CS0-002 Free Update With 100% Exam Passing Guarantee [2021]
[Sep-2021] Verified CompTIA Exam Dumps with CS0-002 Exam Study Guide
NEW QUESTION 31
A security analyst has been alerted to several emails that snow evidence an employee is planning malicious activities that involve employee Pll on the network before leaving the organization. The security analysis BEST response would be to coordinate with the legal department and:
- A. the public relations department
- B. the human resources department
- C. law enforcement
- D. senior leadership
Answer: B
NEW QUESTION 32
A security analyst is investigating a malware infection that occurred on a Windows system. The system was not connected to a network and had no wireless capability Company policy prohibits using portable media or mobile storage The security analyst is trying to determine which user caused the malware to get onto the system Which of the following registry keys would MOST likely have this information?
A)
B)
C)
D)
- A. Option D
- B. Option C
- C. Option A
- D. Option B
Answer: B
NEW QUESTION 33
Hotspot Question
Welcome to the Enterprise Help Desk System. Please work the ticket escalated to you in the desk ticket queue.
INSTRUCTIONS
Click on me ticket to see the ticket details Additional content is available on tabs within the ticket First, select the appropriate issue from the drop-down menu. Then, select the MOST likely root cause from second drop-down menu If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.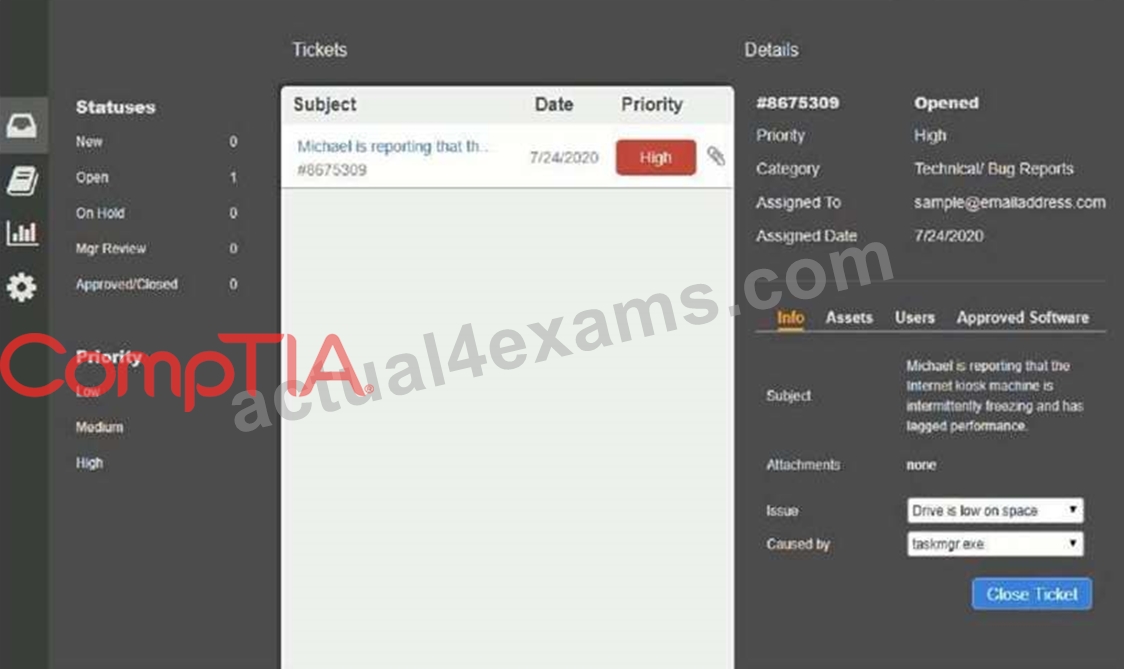
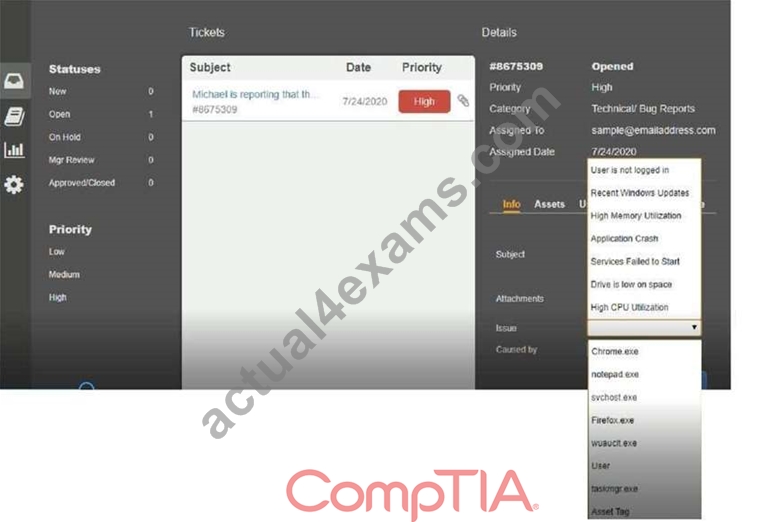
Answer:
Explanation: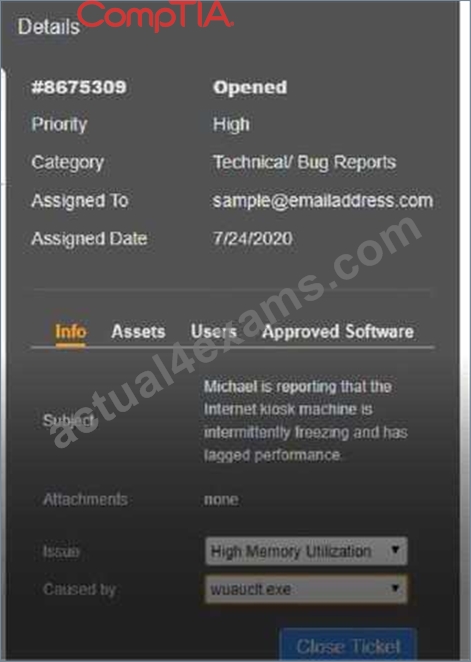
NEW QUESTION 34
Which of the following BEST describes why vulnerabilities found in ICS and SCADA can be difficult to remediate?
- A. ICS/SCADA systems rarely have full security functionality.
- B. ICS/SCADA systems do not allow remote connections.
