Full NSE6_FWB-6.4 Practice Test and 58 unique questions with explanations waiting just for you!
NSE 6 Network Security Specialist Dumps NSE6_FWB-6.4 Exam for Full Questions - Exam Study Guide
NEW QUESTION 28
Which of the following is true about Local User Accounts?
- A. Can be used for Single Sign On
- B. Can be used for site publishing
- C. Best suited for large environments with many users
- D. Must be assigned regardless of any other authentication
Answer: B
NEW QUESTION 29
Review the following configuration: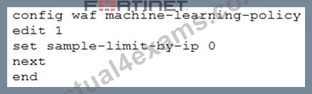
What is the expected result of this configuration setting?
- A. When machine learning (ML) is in its collecting phase, FortiWeb will not accept any samples from any source IP addresses.
- B. When machine learning (ML) is in its running phase, FortiWeb will accept a set number of samples from the same source IP address.
- C. When machine learning (ML) is in its running phase, FortiWeb will accept an unlimited number of samples from the same source IP address.
- D. When machine learning (ML) is in its collecting phase, FortiWeb will accept an unlimited number of samples from the same source IP address.
Answer: D
NEW QUESTION 30
When FortiWeb triggers a redirect action, which two HTTP codes does it send to the client to inform the browser of the new URL? (Choose two.)
- A. 0
- B. 1
- C. 2
- D. 3
Answer: C,D
NEW QUESTION 31
Which
regex expression is the correct format for redirecting the URL http://www.example.com?
- A. www\.example\.com
- B. www\example\com
- C. www.example.com
- D. www/.example/.com
Answer: C
Explanation:
Explanation
\1://www.company.com/\2/\3
NEW QUESTION 32
Refer to the exhibit.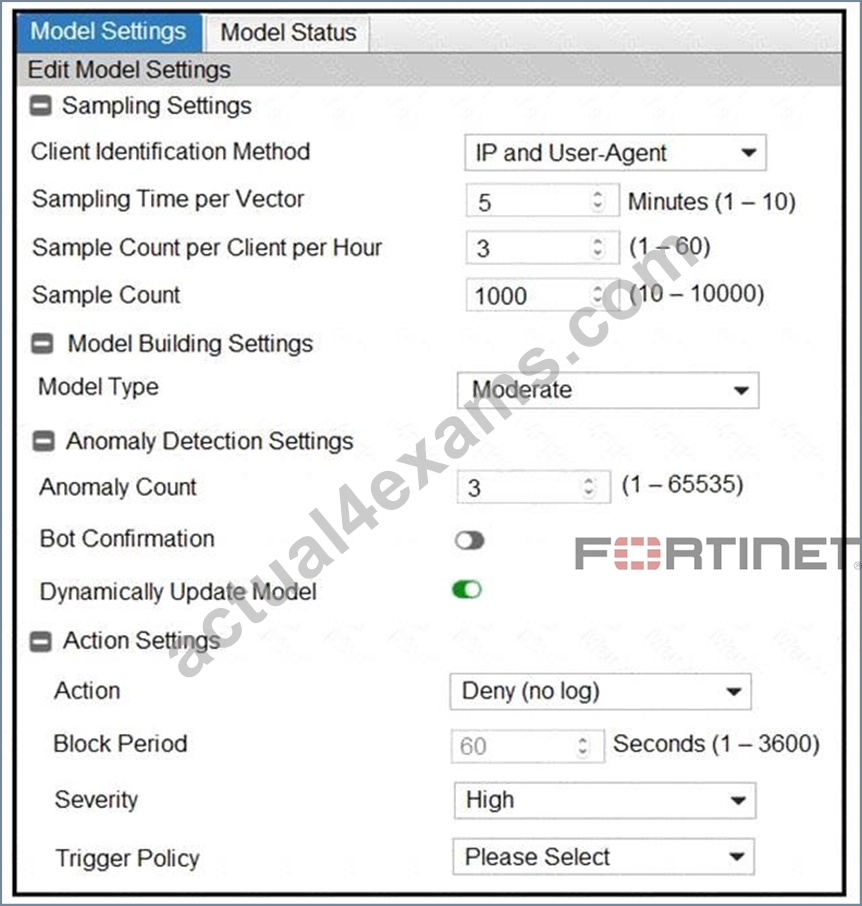
Many legitimate users are being identified as bots. FortiWeb bot detection has been configured with the settings shown in the exhibit. The FortiWeb administrator has already verified that the current model is accurate.
What can the administrator do to fix this problem, making sure that real bots are not allowed through FortiWeb?
- A. Disable Dynamically Update Model
- B. Enable Bot Confirmation
- C. Change Action under Action Settings to Alert
- D. Change Model Type to Strict
Answer: B
Explanation:
Explanation
Bot Confirmation
If the number of anomalies from a user has reached the Anomaly Count, the system executes Bot Confirmation before taking actions.
The Bot Confirmation is to confirm if the user is indeed a bot. The system sends RBE (Real Browser Enforcement) JavaScript or CAPTCHA to the client to double check if it's a real bot.
NEW QUESTION 33
How does an ADOM differ from a VDOM?
