Get Latest [Oct-2021] Conduct effective penetration tests using Actual4Exams 200-201
Penetration testers simulate 200-201 exam PDF
NEW QUESTION 103
What is an example of social engineering attacks?
- A. receiving an invitation to the department's weekly WebEx meeting
- B. receiving an email from human resources requesting a visit to their secure website to update contact information
- C. receiving an unexpected email from an unknown person with an attachment from someone in the same company
- D. sending a verbal request to an administrator who knows how to change an account password
Answer: D
NEW QUESTION 104
What is a benefit of agent-based protection when compared to agentless protection?
- A. It collects and detects all traffic locally
- B. It manages numerous devices simultaneously
- C. It lowers maintenance costs
- D. It provides a centralized platform
Answer: D
NEW QUESTION 105
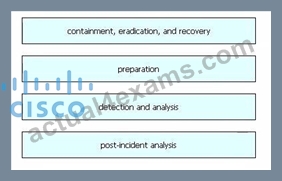
Drag and drop the elements from the left into the correct order for incident handling on the right.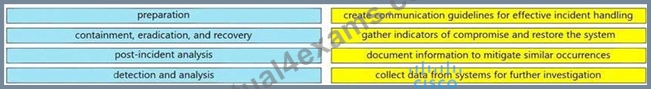
Answer:
Explanation:
NEW QUESTION 106
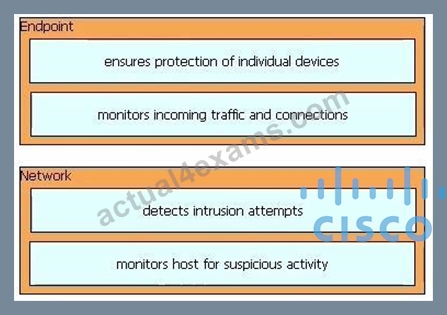
Drag and drop the uses on the left onto the type of security system on the right.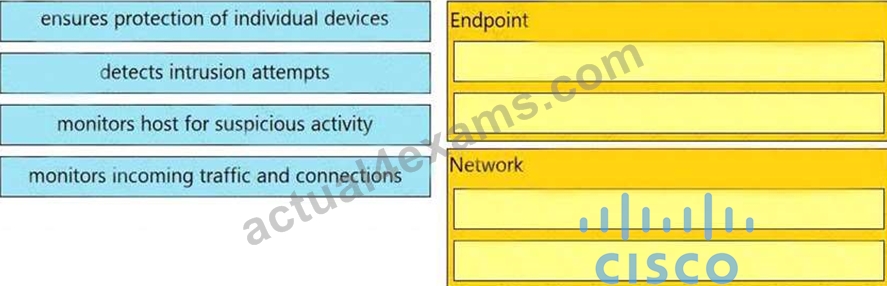
Answer:
Explanation: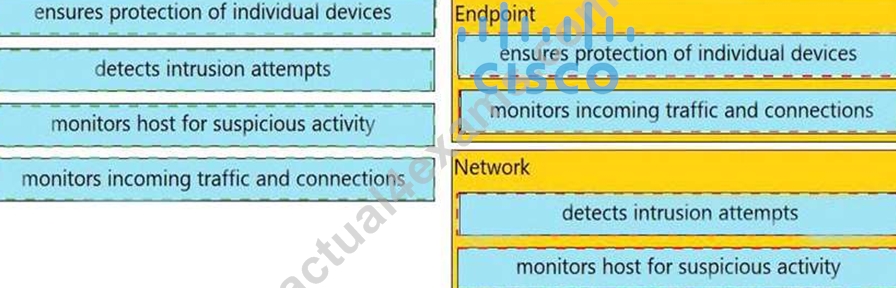
NEW QUESTION 107
Refer to the exhibit.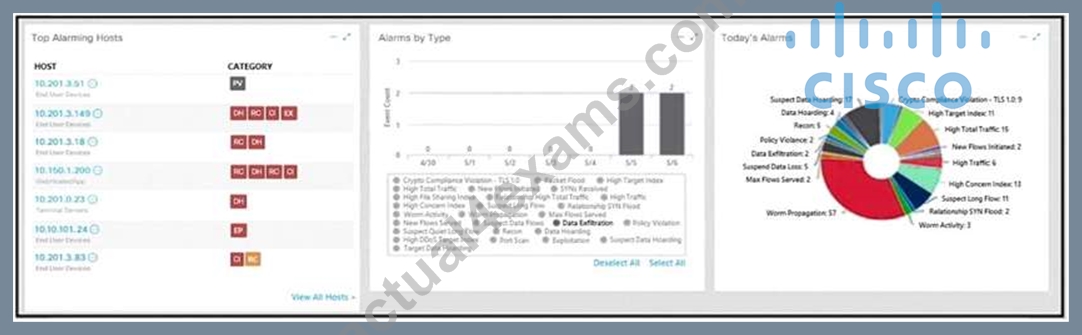
What is the potential threat identified in this Stealthwatch dashboard?
- A. A policy violation is active for host 10.201.3.149.
- B. A host on the network is sending a DDoS attack to another inside host.
- C. A policy violation is active for host 10.10.101.24.
- D. There are two active data exfiltration alerts.
Answer: D
NEW QUESTION 108
Why is encryption challenging to security monitoring?
- A. Encryption introduces larger packet sizes to analyze and store.
