[Oct 17, 2023] Download Free CompTIA 220-1102 Real Exam Questions
Pass Your Exam With 100% Verified 220-1102 Exam Questions
CompTIA A+ certification is a globally recognized and highly respected certification for IT professionals. CompTIA A+ Certification Exam: Core 2 certification is designed to validate the skills and knowledge required to perform essential IT tasks, such as troubleshooting, installation, and maintenance of hardware and software systems. CompTIA A+ Certification Exam: Core 2 certification is divided into two exams, CompTIA 220-1001 (CompTIA A+ Certification Exam: Core 1) and CompTIA 220-1002 (CompTIA A+ Certification Exam: Core 2). In this article, we will focus on the CompTIA 220-1102 (CompTIA A+ Certification Exam: Core 2).
CompTIA 220-1102 (CompTIA A+ Certification Exam: Core 2) Certification Exam is an industry-recognized certification exam that tests the skills and knowledge required to perform essential IT tasks. 220-1102 exam is part of the CompTIA A+ certification, which is one of the most widely recognized and respected IT certifications in the industry. The 220-1102 exam is designed to validate the skills necessary to install, configure, optimize, troubleshoot, repair, upgrade, and maintain PC hardware and software.
CompTIA A+ Certification Exam: Core 2 is a multiple-choice exam, with a maximum of 90 questions. 220-1102 exam duration is 90 minutes, and candidates need to score 700 out of 900 to pass the exam. 220-1102 exam is available in multiple languages, including English, Spanish, German, Japanese, and Portuguese, among others. Candidates can take the exam at any of the Pearson VUE testing centers worldwide or online through Pearson OnVUE, a proctored, online testing platform.
NEW QUESTION # 57
Which of the following Is a package management utility for PCs that are running the Linux operating system?
- A. chmod
- B. grep
- C. man
- D. yum
Answer: D
Explanation:
yum (Yellowdog Updater Modified) is a package management utility for PCs that are running the Linux operating system. It can be used to install, update and remove software packages from repositories. chmod (change mode) is a command that changes the permissions of files and directories in Linux. man (manual) is a command that displays the documentation of other commands in Linux. grep (global regular expression print) is a command that searches for patterns in text files in Linux. Verified Reference: https://www.comptia.org/blog/linux-package-management https://www.comptia.org/certifications/a
NEW QUESTION # 58
A user is unable to access several documents saved on a work PC. A technician discovers the files were corrupted and must change several system settings within Registry Editor to correct the issue. Which of the following should the technician do before modifying the registry keys?
- A. Run the PC in sate mode.
- B. Create a restore point.
- C. Update the anti-malware software.
- D. Roll back the system updates.
Answer: B
Explanation:
A restore point is a snapshot of the system settings and configuration at a specific point in time2. Creating a restore point before modifying the registry keys allows the technician to revert the system back to a previous state if something goes wrong or causes instability2. Updating the anti-malware software, running the PC in safe mode, and rolling back the system updates are not necessary steps before modifying the registry keys.
NEW QUESTION # 59
A company needs to securely dispose of data stored on optical discs. Which of the following is the MOST effective method to accomplish this task?
- A. Degaussing
- B. Shredding
- C. Low-level formatting
- D. Recycling
Answer: B
Explanation:
Explanation
Shredding is the most effective method to securely dispose of data stored on optical discs12 References: 4. How Can I Safely Destroy Sensitive Data CDs/DVDs? - How-To Geek. Retrieved from
https://www.howtogeek.com/174307/how-can-i-safely-destroy-sensitive-data-cdsdvds/ 5. Disposal - UK Data Service. Retrieved from
https://ukdataservice.ac.uk/learning-hub/research-data-management/store-your-data/disposal/
NEW QUESTION # 60
Following the latest Windows update PDF files are opening in Microsoft Edge instead of Adobe Reader. Which of the following utilities should be used to ensure all PDF files open in Adobe Reader?
- A. Network and Sharing Center
- B. Programs and Features
- C. Default Apps
- D. Add or Remove Programs
Answer: C
Explanation:
Default Apps should be used to ensure all PDF files open in Adobe Reader1
NEW QUESTION # 61
A technician removed a virus from a user's device. The user returned the device a week later with the same virus on it. Which of the following should the technician do to prevent future infections?
- A. Install the latest OS patches.
- B. Disable System Restore.
- C. Educate the end user.
- D. Clean the environment reinstallation.
