Use Real SY0-501 Dumps - CompTIA Correct Answers updated on 2022
Security+ SY0-501 Exam Practice Dumps
Architecture as well as Design
This objective will determine if you understand the role of IT frameworks, secure configuration guides, and best practices. Besides, it will also emphasize the skills listed below:
- The pros of using automation and resiliency methods;
- Security implications associated with embedded systems.
- Utilizing reliable systems design;
- Summary of the cloud and virtualization techniques;
- Significance of physical security controls;
- The significance of secure concepts of staging deployment;
- The implementation of reliable concepts of network architecture;
NEW QUESTION 57
Which of the following is an example of the second A in the AAA model?
- A. The encryption protocol successfully completes the handshake and establishes a connection
- B. A domain controller confirms membership in the appropriate group
- C. The event log records a successful login with a type code that indicates an interactive login
- D. The one-time password is keyed in, and the login system grants access
Answer: B
NEW QUESTION 58
A security administrator is given the security and availability profiles for servers that are being deployed.
* Match each RAID type with the correct configuration and MINIMUM number of drives.
* Review the server profiles and match them with the appropriate RAID type based on integrity, availability, I/O, storage requirements. Instructions:
* All drive definitions can be dragged as many times as necessary
* Not all placeholders may be filled in the RAID configuration boxes
* If parity is required, please select the appropriate number of parity checkboxes
* Server profiles may be dragged only once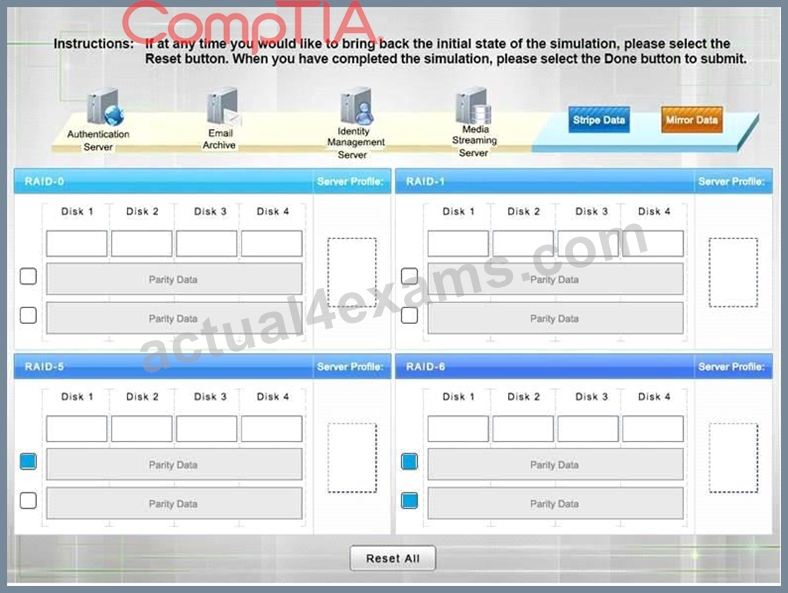
Answer:
Explanation: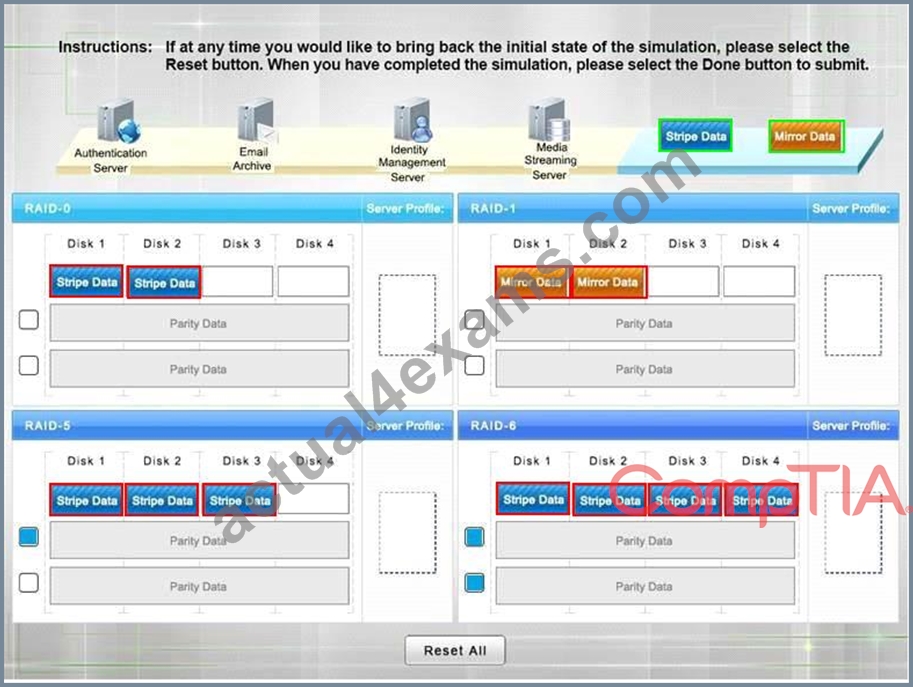
Explanation:
RAID-0 is known as striping. It is not a fault tolerant solution but does improve disk performance for read/write operations. Striping requires a minimum of two disks and does not use parity.