- A. ADOMs improve performance by offloading some functions.
- B. ADOMs do not have virtual networking
- C. ADOMs only affect specific functions, and do not provide full separation like VDOMs do.
- D. Allows you to have 1 administrator for multiple tenants
Answer: B
NEW QUESTION 34
What benefit does Auto Learning provide?
- A. Automatically blocks all detected threats
- B. Automatically builds rules sets
- C. FortiWeb scans all traffic without taking action and makes recommendations on rules
- D. Automatically identifies and blocks suspicious IPs
Answer: B
NEW QUESTION 35
How does FortiWeb protect against defacement attacks?
- A. It keeps a live duplicate of the database.
- B. It keeps a complete backup of all files and the database.
- C. It keeps full copies of all files and directories.
- D. It keeps hashes of files and periodically compares them to the server.
Answer: D
Explanation:
Explanation
The anti-defacement feature examines a web site's files for changes at specified time intervals. If it detects a change that could indicate a defacement attack, the FortiWeb appliance can notify you and quickly react by automatically restoring the web site contents to the previous backup.
NEW QUESTION 36
The FortiWeb machine learning (ML) feature is a two-phase analysis mechanism.
Which two functions does the first layer perform? (Choose two.)
- A. Determines whether an anomaly is a real attack or just a benign anomaly that should be ignored
- B. Builds a threat model behind every parameter and HTTP method
- C. Determines whether traffic is an anomaly, based on observed application traffic over time
- D. Determines if a detected threat is a false-positive or not
Answer: B,C
Explanation:
Explanation
The first layer uses the Hidden Markov Model (HMM) and monitors access to the application and collects data to build a mathematical model behind every parameter and HTTP method.
NEW QUESTION 37
Which would be a reason to implement HTTP rewriting?
- A. To replace a vulnerable function in the requested URL
- B. The original page has moved to a new URL
- C. The original page has moved to a new IP address
- D. To send the request to secure channel
Answer: A
Explanation:
Explanation
Create a new URL rewriting rule.
NEW QUESTION 38
Refer to the exhibit.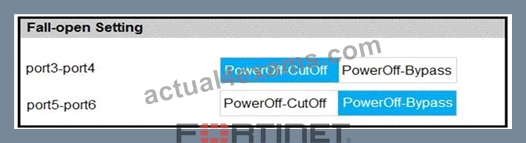
Based on the configuration, what would happen if this FortiWeb were to lose power? (Choose two.)
- A. Traffic will pass between port5 and port6 uninspected.
- B. All traffic will be interrupted.
- C. Traffic will be interrupted between port3 and port4.
- D. Traffic that passes between port5 and port6 will be inspected.
Answer: A,C
NEW QUESTION 39
Refer to the exhibit.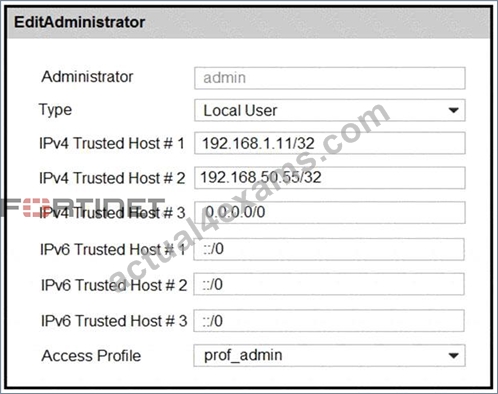
There is only one administrator account configured on FortiWeb. What must an administrator do to restrict any brute force attacks that attempt to gain access to the FortiWeb management GUI?
- A. Delete the built-in administrator user and create a new one.
- B. Configure IPv4 Trusted Host # 3 with a specific IP address.
- C. The configuration changes must be made on the upstream device.
- D. Change the Access Profile to Read_Only.
Answer: B
NEW QUESTION 40
Which algorithm is used to build mathematical models for bot detection?
- A. HCM
- B. SVN
- C. SVM
- D. HMM
Answer: C
Explanation:
Explanation
FortiWeb uses SVM (Support Vector Machine) algorithm to build up the bot detection model
NEW QUESTION 41
You are using HTTP content routing on FortiWeb. You want requests for web application A to be forwarded to a cluster of web servers, which all host the same web application. You want requests for web application B to be forwarded to a different, single web server.
Which statement about this solution is true?
- A. Static or policy-based routes are not required.
- B. You must put the single web server in to a server pool, in order to use it with HTTP content routing.
- C. The server policy applies the same protection profile to all of its protected web applications.
- D. You must chain policies so that requests for web application A go to the virtual server for policy A, and requests for web application B go to the virtual server for policy B.
Answer: A
NEW QUESTION 42
What key factor must be considered when setting brute force rate limiting and blocking?
- A. Multiple clients sharing a single Internet connection
- B. Multiple clients from geographically diverse locations
- C. Multiple clients connecting to multiple resources
- D. A single client contacting multiple resources
Answer: A
Explanation:
Explanation
https://training.fortinet.com/course/view.php?id=3363 What is one key factor that you must consider when setting brute force rate limiting and blocking? Multiple clients sharing a single Internet connection
NEW QUESTION 43
When the FortiWeb is configured in Reverse Proxy mode and the FortiGate is configured as an SNAT device, what IP address will the FortiGate's Real Server configuration point at?