- B. Encryption analysis is used by attackers to monitor VPN tunnels.
- C. Encryption introduces additional processing requirements by the CPU.
- D. Encryption is used by threat actors as a method of evasion and obfuscation.
Answer: D
Explanation:
Section: Security Concepts
NEW QUESTION 109
DRAG DROP
Drag and drop the technology on the left onto the data type the technology provides on the right.
Select and Place:
Answer:
Explanation: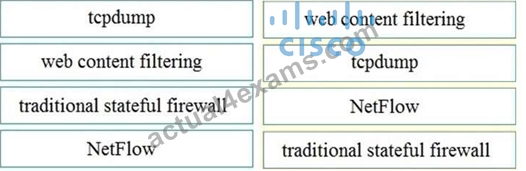
NEW QUESTION 110
Which signature impacts network traffic by causing legitimate traffic to be blocked?
- A. true negative
- B. true positive
- C. false positive
- D. false negative
Answer: C
NEW QUESTION 111
What is the difference between deep packet inspection and stateful inspection?
- A. Stateful inspection verifies contents at Layer 4 and deep packet inspection verifies connection at Layer 7
- B. Stateful inspection is more secure than deep packet inspection on Layer 7
- C. Deep packet inspection is more secure than stateful inspection on Layer 4
- D. Deep packet inspection allows visibility on Layer 7 and stateful inspection allows visibility on Layer 4
Answer: D
NEW QUESTION 112
DRAG DROP
Drag and drop the security concept on the left onto the example of that concept on the right.
Select and Place: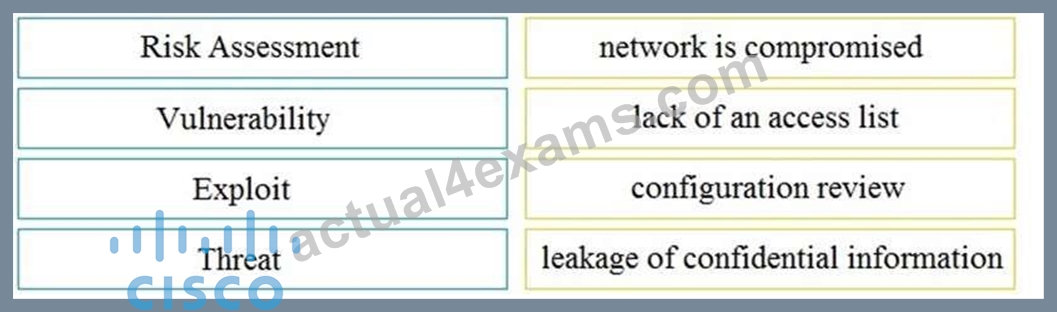
Answer:
Explanation:
NEW QUESTION 113
What is a difference between inline traffic interrogation and traffic mirroring?
- A. Traffic mirroring inspects live traffic for analysis and mitigation
- B. Traffic mirroring passes live traffic to a tool for blocking
- C. Inline inspection acts on the original traffic data flow
- D. Inline traffic copies packets for analysis and security
Answer: C
Explanation:
Explanation
Inline traffic interrogation analyzes traffic in real time and has the ability to prevent certain traffic from being forwarded Traffic mirroring doesn't pass the live traffic instead it copies traffic from one or more source ports and sends the copied traffic to one or more destinations for analysis by a network analyzer or other monitoring device
NEW QUESTION 114
What is the impact of false positive alerts on business compared to true positive?
- A. False positives alerts are manually ignored signatures to avoid warnings that are already acknowledged, while true positives are warnings that are not yet acknowledged.
- B. True positives affect security as no alarm is raised when an attack has taken place, while false positives are alerts raised appropriately to detect and further mitigate them.
- C. False-positive alerts are detected by confusion as potential attacks, while true positives are attack attempts identified appropriately.
- D. True-positive alerts are blocked by mistake as potential attacks, while False-positives are actual attacks Identified as harmless.
Answer: C
NEW QUESTION 115
A security incident occurred with the potential of impacting business services. Who performs the attack?
- A. threat actor
- B. bug bounty hunter
- C. direct competitor
- D. malware author
Answer: D
NEW QUESTION 116
What should a security analyst consider when comparing inline traffic interrogation with traffic tapping to determine which approach to use in the network?
- A. Tapping interrogations detect and block malicious traffic
- B. Inline interrogation enables viewing a copy of traffic to ensure traffic is in compliance with security policies
- C. Tapping interrogation replicates signals to a separate port for analyzing traffic
- D. Inline interrogation detects malicious traffic but does not block the traffic
Answer: C
NEW QUESTION 117
Which incidence response step includes identifying all hosts affected by an attack?
- A. preparation
- B. post-incident activity
- C. containment, eradication, and recovery
- D. detection and analysis
Answer: C
Explanation:
Section: Security Policies and Procedures
NEW QUESTION 118
Which event is user interaction?
- A. executing remote code
- B. opening a malicious file
- C. reading and writing file permission
- D. gaining root access
Answer: B
NEW QUESTION 119
......
Tested Material Used To 200-201 Test Engine: https://www.actual4exams.com/200-201-valid-dump.html
Steps Necessary To Pass The 200-201 Exam: https://drive.google.com/open?id=1o6YuJsUL0-6DFtukkl7hvIISwnAtWBND