Answer: C
Explanation:
Educating the end user is the best way to prevent future infections by viruses or other malware. The technician should teach the user how to avoid risky behaviors, such as opening suspicious attachments, clicking on unknown links, downloading untrusted software, etc. Disabling System Restore, installing the latest OS patches and performing a clean installation are possible ways to remove existing infections, but they do not prevent future ones. Verified Reference: https://www.comptia.org/blog/how-to-prevent-malware https://www.comptia.org/certifications/a
NEW QUESTION # 62
Which of the following Wi-Fi protocols is the MOST secure?
- A. WPA-AES
- B. WPA-TKIP
- C. WPA3
- D. WEP
Answer: C
Explanation:
Explanation
https://partners.comptia.org/docs/default-source/resources/comptia-a-220-1102-exam-objectives-(3-0)
NEW QUESTION # 63
After a company installed a new SOHO router customers were unable to access the company-hosted public website. Which of the following will MOST likely allow customers to access the website?
- A. Firmware updates
- B. Content filtering
- C. Port forwarding
- D. IP filtering
Answer: A
Explanation:
Explanation
If customers are unable to access the company-hosted public website after installing a new SOHO router, the company should check for firmware updates1. Firmware updates can fix bugs and compatibility issues that may be preventing customers from accessing the website1. The company should also ensure that the router is properly configured to allow traffic to the website . If the router is blocking traffic to the website, the company should configure the router to allow traffic to the website
NEW QUESTION # 64
An Android user reports that when attempting to open the company's proprietary mobile application it immediately doses. The user states that the issue persists, even after rebooting the phone. The application contains critical information that cannot be lost. Which of the following steps should a systems administrator attempt FIRST?
- A. Clear the application cache.
- B. Uninstall and reinstall the application
- C. Install an alternative application with similar functionality
- D. Reset the phone to factory settings
Answer: A
Explanation:
Explanation
The systems administrator should clear the application cache
If clearing the application cache does not work, the systems administrator should uninstall and reinstall the application12 Resetting the phone to factory settings is not necessary at this point12 Installing an alternative application with similar functionality is not necessary at this point12
NEW QUESTION # 65
A remote user is having issues accessing an online share. Which of the following tools would MOST likely be used to troubleshoot the Issue?
- A. Screen-sharing software
- B. Virtual private network
- C. Secure shell
- D. File transfer software
Answer: A
Explanation:
Explanation
Screen-sharing software is a tool that allows a technician to remotely view and control a user's screen over the internet. It can be used to troubleshoot issues with accessing an online share, as well as other problems that require visual inspection or guidance. Secure shell (SSH) is a protocol that allows remote access and command execution on another device, but it does not allow screen-sharing. Virtual private network (VPN) is a protocol that creates a secure tunnel between two devices over the internet, but it does not allow remote troubleshooting. File transfer software is a tool that allows transferring files between two devices over the internet, but it does not allow screen-sharing. Verified References:
https://www.comptia.org/blog/what-is-screen-sharing-software https://www.comptia.org/certifications/a
NEW QUESTION # 66
An administrator responded to an incident where an employee copied financial data to a portable hard drive and then left the company with the dat a. The administrator documented the movement of the evidence. Which of the following concepts did the administrator demonstrate?
- A. Preserving chain of custody
- B. Creating a summary of the incident
- C. Implementing data protection policies
- D. Informing law enforcement
Answer: A
Explanation:
Preserving chain of custody is a concept that refers to the documentation and tracking of who handled, accessed, modified, or transferred a piece of evidence, when, where, why, and how. Preserving chain of custody can help establish the authenticity, integrity, and reliability of the evidence, as well as prevent tampering, alteration, or loss of the evidence. An administrator who documented the movement of the evidence demonstrated the concept of preserving chain of custody. Implementing data protection policies, informing law enforcement, and creating a summary of the incident are not concepts that describe the action of documenting the movement of the evidence.
NEW QUESTION # 67
A user receives a call from someone who claims to be from the user's bank and requests information to ensure the user's account is safe. Which of the following social-engineering attacks is the user experiencing?
