PCNSA Practice Dumps - Verified By Actual4Exams Updated 170 Questions
Updated PCNSA Exam Dumps - PDF Questions and Testing Engine
NEW QUESTION 18
Given the topology, which zone type should zone A and zone B to be configured with?
- A. Virtual Wire
- B. Layer2
- C. Layer3
- D. Tap
Answer: C
NEW QUESTION 19
What are three differences between security policies and security profiles? (Choose three.)
- A. Security policies are attached to security profiles
- B. Security profiles should only be used on allowed traffic
- C. Security policies can block or allow traffic
- D. Security profiles are used to block traffic by themselves
- E. Security profiles are attached to security policies
Answer: B,C,E
NEW QUESTION 20
Based on the screenshot presented which column contains the link that when clicked opens a window to display all applications matched to the policy rule?
- A. Apps Seen
- B. Service
- C. Name
- D. Apps Allowed
Answer: A
NEW QUESTION 21
What is considered best practice with regards to committing configuration changes?
- A. Disable the automatic commit feature that prioritizes content database installations before committing
- B. Validate configuration changes prior to committing
- C. Wait until all running and pending jobs are finished before committing
- D. Export configuration after each single configuration change performed
Answer: A
NEW QUESTION 22
You receive notification about new malware that infects hosts through malicious files transferred by FTP.
Which Security profile detects and protects your internal networks from this threat after you update your firewall's threat signature database?
- A. Data Filtering profile applied to outbound Security policy rules.
- B. Vulnerability Protection profile applied to outbound Security policy rules.
- C. URL Filtering profile applied to inbound Security policy rules.
- D. Antivirus profile applied to inbound Security policy rules.
Answer: D
NEW QUESTION 23
Employees are shown an application block page when they try to access YouTube. Which security policy is blocking the YouTube application?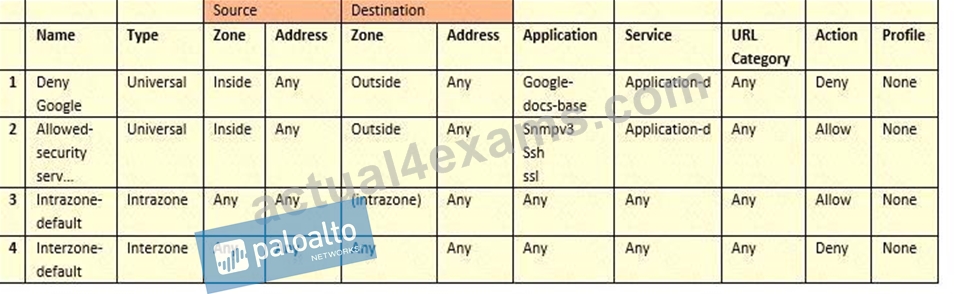
- A. Deny Google
- B. interzone-default
- C. intrazone-default
- D. allowed-security services
Answer: B
NEW QUESTION 24
At which stage of the cyber-attack lifecycle would the attacker attach an infected PDF file to an email?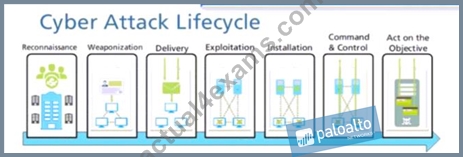
- A. explotation
- B. delivery
- C. reinsurance
- D. command and control
- E. installation
Answer: B
NEW QUESTION 25
Which license must an Administrator acquire prior to downloading Antivirus Updates for use with the firewall?
