H12-721 Exam Study Guide Free Practice Test LAST UPDATED DATE Sep 11, 2022
The New H12-721 2022 Updated Verified Study Guides & Best Courses
NEW QUESTION 15
USG5000A has an IPSEC connection to USG5000B and the "display ike sa" command was performed on USG5000A: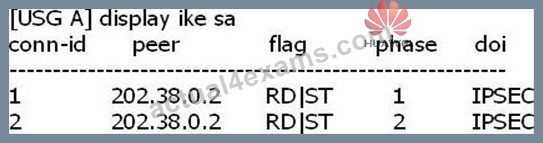
Based on the output shown, which of the following is correct?
- A. USG5000A Firewall is a secure channel initiator IKE negotiation
- B. The SA has been successfully established between the firewalls
- C. USG5000B is the initiator of IKE negotiation of safe passage
- D. The SA has not been established between the firewalls successfully.
Answer: A,B
NEW QUESTION 16
On the USG, you need to delete sslconfig.cfg in the hda1:/ directory. Which of the following commands can complete the operation?
- A. cd hda 1:/delete sslconfig.cfg
- B. cd hda 1:/mkdir sslconfig.cfg
- C. cd hda 1:/remove sslconfig.cfg
- D. cd hda 1:/rmdir sslconfig.cfg
Answer: A
NEW QUESTION 17
Which of the following circumstances where main mode IKE negotiation can not be used?
(Choose two answers)
- A. IKE in the pre-shared mode, and there is a NAT device link
- B. IKE certificate in RSA mode, and there is a NAT device link
- C. IKE in the pre-shared mode and peer identity is ID
- D. IKE in the pre-shared mode, and net exports outside the firewall dynamically assigned addresses using DHCP
Answer: A,D
NEW QUESTION 18
In the hot standby scenario, what is the correct statement about the primary and backup backups?
- A. Real-time backup is a real-time backup of newly created or refreshed data while the device is running.
- B. batch backup is to back up all information in batches after the first negotiation of two devices is completed.
- C. The backup channel must be an interface on the service board and supports GE and Eth-trunk interfaces.
- D. By default, batch backup is turned on.
Answer: A,B,C
Explanation:
Explanation
Note: The automatic backup command is enabled by default on the USG. Used in dual-system hot standby network
NEW QUESTION 19
When graphically configuring L2TP over IPSec, select an IPSec point-to-point scenario for deployment.
- A. True
- B. False
Answer: B
NEW QUESTION 20
Which of the following scenarios can achieve bandwidth reuse? (Multiple Choices)
- A. Multiple bandwidth policies reference bandwidth channels in a policy-only manner, bandwidth reuse can be implemented among multiple traffic matching bandwidth policies.
- B. Multiple traffic matches to the same bandwidth policy, bandwidth reuse can be implemented between multiple traffic.
- C. When multiple bandwidth policies reference bandwidth channels in a policy-sharing manner, bandwidth reuse can be implemented among multiple traffic matching bandwidth policies.
- D. Bandwidth reuse can be implemented between multiple traffic matching multiple sub-policies in a parent-child policy.
Answer: B,C,D
NEW QUESTION 21
Which attack method is CC attack?
- A. malformed packet attack
- B. denial of service attack
- C. scan snooping attack
- D. System-based vulnerability attacks
Answer: B
NEW QUESTION 22
The HRP technology can implement the standby firewall without any configuration information. All the configuration information is synchronized by the main firewall to the standby firewall through HRP, and the configuration information is not lost after the restart.
- A. FALSE
- B. TRUE
Answer: A
NEW QUESTION 23
Logging session log NAT / ASPF generated DPI traffic monitoring logs. Logs for this type provide a "binary" output mode. Using binary output can greatly reduce the impact on system performance but the use of binary form output requires supporting eLog log management system.
- A. TRUE
- B. FALSE
Answer: A
NEW QUESTION 24
Which of the following option do not belong to the intelligent routing way?
- A. Route selection based on ISP
- B. Route Selection Based on Link Quality
- C. Route Selection Based on Global Routing Policy
- D. Route selection based on policy routing
Answer: B
NEW QUESTION 25
To prevent applications such as Email and ERP from being affected during normal business hours, an enterprise wants the minimum bandwidth available for such traffic to be at least 60 Mbps.