RAID-0 can be used where performance is required over fault tolerance, such as a media streaming server.
RAID-1 is known as mirroring because the same data is written to two disks so that the two disks have identical data. This is a fault tolerant solution that halves the storage space. A minimum of two disks are used in mirroring and does not use parity. RAID-1 can be used where fault tolerance is required over performance, such as on an authentication server. RAID-5 is a fault tolerant solution that uses parity and striping. A minimum of three disks are required for RAID-5 with one disk's worth of space being used for parity information. However, the parity information is distributed across all the disks. RAID-5 can recover from a sing disk failure.
RAID-6 is a fault tolerant solution that uses dual parity and striping. A minimum of four disks are required for RAID-6. Dual parity allows RAID-6 to recover from the simultaneous failure of up to two disks. Critical data should be stored on a RAID-6 system.
http://www.adaptec.com/en-us/solutions/raid_levels.html
NEW QUESTION 59
The Chief Information Security Officer (CISO) is asking for ways to protect against zero-day exploits. The CISO is concerned that an unrecognized threat could compromise corporate data and result in regulatory fines as well as poor corporate publicity. The network is mostly flat, with split staff/guest wireless functionality.
Which of the following equipment MUST be deployed to guard against unknown threats?
- A. Cloud-based antivirus solution, running as local admin, with push technology for definition updates
- B. Host-based heuristic IPS, segregated on a management VLAN, with direct control of the perimeter firewall ACLs
- C. Behavior-based IPS with a communication link to a cloud-based vulnerability and threat feed
- D. Implementation of an off-site datacenter hosting all company data, as well as deployment of VDI for all client computing needs
Answer: C
NEW QUESTION 60
A company's AUP requires:
Passwords must meet complexity requirements.
Passwords are changed at least once every six months.
Passwords must be at least eight characters long.
An auditor is reviewing the following report:
Which of the following controls should the auditor recommend to enforce the AUP?
- A. Password expiration
- B. Account lockout thresholds
- C. Account recovery
- D. Prohibit password reuse
Answer: A
NEW QUESTION 61
HOTSPOT
For each of the given items, select the appropriate authentication category from the drop down choices.
