Pass CV0-002 Exam - Real Test Engine PDF with 330 Questions
Get New CV0-002 Certification Practice Test Questions Exam Dumps
How much CV0-002 Exam Cost
The price of the CV0-002 exam is $319 USD.
NEW QUESTION 77
Which of the following is a best practice used in relation to MTBF?
- A. Proactively replace components before they fail
- B. Determine backup schedule based on uptime requirements
- C. Reactively replace components after failure
- D. Determine downtime to perform a system recovery
Answer: A
NEW QUESTION 78
Which of the following cloud delivery models has the LEAST probability of data leakage?
- A. Community cloud
- B. Public cloud
- C. Private cloud
- D. Hybrid cloud
Answer: C
Explanation:
Reference:
http://ijcsmc.com/docs/papers/March2016/V5I3201699a41.pdf
NEW QUESTION 79
A company is required to ensure all access to its cloud instance for all users to utilize two-factor authentication.
The QA team confirms all functional requirements successfully test. After deployment, all business users report the two-factor authentication is not enforced while accessing the instance. Which of the following would be the MOST likely reason the QA team did not catch the issue?
- A. The business users are accessing the instance located in their country.
- B. The administrator configured to use two-factor authentication by default.
- C. The QA team only tested functional requirements.
- D. The business users are using the wrong hardware token to log in.
Answer: C
NEW QUESTION 80
A consultant is helping a gaming-as-a-service company set up a new cloud. The company recently bought several graphic card that need to be added to the servers. Which of the following should the consultant suggest as the MOST cost effective?
- A. Community
- B. Private
- C. SaaS
- D. Public
Answer: B
NEW QUESTION 81
A large finance firm processes three times as many transactions in December of each year. The transactions are processed in a private cloud. Management wants to avoid adding permanent resources to accommodate the single month increase. Which of the following is the BEST way to meet the need?
- A. Keep current capacity for processing, but implement cloud bursting to auto scale the resources without having to invest in infrastructure.
- B. Determine usage patterns over time and virtualize the processing traffic to give room for seasonal changes in resource demand.
- C. Migrate all transaction processing to a public cloud and size capacity for the largest seasonal needs.
- D. Determine usage patterns for the seasonal capacity needs and add physical resources to allow additional processing.
Answer: A
NEW QUESTION 82
The helpdesk starts receiving calls from a number of users that are suddenly having issues accessing one of the project management shared drives. When Joe, an administrator, logs onto the guest hosting the drive via the console he is able to get to the information. Which of the following failures could have caused this issue?
- A. CPU failure
- B. Disk failure
- C. NIC failure
- D. Memory failure
Answer: C
NEW QUESTION 83
A company needs to meet the security requirements for PII. Which of the following cloud service models allows the company to have the MOST control to meet the security requirements?
- A. XaaS
- B. SaaS
- C. IaaS
- D. PaaS
Answer: C
Explanation:
Reference:
https://www.omg.org/cloud/deliverables/CSCC-Cloud-Security-Standards-What-to-Expect-and- What-to-Negotiate.pdf
NEW QUESTION 84
A cloud administrator is tasked with ensuring redundancy and high availability of an IaaS cloud platform environment. The administrator is given the following requirements:
Two web servers must share the same configurations and service client connections evenly. Two database servers must share data and configurations, with only one being used at a time.
Given the above, which of the following should the administrator propose to BEST meet these requirements? (Select TWO).
- A. The availability aspect of the request does not currently exist in the IaaS cloud platform.
- B. The database server should be configured as an active-passive cluster.
- C. The web server should be configured with a load balancer with a virtual IP address.
- D. The redundancy aspect of the request does not currently exist in the IaaS cloud platform.
- E. The database server should be configured as an active-active cluster.
- F. The web server should be configured with a round-robin DNS with a CNAME record.