Which of the following configuration meets the requirements?
- A. time-range work_time period-range 09: 00: 00 to 18: 00: 00 working-day traffic-policy profile profile_email bandwidth maximum-bandwidth whole both 60000 rule name policy_email source-zone trust destination-zone untrust application app LotusNotes application app OWA time-range work_time action qos profile profile_email
- B. time-range work_time period-range 09: 00: 00 to 18: 00: 00 working-day traffic-policy profile profile_email bandwidth guaranteed-bandwidth whole both 60000 rule name policy_email source-zone trust destination-zone untrust application app LotusNotes application app OWA time-range work_time action qos profile profile_email
- C. time-range work_time period-range 00: 00: 00 to 09: 00: 00 working-day traffic-policy profile profile_email bandwidth guaranteed-bandwidth whole both 60000 rule name policy_email source-zone trust destination-zone untrust application app LotusNotes application app OWA time-range work_time action qos profile profile_email
- D. time-range work_time period-range 09: 00: 00 to 18: 00: 00 working-day traffic-policy profile profile_email bandwidth guaranteed-bandwidth whole both 60000 rule name policy_email source-zone trust destination-zone untrust application app BT application app YouKu time-range work_time action qos profile profile_email
Answer: B
NEW QUESTION 26
USG device can be factory reset by holding down the Reset button for 1-3 seconds to recover the console password.
- A. FALSE
- B. TRUE
Answer: A
NEW QUESTION 27
In the networking environment of dual-system hot backup and IP-Link linkage (as shown in the following figure), in the configuration of the active firewall, which of the following is the configuration for the linkage between IP-Link and hot standby?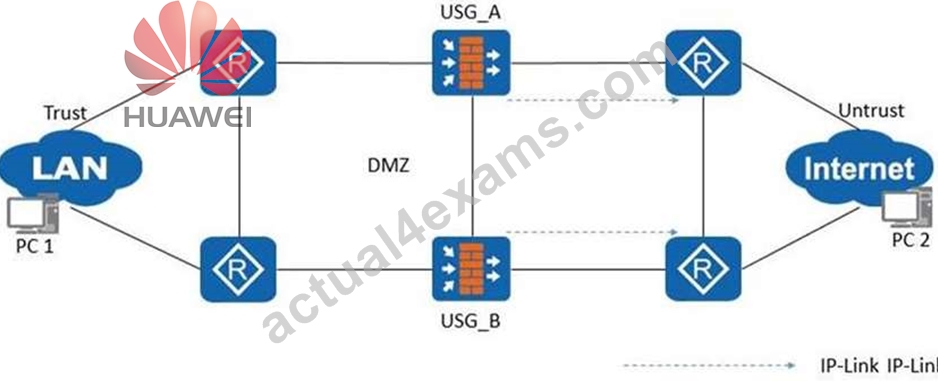
- A. hrp mirror IP-Link 1
- B. IP-Link check enable
- C. hrp track IP-Link 1 enable
- D. hrp track IP-Link 1
Answer: D
NEW QUESTION 28
Is the correct statement about TCP proxy and TCP reverse source probing?
- A. TCP proxy and TCP reverse source probe can prevent SYN Flood
- B. The principle of the TCP proxy is that the device acts as a proxy for the TCP connection between the two ends. When one end initiates the connection, it must first complete the TCP 3 handshake with the device.
- C. Use TCP proxy mode for attack defense, you must enable the state detection mechanism.
- D. TCP reverse source detection detects the source IP by sending a Reset packet.
Answer: A,B,C
Explanation:
Explanation
Note: TCP reverse source detection principle, when the device receives a SYN message, it will detect the existence of the source IP. The TCP reverse source detects the SYN-ACK sequence number that is sent incorrectly. If the source exists, it will send an RST message to request a three-way handshake. Because the reverse source detection mechanism is not affected by the successful establishment of the session table, it is recommended to use the reverse source detection technology to defend against SYN flood attacks. If you use TCP proxy attack defense, you must enable the state detection mechanism.
NEW QUESTION 29
When using the SSL VPN client to start the network extension, the prompt "Connection gateway failed", what are the possible reasons for the failure?
- A. The route between the B PC and the virtual gateway is unreachable.