- A. Whaling
- B. Smishing
- C. Vishing
- D. Phishing
Answer: C
Explanation:
Explanation
The user is experiencing a vishing attack. Vishing stands for voice phishing and is a type of social-engineering attack that uses phone calls or voice messages to trick users into revealing personal or financial information. Vishing attackers often pretend to be from legitimate organizations, such as banks, government agencies or service providers, and use various tactics, such as urgency, fear or reward, to persuade users to comply with their requests. Phishing is a type of social-engineering attack that uses fraudulent emails or websites to trick users into revealing personal or financial information. Phishing does not involve phone calls or voice messages. Smishing is a type of social-engineering attack that uses text messages or SMS to trick users into revealing personal or financial information. Smishing does not involve phone calls or voice messages. Whaling is a type of social-engineering attack that targets high-profile individuals, such as executives, celebrities or politicians, to trick them into revealing personal or financial information. Whaling does not necessarily involve phone calls or voice messages. References: CompTIA A+ Core 2 (220-1002) Certification Exam Objectives Version 4.0, Domain 3.1
NEW QUESTION # 68
The command cac cor.ptia. txt was issued on a Linux terminal. Which of the following results should be expected?
- A. The contents of the text comptia. txt would be copied to another comptia. txt file
- B. The contents of the text comptia.txt will be replaced with a new blank document
- C. The contents of the text comptia. txt would be displayed.
- D. The contents of the text comptia.txt would be categorized in alphabetical order.
Answer: C
Explanation:
Explanation
The command cac cor.ptia. txt was issued on a Linux terminal. This command would display the contents of the text comptia.txt.
NEW QUESTION # 69
The command cac cor.pti
a. txt was issued on a Linux terminal. Which of the following results should be expected?
- A. The contents of the text comptia. txt would be copied to another comptia. txt file
- B. The contents of the text comptia.txt will be replaced with a new blank document
- C. The contents of the text comptia. txt would be displayed.
- D. The contents of the text comptia.txt would be categorized in alphabetical order.
Answer: C
Explanation:
The command cac cor.ptia. txt was issued on a Linux terminal. This command would display the contents of the text comptia.txt.
NEW QUESTION # 70
A customer reported that a home PC with Windows 10 installed in the default configuration is having issues loading applications after a reboot occurred in the middle of the night. Which of the following is the FIRST step in troubleshooting?
- A. Check for any installed patches and roll them back one at a time until the issue is resolved
- B. Install alternate open-source software in place of the applications with issues
- C. Reformat the hard drive, and then reinstall the newest Windows 10 release and all applications.
- D. Run both CPU and memory tests to ensure that all hardware functionality is normal
Answer: A
Explanation:
Explanation
The first step in troubleshooting is to check for any installed patches and roll them back one at a time until the issue is resolved. This can help to identify any patches that may be causing the issue and allow them to be removed.
NEW QUESTION # 71
A Windows user recently replaced a computer The user can access the public internet on the computer; however, an internal site at https7/companyintranet.com:8888 is no longer loading. Which of the following should a technician adjust to resolve the issue?
- A. Firewall settings
- B. Default gateway settings
- C. IP address settings
- D. DHCP settings
- E. Antivirus settings
Answer: A
Explanation:
Explanation
The technician should adjust the firewall settings to resolve the issue of not being able to access an internal site at https://companyintranet.com:8888. The firewall settings control how the firewall filters and allows network traffic based on rules and policies. The firewall settings may be blocking or preventing the access to the internal site by mistake or by default, especially if the site uses a non-standard port number such as 8888. The technician should check and modify the firewall settings to allow the access to the internal site or its port number. Default gateway settings determine how a computer connects to other networks or the internet.
Default gateway settings are not likely to cause the issue of not being able to access an internal site if the user can access the public internet. DHCP settings determine how a computer obtains its IP address and other network configuration parameters automatically from a DHCP server. DHCP settings are not likely to cause the issue of not being able to access an internal site if the user can access other network resources. IP address settings determine how a computer identifies itself and communicates with other devices on a network. IP address settings are not likely to cause the issue of not being able to access an internal site if the user can access other network resources. Antivirus settings control how the antivirus software scans and protects the computer from malware and threats. Antivirus settings are less likely to cause the issue of not being able to access an internal site than firewall settings, unless the antivirus software has its own firewall feature that may interfere with the network traffic. References: CompTIA A+ Core 2 (220-1002) Certification Exam Objectives Version 4.0, Domain 1.6
NEW QUESTION # 72
A network administrator is deploying a client certificate to be used for Wi-Fi access for all devices in an organization. The certificate will be used in conjunction with the user's existing username and password.
Which of the following BEST describes the security benefits realized after this deployment?
- A. All Wi-Fi traffic will be encrypted in transit.
- B. Multifactor authentication will be forced for Wi-Fi.
- C. Eavesdropping attempts will be prevented.
- D. Rogue access points will not connect.