Answer: B,F
NEW QUESTION 85
A company wants to leverage a SaaS provider for its back-office services, and security is paramount. Which of the following solutions should a cloud engineer deploy to BEST meet the security requirements?
- A. Firewall
- B. CASB
- C. Proxy gateway
- D. IPS/IDS
Answer: B
NEW QUESTION 86
Engineers are preparing to move guests to new compute and storage infrastructure. Basic network and SAN connectivity have been established. Which of the following options are valid NEXT steps to prepare for guest migration to the new infrastructure? (Select two.)
- A. Tag the SAN trunks with the correct guest network VLANs
- B. Zone HBAs
- C. Prep mirror VMs on new hosts for data migration
- D. Tag the live migration VLAN on the trunk to the new servers
- E. Correctly size and provision NFS LUNs on the new storage
Answer: C,D
NEW QUESTION 87
A cloud administrator is required to implement a solution to handle data-at-rest encryption requirements for a database. Which of the following would BEST satisfy the requirements?
- A. Install an SSL certificate and only allow secure connections to the server.
- B. Create a virtual encrypted disk, add it to the virtual server, and have the database write to it.
- C. Activate memory encryption on the virtual server and store the certificates remotely.
- D. Enable two-factor authentication on connections to the database server and log activities.
Answer: B
Explanation:
The Question: talks about data at rest. The only option given that offers a solution for data at rest is to encrypt the disk that the database writes to.
NEW QUESTION 88
A newly established CSP allows for drive shipping to upload new data into the environment. Sensitive data on
40TB of storage needs to be transferred within one week. Which of the following is the MOST efficient and secure method for shipment of the data to the CSP with minimal downtime?
- A. Create a VPN between the sites and schedule data transfer during non-business hours.
- B. Compress and SFTP the data to the CSP.
- C. Move the data to encrypted drives and use the CSP-certified shipping provider.
- D. Copy the data to encrypted drives and use the CSP-certified shipping provider.
Answer: C
NEW QUESTION 89
The sales department is preparing to launch a high-demand product for purchase through the company's online store. The senior engineer asks the junior engineer to review the sales cloud resources to plan for a surge in online traffic: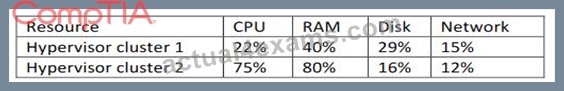
Given the metrics in the table above, which of the following resources should be adjusted to plan for future growth?
- A. Propose additional storage for cluster 1.
- B. Propose additional guests for cluster 2.
- C. Propose additional hosts for cluster 2.
- D. Propose additional memory for cluster 1.
Answer: D
NEW QUESTION 90
Company A acquires Company B.
The resources need to be added accordingly to the SaaS environment. Which of the following resources should be changed by the tenant?
- A. Compute
- B. Storage
- C. Application
- D. Users
Answer: B
NEW QUESTION 91
An administrator is deploying a new application platform with the following resource utilization: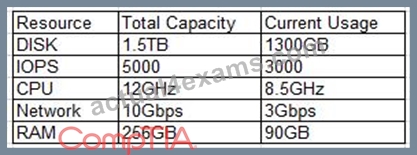
Company policy requires that no resource utilization surpasses 80%. Which of the following resources will need to be upgraded prior to deployment?
- A. Network
- B. RAM
- C. IOPS
- D. Disk
- E. CPU
Answer: D
NEW QUESTION 92
A cloud-based web proxy is blocking key sites that a business requires for operation. After validation, the sites are legitimate, and access is required for end users to complete their work.
Which of the following is the BEST solution to allow access to the sites?
- A. Whitelist the URLs.
- B. Instruct users to bypass the cloud-based web proxy.
- C. Create a security group for those users and enforce MFA.
- D. Blacklist the URLs.
Answer: A
NEW QUESTION 93
A company has implemented a change management process that allows standard changes during business hours. The company's private cloud hardware needs firmware updates and supports rolling upgrades. Which of the following considerations should be given to upgrade firmware and make the change as transparent as possible to users?