- A. Threat Environment License
- B. Threat Prevention License
- C. Threat Protection License
- D. Threat Implementation License
Answer: B
NEW QUESTION 26
Which two configuration settings shown are not the default? (Choose two.)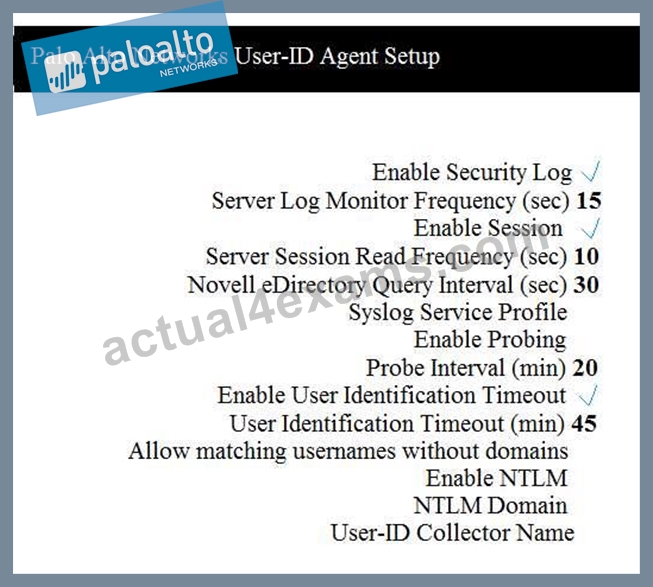
- A. Enable Probing
- B. Enable Session
- C. Server Log Monitor Frequency (sec)
- D. Enable Security Log
Answer: B,C
Explanation:
Explanation/Reference: https://docs.paloaltonetworks.com/pan-os/8-0/pan-os-web-interface-help/user-identification/device- user-identification-user-mapping/enable-server-monitoring
NEW QUESTION 27
Match the Palo Alto Networks Security Operating Platform architecture to its description.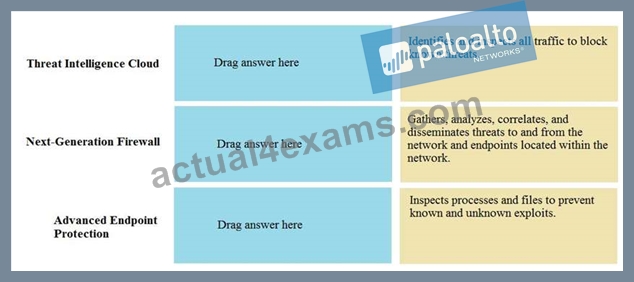
Answer:
Explanation:
Explanation:
Threat Intelligence Cloud - Gathers, analyzes, correlates, and disseminates threats to and from the network and endpoints located within the network.