Answer: A
Explanation:
Explanation
The security benefits realized after deploying a client certificate to be used for Wi-Fi access for all devices in an organization are that all Wi-Fi traffic will be encrypted in transit. This means that any data transmitted over the Wi-Fi network will be protected from eavesdropping attempts. Rogue access points will not connect to the network because they will not have the client certificate. However, multifactor authentication will not be forced for Wi-Fi because the client certificate is being used in conjunction with the user's existing username and password12
NEW QUESTION # 73
A developer receives the following error while trying to install virtualization software on a workstation:
VTx not supported by system
Which of the following upgrades will MOST likely fix the issue?
- A. Memory
- B. Processor
- C. Video card
- D. Hard drive
Answer: B
Explanation:
Explanation
The processor is the component that determines if the system supports virtualization technology (VTx), which is required for running virtualization software. The hard drive, memory and video card are not directly related to VTx support, although they may affect the performance of the virtual machines. Verified References:
https://www.comptia.org/blog/what-is-virtualization https://www.comptia.org/certifications/a
NEW QUESTION # 74
A technician is investigating an employee's smartphone that has the following symptoms
* The device is hot even when it is not in use.
*Applications crash, especially when others are launched
* Certain applications, such as GPS, are in portrait mode when they should be in landscape mode Which of the following can the technician do to MOST likely resolve these issues with minimal impact?
(Select TWO).
- A. Close unnecessary applications
- B. Turn on autorotation
- C. Reinstall the applications that have crashed.
- D. Perform a factory reset
- E. Update the device's operating system
- F. Activate airplane mode.
Answer: A,B
Explanation:
Explanation
The technician can close unnecessary applications and turn on autorotation to resolve these issues with minimal impact. Autorotation can help the device to switch between portrait and landscape modes automatically. Closing unnecessary applications can help to free up the device's memory and reduce the device's temperature1
NEW QUESTION # 75
Which of the following provide the BEST way to secure physical access to a data cento server room? (Select TWO).
- A. USB token
- B. Badge reader
- C. Video surveillance
- D. Biometric lock
- E. Locking rack
- F. Access control vestibule
Answer: C,D
NEW QUESTION # 76
A Windows workstation that was recently updated with approved system patches shut down instead of restarting. Upon reboot, the technician notices an alert stating the workstation has malware in the root OS folder. The technician promptly performs a System Restore and reboots the workstation, but the malware is still detected. Which of the following BEST describes why the system still has malware?
- A. The malware was installed before the system restore point was created.
- B. The system updates did not include the latest anti-malware definitions.
- C. The system restore process was compromised by the malware.
- D. A system patch disabled the antivirus protection and host firewall.
Answer: A
Explanation:
The best explanation for why the system still has malware after performing a System Restore is that the malware was installed before the system restore point was created. A system restore point is a snapshot of the system settings and configuration at a certain point in time. A System Restore is a feature that allows users to restore their system to a previous state in case of problems or errors. However, a System Restore does not affect personal files or folders, and it may not remove malware that was already present on the system before the restore point was created. A system patch disabling the antivirus protection and host firewall may increase the risk of malware infection, but it does not explain why the malware persists after a System Restore. The system updates not including the latest anti-malware definitions may reduce the effectiveness of malware detection and removal, but it does not explain why the malware persists after a System Restore. The system restore process being compromised by the malware may prevent a successful System Restore, but it does not explain why the malware persists after a System Restore. Reference: CompTIA A+ Core 2 (220-1002) Certification Exam Objectives Version 4.0, Domain 1.3
NEW QUESTION # 77
A technician needs to provide recommendations about how to upgrade backup solutions for a site in an area that has frequent hurricanes and an unstable power grid. Which of the following should the technician recommend implementing?
- A. Regionally diverse backups
- B. On-site backups
- C. High availability
- D. Incremental backups
Answer: A
Explanation:
Regionally diverse backups are backups that are stored in different geographic locations, preferably far away from the primary site1. This way, if a disaster such as a hurricane or a power outage affects one location, the backups in another location will still be available and accessible2. Regionally diverse backups can help ensure business continuity and data recovery in case of a disaster3. The other options are not the best backup solutions for a site in an area that has frequent hurricanes and an unstable power grid. High availability is a feature that allows a system to remain operational and accessible even if one or more components fail, but it does not protect against data loss or corruption4. On-site backups are backups that are stored in the same location as the primary site, which means they are vulnerable to the same disasters that can affect the primary site. Incremental backups are backups that only store the changes made since the last backup, which means they require less storage space and bandwidth, but they also depend on previous backups to restore data and may not be sufficient for disaster recovery.