- B. username and password are incorrectly configured
- C. If the proxy server is used, the proxy server settings of the network extension client are incorrect.
- D. TCP connection between the network extension client and the virtual gateway is blocked by the firewall
Answer: A,C,D
NEW QUESTION 30
The following figure shows the data packets captured during the pre-shared key mode master mode exchange process in the first phase of IKE V1. Which packet is captured below?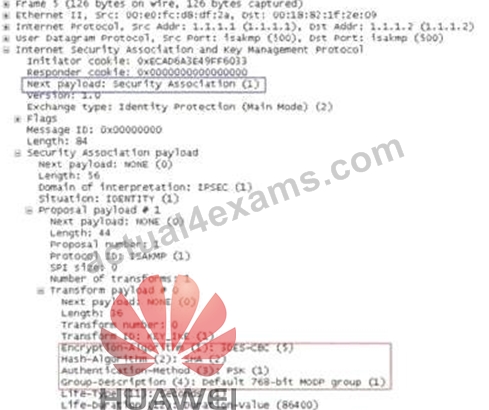
- A. IKE third message or fourth message
- B. IKE seventh message or eighth message
- C. IKE first message or second message
- D. IKE fifth message or sixth message
Answer: C
NEW QUESTION 31
To ensure the normal forwarding of large traffic, a network administrator of a company uses two firewalls to implement hot standby. As shown in the following figure, when the configuration is complete, it is found that when A of the two firewalls fails, the data stream being transmitted before the fault has been seriously lost, but the newly transmitted data stream can work normally after the fault. What could be the cause of this phenomenon?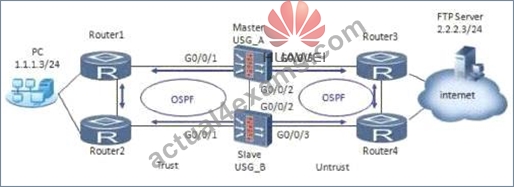
- A. The session fast backup function is not configured on the USG. The packets cannot be forwarded normally if the back and forth paths are inconsistent.
- B. is not configured to adjust the COST value of OSPF according to the HRP status.
- C. The HRP preemption time configured on the firewall is smaller than the convergence time of OSPF.
- D. does not enable hrp track on the upstream and downstream interfaces of the firewall.
Answer: D
NEW QUESTION 32
BFD static route topology is shown in Figure A.
On the firewall, administrator needs to do the following configuration:
[USG9000_A] bfd
[USG9000_A-bfd] quit
[USG9000_A] bfd aa bind peer-ip 1.1.1.2
[USG9000_A-bfd-session-aa] discriminator local 10
[USG9000_A-bfd-session-aa] discriminator remote 20
Which of the following commands should be added to the firewall configuration to achieve BFD for static route? (Choose two answers)
- A. [USG9000_A] ip route-static 0.0.0.0 0 1.1.1.2 bind bfd-session aa
- B. [USG9000_A] ip route-static 0.0.0.0 0 1.1.1.2 track bfd-session aa
- C. [USG9000_A] bfd aa bind local-ip 1.1.1.1
- D. [USG9000_A-bfd-session-aa] commit
Answer: B,D
NEW QUESTION 33
The IP-MAC address binding configuration is as follows:
[USG] firewall mac-binding 202.169.168.1 00e0-fc00-0100
When the data packets travel through the Huawei firewall device, and other strategies such as packet filtering, attack prevention are not considered, the following data ttravels hrough the firewall device? (Choose two answers)
- A. Packet source IP: 202.1.1.1
Packet source MAC: 00e0-fc11-1111 - B. Packet source IP: 202.169.168.1
Packet source MAC: 00e0-fc00-0100 - C. Packet source IP: 202.169.168.2
Packet source MAC: 00e0-fc00-0100 - D. Packet source IP: 202.169.168.1
Packet source MAC: FFFF-FFFF-FFFF
Answer: A,B
NEW QUESTION 34
......
Huawei H12-721 Exam Syllabus Topics:
| Topic | Details |
|---|---|
| Topic 1 |
|
| Topic 2 |
|
| Topic 3 |
|
| Topic 4 |
|
| Topic 5 |
|
| Topic 6 |
|
Get Prepared for Your H12-721 Exam With Actual 180 Questions: https://www.actual4exams.com/H12-721-valid-dump.html