Next-Generation Firewall - Identifies and inspects all traffic to block known threats Advanced Endpoint Protection - Inspects processes and files to prevent known and unknown exploits
NEW QUESTION 28
Which two configuration settings shown are not the default? (Choose two.)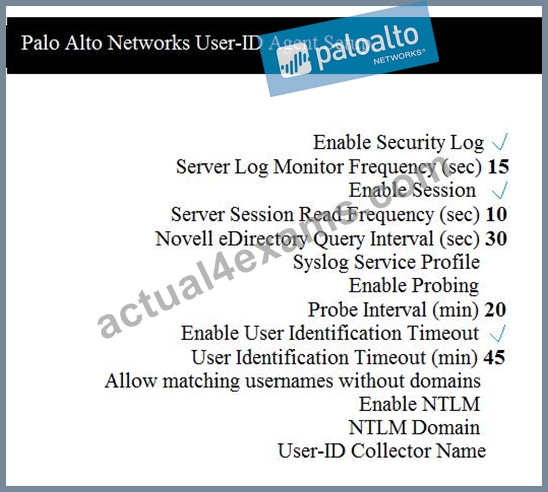
- A. Enable Probing
- B. Enable Session
- C. Server Log Monitor Frequency (sec)
- D. Enable Security Log
Answer: B,C
Explanation:
Explanation/Reference:
Reference: https://docs.paloaltonetworks.com/pan-os/8-0/pan-os-web-interface-help/user-identification/ device-user-identification-user-mapping/enable-server-monitoring
NEW QUESTION 29
Match the Cyber-Attack Lifecycle stage to its correct description.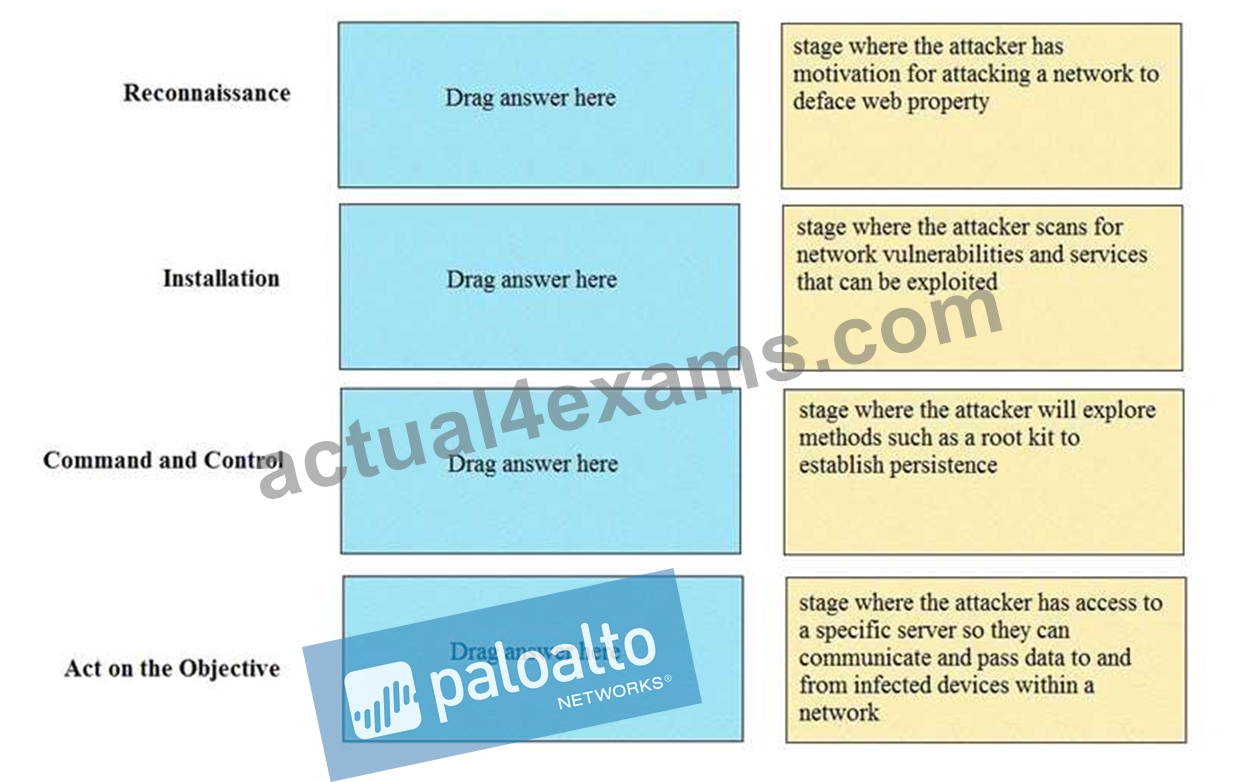
Answer:
Explanation: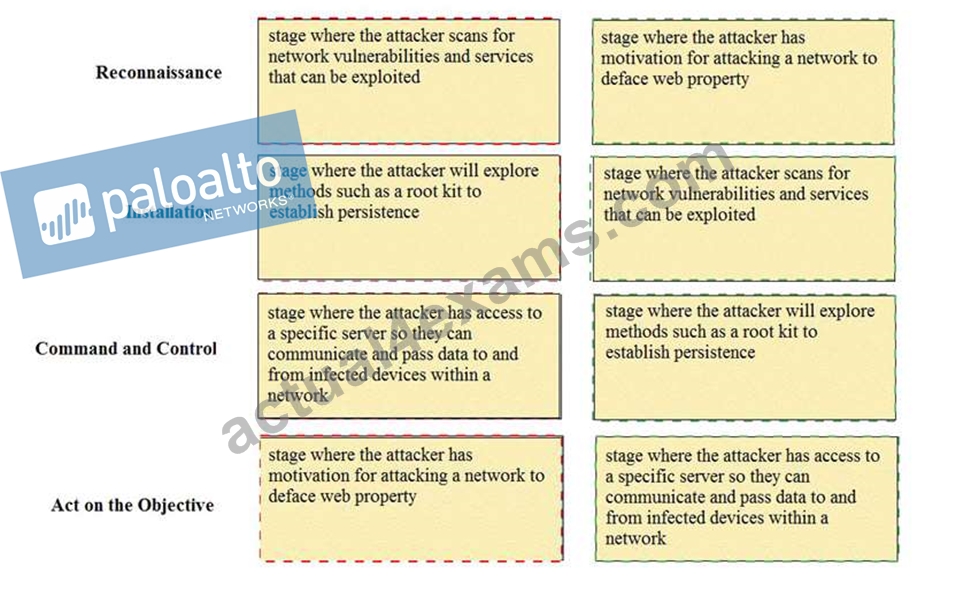
Explanation
Reconnaissance - stage where the attacker scans for network vulnerabilities and services that can be exploited.
