[Nov-2023] SPLK-1003 Dumps are Available for Instant Access using Actual4Exams
SPLK-1003 Dumps 2023 - New Splunk SPLK-1003 Exam Questions
Certification Path for Splunk Enterprise Certified Admin
The Splunk Enterprise Data Administration course targets administrators who are responsible for getting data into Splunk. It is recommended that candidates for this certification complete the lecture, hands-on labs, and quizzes that are part of the Splunk Enterprise System Administration and Splunk Enterprise Data Administration courses in order to qualify for the certification exam. Splunk Enterprise Certified Admin is a required prerequisite to the Splunk Enterprise Certified Architect and Splunk Certified Developer certification tracks.
Splunk SPLK-1003, also known as the Splunk Enterprise Certified Admin Certification Exam, is designed for individuals who want to demonstrate their knowledge and skills in managing and administering Splunk Enterprise. Splunk Enterprise Certified Admin certification exam is ideal for IT professionals who want to advance their career in the field of data analysis and gain recognition for their expertise in Splunk technology.
To prepare for the SPLK-1003 exam, candidates can take Splunk's official training courses, which cover all the topics included in the exam. Additionally, candidates can use Splunk's documentation and online resources to gain a deeper understanding of the platform's capabilities and best practices for its administration. Practice exams and study groups can also be helpful in preparing for the exam.
NEW QUESTION # 92
Consider the following stanza in inputs.conf:
What will the value of the source filed be for events generated by this scripts input?
- A. /opt/splunk/ecc/apps/search/bin/liscer.sh
- B. liscer
- C. unknown
- D. liscer.sh
Answer: A
Explanation:
Explanation
https://docs.splunk.com/Documentation/Splunk/8.2.2/Admin/Inputsconf
-Scroll down to source = <string>
*Default: the input file path
NEW QUESTION # 93
What happens when the same username exists in Splunk as well as through LDAP?
- A. LDAP user is automatically deleted from authentication.conf
- B. Splunk settings take precedence.
- C. Splunk user is automatically deleted from authentication.conf.
- D. LDAP settings take precedence.
Answer: B
Explanation:
Reference:
Splunk platform attempts native authentication first. If authentication fails outside of a local account that doesn't exist, there is no attempt to use LDAP to log in. This is adapted from precedence of Splunk authentication schema.
NEW QUESTION # 94
Which parent directory contains the configuration files in Splunk?
- A. SSPLUNK_HOME/conf
- B. SSPLUNK_HOME/var
- C. SSPLUNK_HOME/default
- D. SSFLUNK_HOME/etc
Answer: D
Explanation:
https://docs.splunk.com/Documentation/Splunk/7.3.1/Admin/Configurationfiledirectories Section titled, Configuration file directories, states "A detailed list of settings for each configuration file is provided in the .spec file names for that configuration file. You can find the latest version of the .spec and .example files in the $SPLUNK_HOME/etc system/README folder of your Splunk Enterprise installation..."
NEW QUESTION # 95
Which of the following enables compression for universal forwarders in outputs.conf?
- A. defaultGroup=my_indexers
compressed=true
/opt/splunkforwarder/bin/splunk enable compression - B. [tcpount:my_indexers] server=mysplunk_indexer1:9997, mysplunk_indexer2:9997 decompression=false
- C.
- D. [udpout:mysplunk_indexer11]
compression=true
[tcpout]
Answer: A
Explanation:
Explanation/Reference: https://docs.splunk.com/Documentation/Splunk/7.3.1/Admin/Outputsconf
NEW QUESTION # 96
When using a directory monitor input, specific source types can be selectively overridden using which configuration file?
- A. trans forms . conf
- B. outputs . conf
- C. props . conf
- D. sourcetypes . conf
Answer: C
Explanation:
When using a directory monitor input, specific source types can be selectively overridden using the props.conf file. According to the Splunk documentation1, "You can specify a source type for data based on its input and source. Specify source type for an input. You can assign the source type for data coming from a specific input, such as /var/log/. If you use Splunk Cloud Platform, use Splunk Web to define source types. If you use Splunk Enterprise, define source types in Splunk Web or by editing the inputs.conf configuration file." However, this method is not very granular and assigns the same source type to all data from an input. To override the source type on a per-event basis, you need to use the props.conf file and the transforms.conf file2. The props.conf file contains settings that determine how the Splunk platform processes incoming data, such as how to segment events, extract fields, and assign source types2. The transforms.conf file contains settings that modify or filter event data during indexing or search time2. You can use these files to create rules that match specific patterns in the event data and assign different source types accordingly2. For example, you can create a rule that assigns a source type of apache_error to any event that contains the word "error" in the first line2.
NEW QUESTION # 97
Which of the following configuration files are used with a universal forwarder? (Choose all that apply.)
- A. monitor.conf
- B. outputs.conf
- C. forwarder.conf
- D. inputs.conf
Answer: B,D
Explanation:
Explanation/Reference: https://docs.splunk.com/Documentation/Forwarder/8.0.5/Forwarder/Configuretheuniversalforwarder
NEW QUESTION # 98
Which of the following is valid distribute search group?