NEW QUESTION # 78
A customer recently experienced a power outage at a SOHO. The customer does not think the components are connected properly. A print job continued running for several minutes after the power failed, but the customer was not able to interact with the computer. Once the UPS stopped beeping, all functioning devices also turned off. In case of a future power failure, the customer wants to have the most time available to save cloud documents and shut down the computer without losing any data.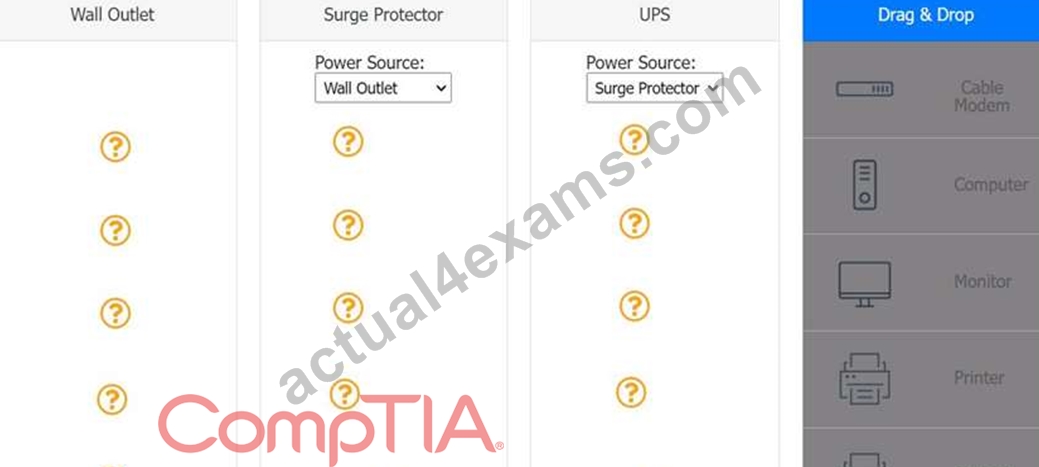
Answer:
Explanation: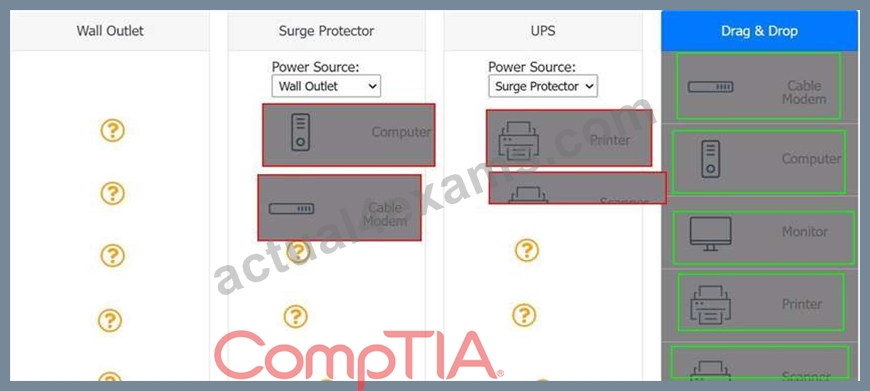
NEW QUESTION # 79
Which of the following threats will the use of a privacy screen on a computer help prevent?
- A. Whaling
- B. Impersonation
- C. Tailgating
- D. Shoulder surfing
Answer: D
Explanation:
Explanation
Shoulder surfing is a threat that involves someone looking over another person's shoulder to observe their screen, keyboard, or other sensitive information. Shoulder surfing can be used to steal passwords, personal identification numbers (PINs), credit card numbers, or other confidential data. The use of a privacy screen on a computer can help prevent shoulder surfing by limiting the viewing angle of the screen and making it harder for someone to see the screen from the side or behind. Impersonation, whaling, and tailgating are not threats that can be prevented by using a privacy screen on a computer.
NEW QUESTION # 80
A technician needs to formal a USB drive to transfer 20GB of data from a Linux computer to a Windows computer. Which of the following filesystems will the technician MOST likely use?
- A. ext4
- B. exFAT
- C. NTFS
- D. FAT32
Answer: C
NEW QUESTION # 81
......
220-1102 Dumps 100 Pass Guarantee With Latest Demo: https://www.actual4exams.com/220-1102-valid-dump.html
220-1102 Dumps PDF - 220-1102 Real Exam Questions Answers: https://drive.google.com/open?id=17mU0YC91PJhwBUZ1HnFDB7NSOUyIHKb5