- C. ICS/SCADA systems use encrypted traffic to communicate between devices.
- D. ICS/SCADA systems are not supported by the CVE publications.
Answer: D
NEW QUESTION 35
A malicious hacker wants to gather guest credentials on a hotel 802.11 network. Which of the following tools is the malicious hacker going to use to gain access to information found on the hotel network?
- A. tcpdump
- B. Nikto
- C. Nessus
- D. Aircrak-ng
Answer: D
NEW QUESTION 36
Which of the following is MOST effective for correlation analysis by log for threat management?
- A. SCAP
- B. IPS
- C. PCAP
- D. SIEM
Answer: D
NEW QUESTION 37
An analyst is performing penetration testing and vulnerability assessment activities against a new vehicle automation platform.
Which of the following is MOST likely an attack vector that is being utilized as part of the testing and assessment?
- A. FaaS
- B. CAN bus
- C. SoC
- D. RTOS
- E. GPS
Answer: D
Explanation:
Explanation
IoT devices also often run real-time operating systems (RTOS). These are either special purpose operating systems or variants of standard operating systems designed to process data rapidly as it arrives from sensors or other IoT components.
NEW QUESTION 38
The following IDS log was discovered by a company's cybersecurity analyst:
Which of the following was launched against the company based on the IDS log?
- A. Cross-site scripting attack
- B. Buffer overflow attack
- C. Online password crack attack
- D. SQL injection attack
Answer: B
NEW QUESTION 39
A large software company wants to move its source control and deployment pipelines into a cloud- computing environment. Due to the nature of the business, management determines the recovery time objective needs to be within one hour. Which of the following strategies would put the company in the BEST position to achieve the desired recovery time?