Installation - stage where the attacker will explore methods such as a root kit to establish persistence Command and Control - stage where the attacker has access to a specific server so they can communicate and pass data to and from infected devices within a network.
Act on the Objective - stage where an attacker has motivation for attacking a network to deface web property
NEW QUESTION 30
Given the topology, which zone type should zone A and zone B to be configured with?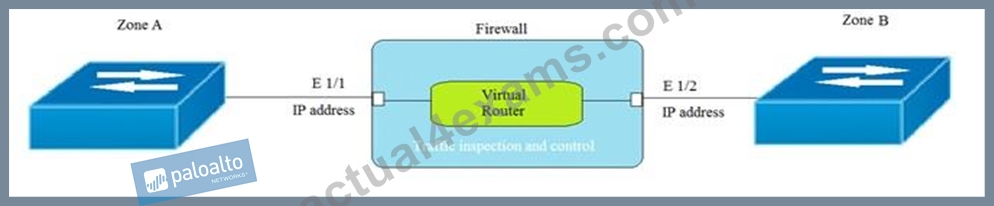
- A. Virtual Wire
- B. Layer2
- C. Layer3
- D. Tap
Answer: C
NEW QUESTION 31
What must be configured for the firewall to access multiple authentication profiles for external services to authenticate a non-local account?