A)
B)
C)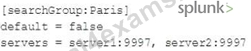
D)
- A. Option B
- B. Option C
- C. option A
- D. Option D
Answer: D
NEW QUESTION # 99
Which Splunk component does a search head primarily communicate with?
- A. Deployment server
- B. Indexer
- C. Cluster master
- D. Forwarder
Answer: B
NEW QUESTION # 100
What is required when adding a native user to Splunk? (select all that apply)
- A. Password
- B. Username
- C. Full Name
- D. Default app
Answer: A,B
NEW QUESTION # 101
Assume a file is being monitored and the data was incorrectly indexed to an exclusive index. The index is cleaned and now the data must be reindexed. What other index must be cleaned to reset the input checkpoint information for that file?
- A. _checkpoint
- B. _thefishbucket
- C. _introspection
- D. _audit
Answer: B
Explanation:
--reset Reset the fishbucket for the given key or file in the btree. Resetting the checkpoint for an active monitor input reindexes data, resulting in increased license use. https://docs.splunk.com/Documentation/Splunk/8.1.1/Troubleshooting/CommandlinetoolsforusewithSupport
NEW QUESTION # 102
Which of the following authentication types requires scripting in Splunk?
- A. ADFS
- B. RADIUS
- C. LDAP
- D. SAML
Answer: B
Explanation:
Explanation/Reference: https://answers.splunk.com/answers/131127/scripted-authentication.html
NEW QUESTION # 103
What action is required to enable forwarder management in Splunk Web?
- A. Create a server class and map it to a client in SPLUNK_HOME/etc/system/local/serverclass.conf.
- B. Navigate to Settings > Server Settings > General Settings, and set an App server port.
- C. Place an app in the SPLUNK_HOME/etc/deployment-apps directory of the deployment server.
- D. Navigate to Settings > Forwarding and receiving, and click on Enable Forwarding.
Answer: A
NEW QUESTION # 104
Which Splunk indexer operating system platform is supported when sending logs from a Windows universal forwarder?
- A. Windows platform only.
- B. Any OS platform
- C. None of the above.
- D. Linux platform only
Answer: B
NEW QUESTION # 105
User role inheritance allows what to be inherited from the parent role? (select all that apply)
- A. Search history
- B. Parents
- C. Index access
- D. Capabilities
Answer: C
NEW QUESTION # 106
Which configuration file would be used to forward the Splunk internal logs from a search head to the indexer?
- A. inputs.conf
- B. outputs.conf
- C. props.conf
- D. collections.conf
Answer: B
Explanation:
Explanation
https://docs.splunk.com/Documentation/Splunk/8.1.1/DistSearch/Forwardsearchheaddata Per the provided Splunk reference URL by @hwangho, scroll to section Forward search head data, subsection titled, 2. Configure the search head as a forwarder. "Create an outputs.conf file on the search head that configures the search head for load-balanced forwarding across the set of search peers (indexers)."
NEW QUESTION # 107
A company moves to a distributed architecture to meet the growing demand for the use of Splunk. What parameter can be configured to enable automatic load balancing in the Universal Forwarder to send data to the indexers?
- A. Splunk does not do load balancing and requires a hardware load balancer to balance traffic across the indexers.
- B. Configure the outputs . conf file to point to any server in the indexing tier and Splunk will configure the data to be sent to all of the indexers.
- C. Create one outputs . conf file for each of the server addresses in the indexing tier.
- D. Set the stanza to have a server value equal to a comma-separated list of IP addresses and indexer ports for each of the indexers in the environment.
Answer: D
Explanation:
Set the stanza to have a server value equal to a comma-separated list of IP addresses and indexer ports for each of the indexers in the environment. This is explained in the Splunk documentation1, which states:
To enable automatic load balancing, set the stanza to have a server value equal to a comma-separated list of IP addresses and indexer ports for each of the indexers in the environment. For example:
[tcpout] server=10.1.1.1:9997,10.1.1.2:9997,10.1.1.3:9997
The forwarder then distributes data across all of the indexers in the list.
NEW QUESTION # 108
You update a props.conffile while Splunk is running. You do not restart Splunk and you run this command:
splunk btool props list --debug. What will the output be?
- A. A list of props.confconfigurations as they are on-disk along with a file path from which the configuration is located.
- B. A list of the current running props.confconfigurations along with a file path from which the configuration was made.
- C. A list of all the configurations on-disk that Splunk contains.
- D. A verbose list of all configurations as they were when splunkd started.
Answer: B
Explanation:
Explanation/Reference: https://answers.splunk.com/answers/494219/need-help-with-what-should-be-a-simple- precedence.html
NEW QUESTION # 109
In case of a conflict between a whitelist and a blacklist input setting, which one is used?
- A. Whichever is entered into the configuration first.
- B. They cancel each other out.
- C. Whitelist
- D. Blacklist
Answer: D
Explanation:
Explanation
https://docs.splunk.com/Documentation/Splunk/8.0.4/Data/Whitelistorblacklistspecificincomingdata
NEW QUESTION # 110
......
Splunk SPLK-1003 Exam Practice Test Questions: https://www.actual4exams.com/SPLK-1003-valid-dump.html
Free SPLK-1003 Braindumps Download Updated: https://drive.google.com/open?id=1T4Vo2uxu9NcSGUk03LTxQfAGzJDi-blU