- A. Establish an alternate site with active replication to other regions
- B. Configure a duplicate environment in the same region and load balance between both instances
- C. Set up every cloud component with duplicated copies and auto-scaling turned on
- D. Create a duplicate copy on premises that can be used for failover in a disaster situation
Answer: A
NEW QUESTION 40
A company office was broken into over the weekend. The office manager contacts the IT security group to provide details on which servers were stolen. The security analyst determines one of the stolen servers contained a list of customer PII information, and another server contained a copy of the credit card transactions processed on the Friday before the break-in. In addition to potential security implications of information that could be gleaned from those servers and the rebuilding/restoring of the data on the stolen systems, the analyst needs to determine any communication or notification requirements with respect to the incident. Which of the following items is MOST important when determining what information needs to be provided, who should be contacted, and when the communication needs to occur.
- A. Government and industry regulations
- B. Impact on the reputation of the company's name/brand
- C. Monetary value of data stolen
- D. Total number of records stolen
Answer: A
NEW QUESTION 41
A development team signed a contract that requires access to an on-premises physical server.
Access must be restricted to authorized users only and cannot be connected to the Internet.
Which of the following solutions would meet this requirement?
- A. Virtualize the server.
- B. Establish a hosted SSO.
- C. Implement a CASB.
- D. Air gap the server.
Answer: B
NEW QUESTION 42
The IT department at a growing law firm wants to begin using a third-party vendor for vulnerability monitoring and mitigation. The executive director of the law firm wishes to outline the assumptions and expectations between the two companies. Which of the following documents might be referenced in the event of a security breach at the law firm?
- A. NDA
- B. SOW
- C. SLA
- D. MOU
Answer: C
NEW QUESTION 43
An alert is issued from the SIEM that indicates a large number of failed logins for the same account name on one of the application servers starting at 10:20 a.m. No other significant failed login activity is detected. Using Splunk to search for activity pertaining to that account name, a security analyst finds the account has been authenticating successfully for some time and started to fail this morning. The account is attempting to authenticate from an internal server that is running a database to an application server. No other security activity is detected on the network.
The analyst discovers the account owner is a developer who no longer works for the company.
Which of the following is the MOST likely reason for the failed login attempts for that account?
- A. A successful malware attack has provided someone access to the network, and failed login attempts are an indication of an attempt to privilege access to the application
- B. The account that is failing to authenticate has not been maintained, and the company password change policy time frame has been reached for that account
- C. The license for the application has expired, and the failed logins will continue to occur until a new license key is installed on the application
- D. The host-based firewall is blocking port 389 LDAP communication, preventing the login credentials from being received by the application server
Answer: B
NEW QUESTION 44
A security analyst receives an alert that highly sensitive information has left the company's network Upon investigation, the analyst discovers an outside IP range has had connections from three servers more than 100 times m the past month.
The affected servers are virtual machines.
Which of the following is the BEST course of action?
- A. Report the data exfiltration to management take the affected servers offline, conduct an antivirus scan, remediate all threats found, and return the servers to service.
- B. Shut down the servers as soon as possible, move them to a clean environment, restart, run a vulnerability scanner to find weaknesses determine the root cause, remediate, and report
- C. Disconnect the affected servers from the network, use the virtual machine console to access the systems, determine which information has left the network, find the security weakness, and remediate
- D. Determine if any other servers have been affected, snapshot any servers found, determine the vector that was used to allow the data exfiltration. fix any vulnerabilities, remediate, and report.
Answer: B
NEW QUESTION 45
Bootloader malware was recently discovered on several company workstations. All the workstations run Windows and are current models with UEFI capability.
Which of the following UEFI settings is the MOST likely cause of the infections?
- A. Secure boot mode
- B. Native mode
- C. Fast boot mode
- D. Compatibility mode
Answer: D
NEW QUESTION 46
A network attack that is exploiting a vulnerability in the SNMP is detected.
Which of the following should the cybersecurity analyst do FIRST?
- A. Escalate the incident to senior management for guidance.
- B. Disable all privileged user accounts on the network.
- C. Apply the required patches to remediate the vulnerability.
- D. Temporarily block the attacking IP address.
Section: (none)
Explanation
Answer: C
Explanation:
Reference:
https://beyondsecurity.com/scan-pentest-network-vulnerabilities-snmp-protocol-version- detection.html
NEW QUESTION 47
......
Authentic Best resources for CS0-002 Online Practice Exam: https://www.actual4exams.com/CS0-002-valid-dump.html
CS0-002 Test Engine Practice Exam: https://drive.google.com/open?id=1ruRHrjlXxe02WBzqQIRNzHC7apzN8K6Q