- A. Notify users before applying the change during the day.
- B. Perform the change during off-hours to minimize the impact on users.
- C. Fail the application over to perform the upgrade.
- D. Implement the change as a standard change.
Answer: A
NEW QUESTION 94
An administrator needs to build a VM for a legacy, single-threaded application. According to best practice, how many virtual CPUs should the administrator use?
- A. 0
- B. 1
- C. 2
- D. 3
Answer: B
NEW QUESTION 95
A company uses its own private cloud, which has few available resources. Mission-critical systems and other information systems are running on it. A new system will be deployed on the private cloud. The following tests are included in the test plan:
* Load test (2h)
* Backup/restore test (6h)
* Functional test (8h)
* Failover test (1h)
The work schedule of the existing system is shown below.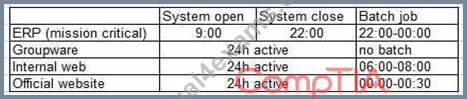
To minimize the effect to the existing system, which of the following schedules is MOST suitable for the load test?
- A. 09:00-12:00
- B. 02:00-04:00
- C. 22:00-00:00
- D. 18:00-20:00
Answer: D
NEW QUESTION 96
After monthly patching, a large number of users who are logged onto the network report that application links from a company's intranet site, which previously opened directly into the website, are now prompting for logon information. Application administrators confirm that the websites in Question: are working properly. Which of the following is the MOST likely cause of the new behavior?
- A. Account lockout
- B. Password expiration
- C. SSO issues
- D. Certificate expiration
Answer: C
NEW QUESTION 97
Several of an organization's mobile applications are hosted in a cloud environment, and the risk team requires cross-site scripting protection to ensure availability.
Which of the following is the MOST efficient security tool to implement?
- A. VPN
- B. WAF
- C. HIPS
- D. IPSec
Answer: B
NEW QUESTION 98
An e-commerce business recently experienced a two-hour outage from its hosted web service provider.
According to the SLA, the business needs to determine how much data can be restored. On which of the following service-level components should the business focus?
- A. MTTR
- B. MTBF
- C. RTO
- D. RPO
Answer: D
NEW QUESTION 99
A cloud administrator wants to make a web application on the company's private cloud available to multiple remote sites. Which of the following protocols BEST provides IP packet encapsulation?
- A. L2TP
- B. SIP
- C. GRE
- D. PPTP
Answer: C
NEW QUESTION 100
Email users report that it takes more than one minute to open emails, including those without attachments.
There are three email instances in three different regions hosted by the same CSP. Other applications hosted by the same CSP have no reported issues. Which of the following solutions BEST resolves the issue?
- A. Ensure the requested IOPS are being provided to the email instances.
- B. Check the antivirus software settings and disable real-time message scanning.
- C. Install monitoring software on the email instances.
- D. Confirm that the email instances have sufficient bandwidth.
Answer: B
NEW QUESTION 101
......
CompTIA CV0-002 Exam Syllabus Topics:
| Topic | Details |
|---|---|
| Topic 1 |
|
| Topic 2 |
|
| Topic 3 |
|
| Topic 4 |
|
| Topic 5 |
|
| Topic 6 |
|
| Topic 7 |
|
| Topic 8 |
|
| Topic 9 |
|
| Topic 10 |
|
| Topic 11 |
|
| Topic 12 |
|
| Topic 13 |
|
| Topic 14 |
|
| Topic 15 |
|
| Topic 16 |
|
| Topic 17 |
|
| Topic 18 |
|
| Topic 19 |
|
| Topic 20 |
|
| Topic 21 |
|
| Topic 22 |
|
| Topic 23 |
|
| Topic 24 |
|
CV0-002 Exam Dumps - PDF Questions and Testing Engine: https://www.actual4exams.com/CV0-002-valid-dump.html

