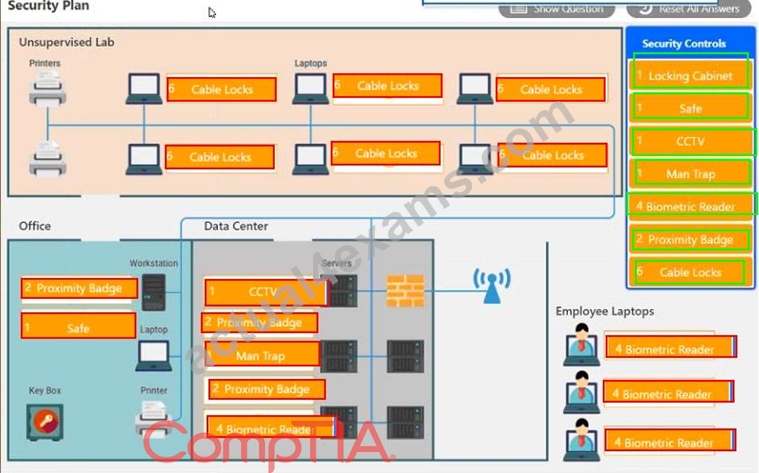
Cable locks - Adding a cable lock between a laptop and a desk prevents someone from picking it up and walking away Proximity badge + reader Safe is a hardware/physical security measure Mantrap can be used to control access to sensitive areas. CCTV can be used as video surveillance.
Biometric reader can be used to control and prevent unauthorized access. Locking cabinets can be used to protect backup media, documentation and other physical artifacts.
NEW QUESTION 228
An analyst generates the following color-coded table shown in the exhibit to help explain the risk of potential incidents in the company. The vertical axis indicates the likelihood or an incident, while the horizontal axis indicates the impact.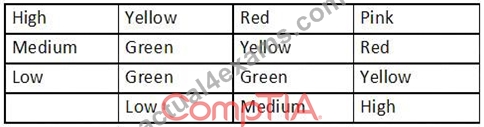
Which of the following is this table an example of?
- A. Internal threat assessment
- B. Supply chain assessment
- C. Privacy impact assessment
- D. Qualitative risk assessment
Answer: D
NEW QUESTION 229
Joe, a user at a company, clicked an email link that led to a website that infected his workstation. Joe was connected to the network, and the virus spread to the network shares. The protective measures failed to stop this virus, and it has continued to evade detection. Which of the following should a security administrator implement to protect the environment from this malware?
- A. Implement CASB to protect the network shares.
- B. Install a definition-based antivirus.
- C. Implement a heuristic behavior-detection solution.
- D. Implement an IDS/IPS.
Answer: D
NEW QUESTION 230
Which of the following delineates why it is important to perform egress filtering and monitoring on Internet connected security zones of interfaces on a firewall?
- A. Outbound traffic could be communicating to known botnet sources
- B. To prevent DDoS attacks originating from external network
- C. Egress traffic is more important than ingress traffic for malware prevention
- D. To rebalance the amount of outbound traffic and inbound traffic
Answer: D
NEW QUESTION 231
A security analyst is attempting to identify vulnerabilities in a customer's web application without impacting the system or its data.
Which of the following BEST describes the vulnerability scanning concept performed?
- A. Non-credentialed scan
- B. Compliance scan
- C. Aggressive scan
- D. Passive scan
Answer: D
Explanation:
Passive scanning is a method of vulnerability detection that relies on information gleaned from network data that is captured from a target computer without direct interaction.
Packet sniffing applications can be used for passive scanning to reveal information such as operating system, known protocols running on non-standard ports and active network applications with known bugs. Passive scanning may be conducted by a network administrator scanning for security vulnerabilities or by an intruder as a preliminary to an active attack.
For an intruder, passive scanning's main advantage is that it does not leave a trail that could alert users or administrators to their activities. For an administrator, the main advantage is that it doesn't risk causing undesired behavior on the target computer, such as freezes. Because of these advantages, passive scanning need not be limited to a narrow time frame to minimize risk or disruption, which means that it is likely to return more information.
Passive scanning does have limitations. It is not as complete in detail as active vulnerability scanning and cannot detect any applications that are not currently sending out traffic; nor can it distinguish false information put out for obfuscation.
NEW QUESTION 232
During a routine check, a security analyst discovered the script responsible for the backup of the corporate file server had been changed to the following.
Which of the following BEST describes the type of malware the analyst discovered?
- A. Rootkit
- B. RAT
- C. Key logger
- D. Logic bomb
Answer: D
NEW QUESTION 233
......
Updated Verified SYO-501 Q&As - Pass Guarantee: https://www.actual4exams.com/SYO-501-valid-dump.html
SYO-501 Certification with Actual Questions: https://drive.google.com/open?id=1fqSL6wSO7XZ-eMTD3AKl_EwVndMPp2_T