- A. authentication list profile
- B. LDAP server profile
- C. authentication sequence
- D. authentication server list
Answer: C
NEW QUESTION 32
Which URL Filtering Profile action does not generate a log entry when a user attempts to access a URL?
- A. allow
- B. override
- C. block
- D. continue
Answer: A
NEW QUESTION 33
Match the Cyber-Attack Lifecycle stage to its correct description.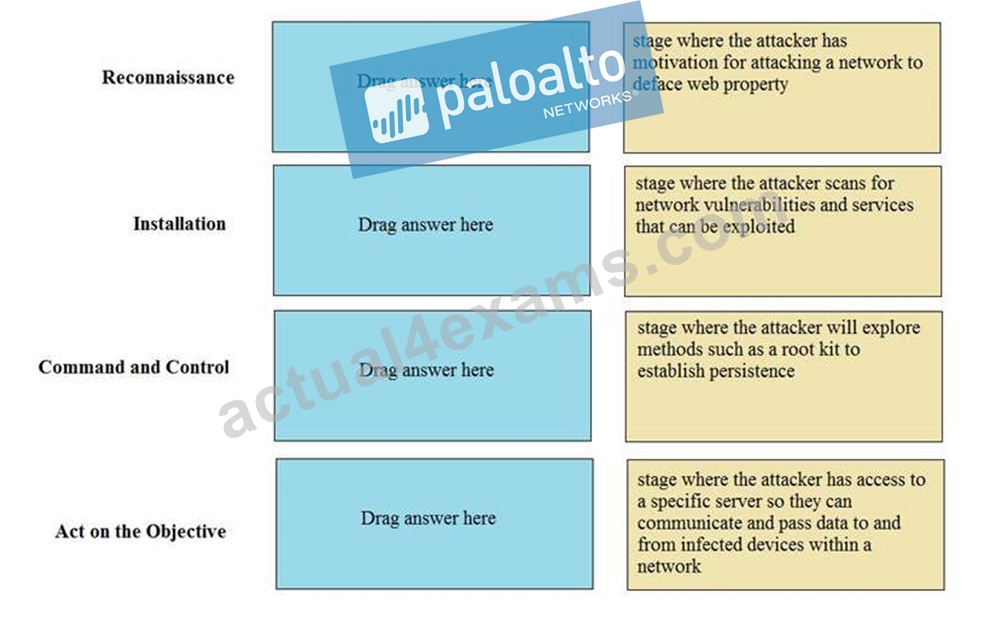
Answer:
Explanation: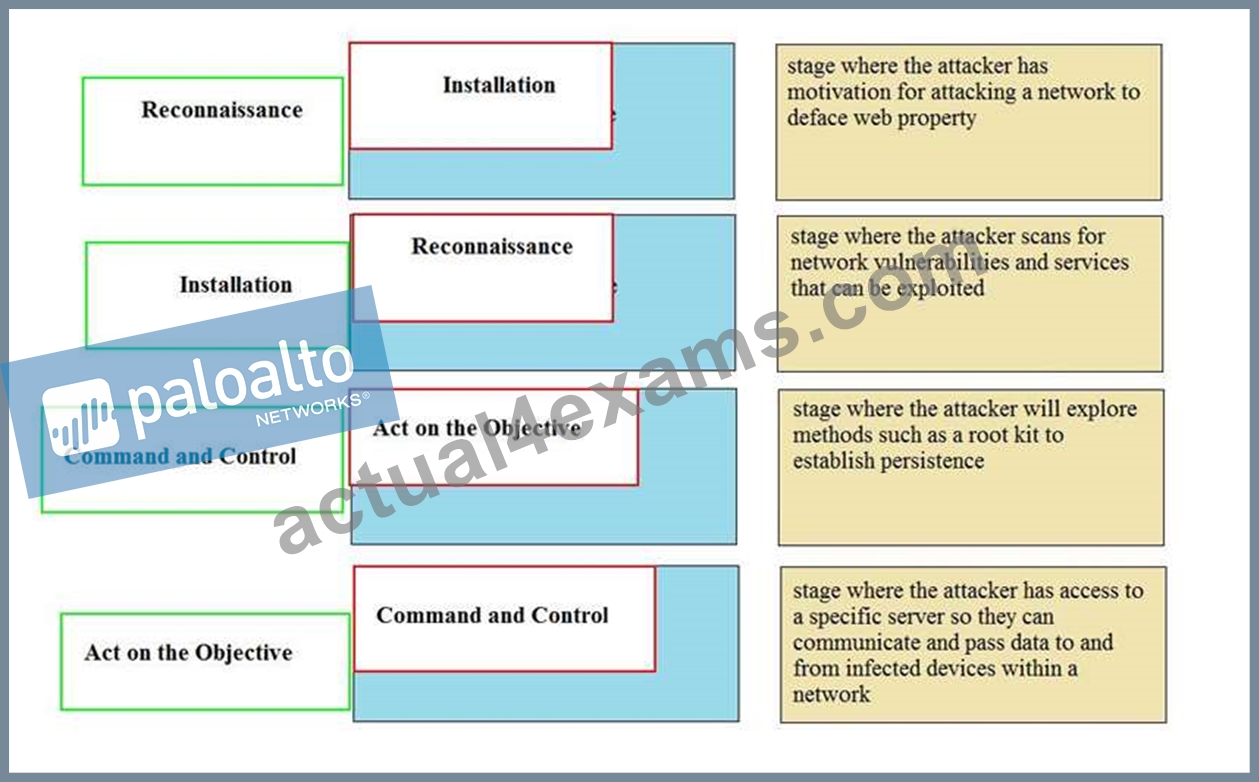
NEW QUESTION 34
Actions can be set for which two items in a URL filtering security profile? (Choose two.)