- A. FortiWeb's real IP
- B. Server's real IP
- C. Virtual Server IP on the FortiGate
- D. IP Address of the Virtual Server on the FortiWeb
Answer: C
NEW QUESTION 44
You are configuring FortiAnalyzer to store logs from FortiWeb.
Which is true?
- A. FortiAnalyzer will store antivirus and DLP archives from FortiWeb.
- B. You must enable ADOMs on FortiAnalyzer.
- C. FortiWeb will query FortiAnalyzer for reports, instead of generating them locally.
- D. To store logs from FortiWeb 6.4, on FortiAnalyzer, you must select "FrotiWeb 6.1".
Answer: B
NEW QUESTION 45
Which three statements about HTTPS on FortiWeb are true? (Choose three.)
- A. For SNI, you select the certificate that FortiWeb will present in the server pool, not in the server policy.
- B. Enabling RC4 protects against the BEAST attack, but is not recommended if you configure FortiWeb to only offer TLS 1.2.
- C. In true transparent mode, the TLS session terminator is a protected web server.
- D. In transparent inspection mode, you select which certificate that FortiWeb will present in the server pool, not in the server policy.
- E. After enabling HSTS, redirects to HTTPS are no longer necessary.
Answer: B,C,D
NEW QUESTION 46
In which two operating modes can FortiWeb modify HTTP packets? (Choose two.)
- A. True transparent proxy
- B. Reverse proxy
- C. Offline protection
- D. Transparent inspection
Answer: A,B
NEW QUESTION 47
Refer to the exhibit.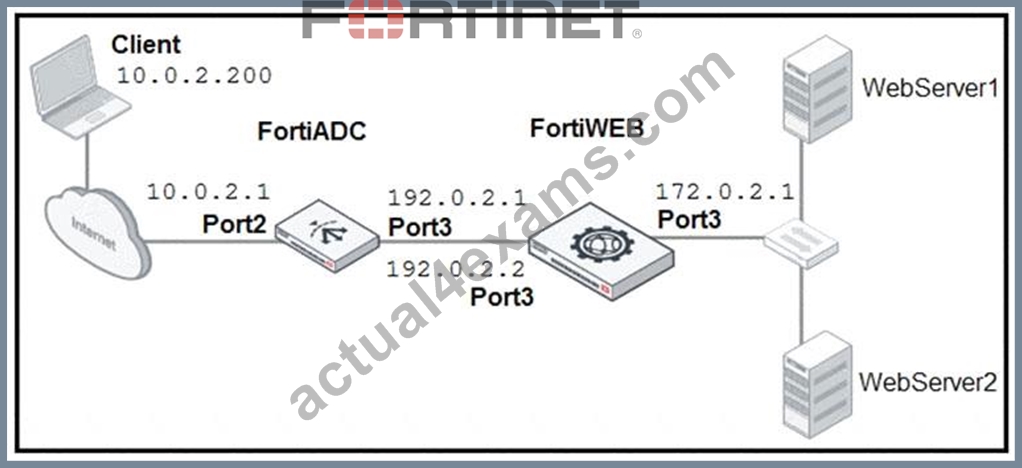
FortiADC is applying SNAT to all inbound traffic going to the servers. When an attack occurs, FortiWeb blocks traffic based on the 192.0.2.1 source IP address, which belongs to FortiADC. The setup is breaking all connectivity and genuine clients are not able to access the servers.
What must the administrator do to avoid this problem? (Choose two.)
- A. Enable the Add X-Forwarded-For setting on FortiWeb.
- B. Enable the Use X-Forwarded-For setting on FortiWeb.
- C. Place FortiWeb in front of FortiADC.
- D. No Special configuration is required; connectivity will be re-established after the set timeout.
Answer: B,C
Explanation:
Explanation
Configure your load balancer to insert or append to an X-Forwarded-For:, X-Real-IP:, or other HTTP X-header. Also configure FortiWeb to find the original attacker's or client's IP address in that HTTP header
NEW QUESTION 48
What can an administrator do if a client has been incorrectly period blocked?
- A. Manually release the ID address from the temporary blacklist.
- B. Nothing, it is not possible to override a period block.
- C. Disconnect the client from the network.
- D. Force a new IP address to the client.
Answer: A
Explanation:
Explanation
Block Period
Enter the number of seconds that you want to block the requests. The valid range is 1-3,600 seconds. The default value is 60 seconds.
This option only takes effect when you choose Period Block in Action.
Note: That's a temporary blacklist so you can manually release them from the blacklist.
NEW QUESTION 49
......
Authentic Best resources for NSE6_FWB-6.4 Online Practice Exam: https://www.actual4exams.com/NSE6_FWB-6.4-valid-dump.html
Get the superior quality NSE6_FWB-6.4 Dumps Questions from Actual4Exams: https://drive.google.com/open?id=1WstsxWDmSDh4lmhCUcXKCBawic6NICR8

