Ultimate Guide to Prepare 1V0-81.20 with Accurate PDF Questions [Dec 24, 2021]
Pass VMware With Actual4Exams Exam Dumps
NEW QUESTION 20
An organization using VMware Carbon Black makes use of an unsigned third party application that is critical to business function. Unfortunately, the application has a reputation of Potentially Unwanted Program and is prevented from running based on the policy.
What Approved list mechanism will allow this application to run in your environment while maintaining the most secure posture?
- A. Certs based
- B. SHA-256 Hash based
- C. IT Tools based
- D. MD5 Hash based
Answer: B
NEW QUESTION 21
Which parameter ensures an endpoint will stay connected with the designated VMware Carbon Black Cloud tenant?
- A. Company Code
- B. User ID
- C. Organization Group ID
- D. Device Serial Number
Answer: B
NEW QUESTION 22
In VMware Carbon Black Cloud Endpoint Standard, which items are available in the Event view?
- A. Emails, Policies, OS, Locations
- B. Hashes, Reputations
- C. Connection, IP/Port
- D. IDs, Indicators/TTPs
Answer: C
NEW QUESTION 23
Least Privilege is a common method for minimizing the risk of what kind of threat?
- A. Distributed Denial of Service
- B. Spear Phishing
- C. Insider Threats
- D. Man in the Middle
Answer: C
NEW QUESTION 24
VMware's Intrinsic Security layer includes functionality for which control points?
- A. applications, workloads, devices, identity, virtual infrastructure
- B. networks, workloads, endpoints, identity, and clouds
- C. networks, containers, devices, users, and VMware Cloud
- D. applications, users, networks, data center perimeter, vSphere
Answer: B
NEW QUESTION 25
In VMware Carbon Black Cloud, which reputations have the highest priority during analysis?
- A. Trusted Allow List
- B. Known Priority
- C. Ignore
- D. Company Allow List
Answer: A
NEW QUESTION 26
Which of the following is true about VMware Carbon Black Cloud Enterprise EDR watchlists?
- A. You cannot customize them
- B. They are made up of reports
- C. They only update annually
- D. Each watchlist is user specific
Answer: D
NEW QUESTION 27
Which is a common solution to implement for inbound network attacks?
- A. Load Balancer
- B. Firewall
- C. Reverse Proxy
- D. Proxy
Answer: B
NEW QUESTION 28
Which would require a Layer 7 Firewall?
- A. block a specific application
- B. block a specific port
- C. block a subnet range
- D. block a host
Answer: A
NEW QUESTION 29
When filtering firewall rules after selecting an object to filter by, which four columns does the filter search? (Choose four.)
- A. Action
- B. Destinations
- C. Protocol
- D. Log
- E. Services
- F. Applied To
- G. Source
Answer: B,E,F,G
NEW QUESTION 30
Which Workspace ONE feature incorporates network range, device platform, and authentication method into decision making when evaluating an access request from a user?
- A. Sensors
- B. Access Policies
- C. Compliance Policies
- D. Restriction Profiles
Answer: B
NEW QUESTION 31
Which shell command line syntax represents less suspicious danger than the others?
- A. sc create
- B. net user
- C. clear
- D. -Enc
Answer: C
NEW QUESTION 32
What is the default user's network range when creating a new access policy rule in Workspace ONE Access?
- A. 10.0.0.0/8
- B. ALL RANGES
- C. 192.168.0.0/16
- D. LOCAL SUBNET
Answer: B
NEW QUESTION 33
In a Workspace ONE deployment, Per App Tunnel uses the Native Platform API for which platforms?
- A. iOS & MacOS only
- B. iOS, Android, MacOS & Windows
- C. Android & Windows only
- D. iOS & Android only
Answer: D
NEW QUESTION 34
Micro segmentation is under which pillar of trust in VMware's 5 pillars of Zero Trust?
- A. User
- B. Session/Transport
- C. Application
- D. Device
Answer: B
NEW QUESTION 35
Which three default connectors are available in Workspace ONE Intelligence to execute automation actions? (Choose three.)
- A. ServiceNow
- B. Log Insight
- C. Workspace ONE UEM
- D. vRealize Operations Manager
- E. Slack
Answer: A,C,E
NEW QUESTION 36
Network Security teams can leverage Micro-Segmentation for which purpose?
- A. deny attackers the opportunity to move laterally within the internal network
- B. prevent a successful attack to any of the systems attached to the network
- C. replace the need to leverage traditional network segmentation
- D. deny attackers the possibility to breach the data center perimeter
Answer: A
NEW QUESTION 37
In VMware Carbon Black Cloud, which two of these statements are true of the Permissions section of the Prevention tab under Policies? (Choose two.)
- A. assigns access rights to specific individuals
- B. assigns access rights to specific applications
- C. take precedence over blocking and isolation
- D. allows specific operations or applications
- E. deny or close Applications or Actions
Answer: B,D
NEW QUESTION 38
Which three are industry best practices of Zero Trust framework? (Choose three.)
- A. Employee machines are checked for compliance before they get access to applications
- B. Employee machines on Internal network are trusted and have access to all internal resources
- C. Employees are not required to provide MFA to access internal resources over VPN
- D. Employee machines need to have a passcode profile setup
- E. Employees get access to only the required resources to get their job done
Answer: A,D,E
NEW QUESTION 39
Match each Workspace ONE Intelligence Security Risk Module tab on the left with its description on the right by dragging the tab's name into the correct box.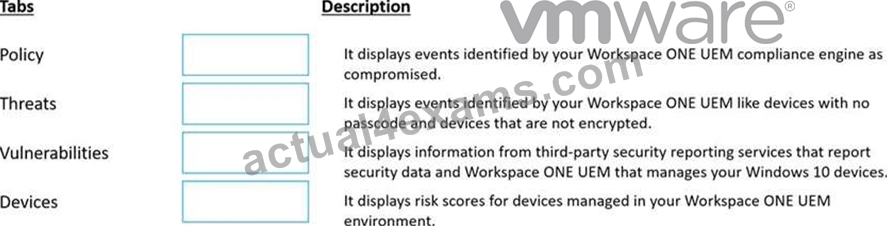
Answer:
Explanation: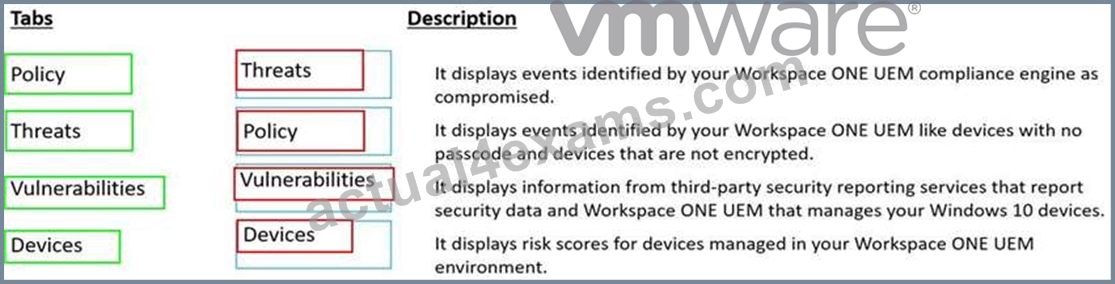
NEW QUESTION 40
......
Latest 1V0-81.20 Exam Dumps - Valid and Updated Dumps: https://www.actual4exams.com/1V0-81.20-valid-dump.html