- A. Block List
- B. PAN-DB URL Categories
- C. Custom URL Categories
- D. Allow List
Answer: A,D
Explanation:
Explanation
NEW QUESTION 35
Which URL profiling action does not generate a log entry when a user attempts to access that URL?
- A. Allow
- B. Continue
- C. Override
- D. Block
Answer: A
Explanation:
References:
NEW QUESTION 36
Match the network device with the correct User-ID technology.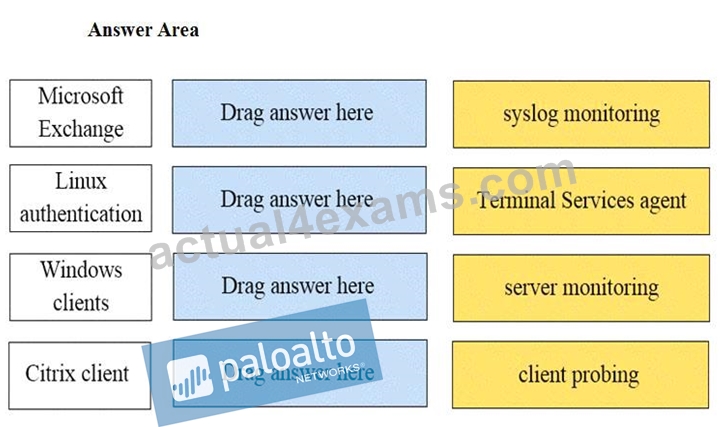
Answer:
Explanation: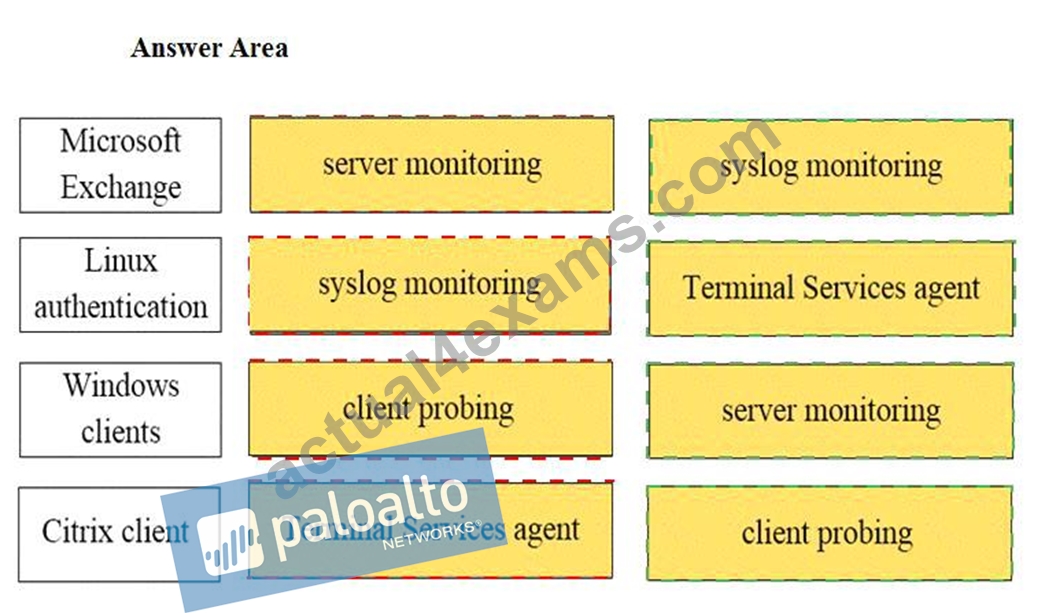
Explanation
Microsoft Exchange - Server monitoring
Linux authentication - syslog monitoring
Windows Client - client probing
Citrix client - Terminal Services agent
NEW QUESTION 37
Arrange the correct order that the URL classifications are processed within the system.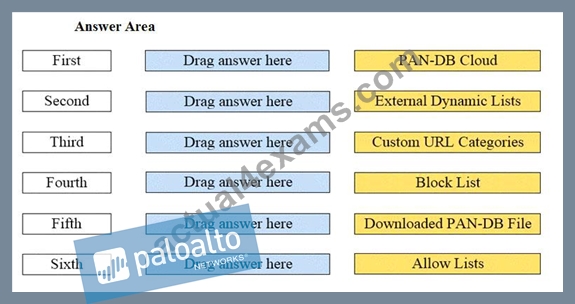
Answer:
Explanation: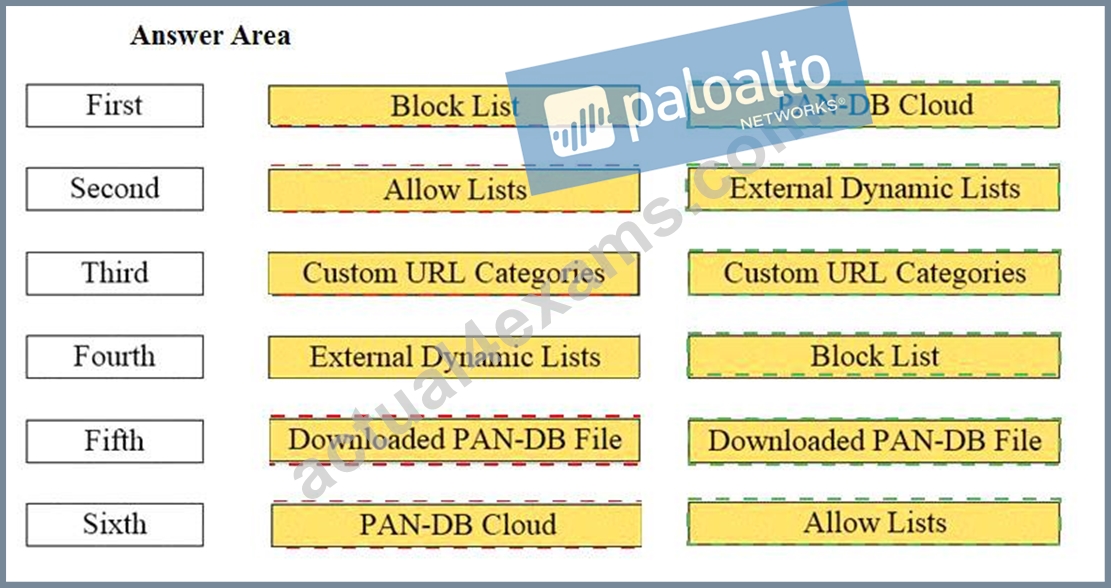
Explanation
First - Block List
Second - Allow List
Third - Custom URL Categories
Fourth - External Dynamic Lists
Fifth - Downloaded PAN-DB Files
Sixth - PAN-DB Cloud
NEW QUESTION 38
Which protocol used to map username to user groups when user-ID is configured?
- A. LDAP
- B. RADIUS
- C. TACACS+
- D. SAML
Answer: A
NEW QUESTION 39
......
Conclusion
Passing the PCNSA exam isn't much of a big deal if you prepare well and read the right resources. Remember that the PCNSA certification is only valid for two years from the date you passed the actual evaluation. It would help if you planned adequately to avert any situation that will make you an uncertified professional. If clients discover that you are posing as a certified specialist during the period of expiration, they may perceive you as a fraud. To avoid a situation like this, you should make adequate preparation to get your recertification done quickly. That way, you'll maintain a good reputation with employers of your services and get familiar with new solutions and processes within the Network and Security industry.
New (2021) Palo Alto Networks PCNSA Exam Dumps: https://www.actual4exams.com/PCNSA-valid-dump.html
Best Way To Study For Palo Alto Networks PCNSA Exam Brilliant PCNSA Exam Questions PDF: https://drive.google.com/open?id=1NUvBcqrYYXGvqGXQvG4aHrwgEiZkH-eU