Select the appropriate authentication type for the following items:
Hot Area: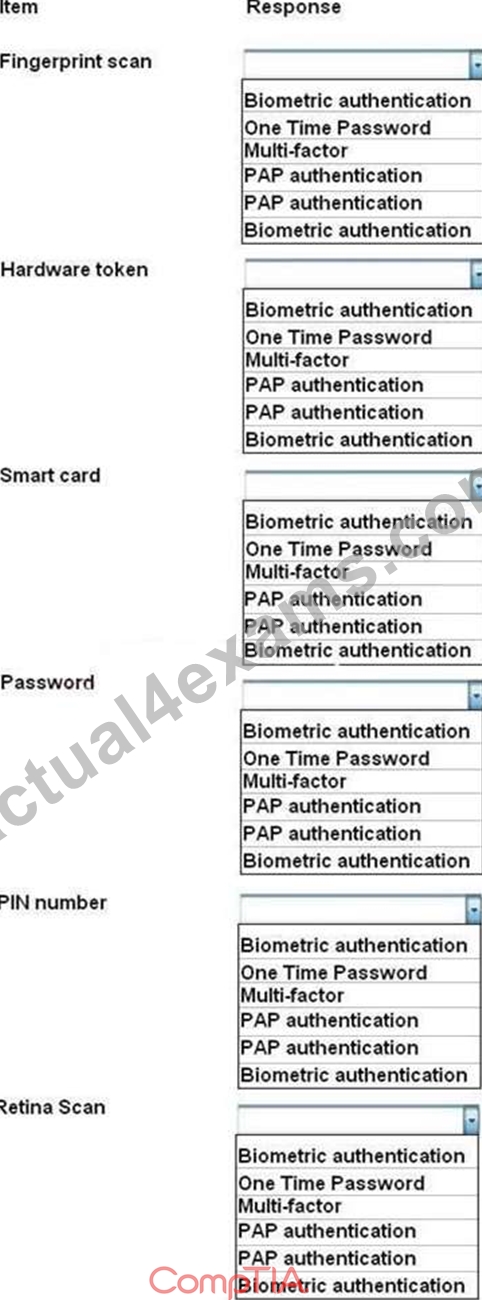
Answer:
Explanation: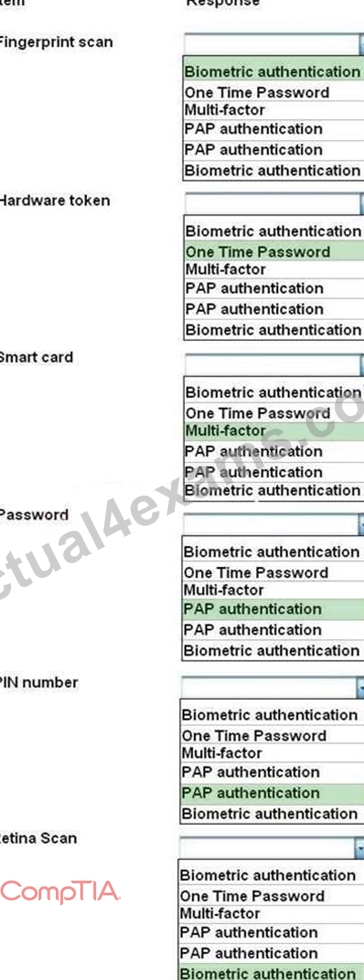
NEW QUESTION 62
An analyst is reviewing a simple program for potential security vulnerabilities before being deployed to a Windows server. Given the following code:
Which of the following vulnerabilities is present?
- A. Backdoor
- B. Bad memory pointer
- C. Integer overflow
- D. Buffer overflow
Answer: D
NEW QUESTION 63
A high-security defense installation recently begun utilizing large guard dogs that bark very loudly and excitedly at the slightest provocation. Which of the following types of controls does this BEST describe?
- A. Preventive
- B. Deterrent
- C. Compensating
- D. Detective
Answer: B
NEW QUESTION 64
In a corporation where compute utilization spikes several times a year, the Chief Information Officer (CIO) has requested a cost-effective architecture to handle the variable capacity demand. Which of the following characteristics BEST describes what the CIO has requested?
- A. Elasticity
- B. Scalability
- C. High availability
- D. Redundancy
Answer: C
NEW QUESTION 65
A software developer wants to ensure that the application is verifying that a key is valid before establishing SSL connections with random remote hosts on the Internet. Which of the following should be used in the code? (Select TWO.)
- A. Software code private key
- B. SSL symmetric encryption key
- C. Remote server public key
- D. Escrowed keys
- E. OCSP
Answer: A,E
NEW QUESTION 66
Which of the following penetration testing concepts is being used when an attacker uses public Internet
databases to enumerate and learn more about a target?
- A. Initial exploitation
- B. Pivoting
- C. Reconnaissance
- D. Vulnerability scanning
- E. White box testing
Answer: C
NEW QUESTION 67
A security administrator is implementing a secure method that allows developers to place files or objects onto a Linux server. Developers are required to log in using a username, password, and asymmetric key.
Which of the following protocols should be implemented?
- A. SFTP
- B. IPSec
- C. SSL/TLS
- D. SRTP
Answer: A
NEW QUESTION 68
A systems administrator is installing and configuring an application service that requires access to read and write to log and configuration files on a local hard disk partition. The service must run as an account with authorization to interact with the file system. Which of the following would reduce the attack surface added by the service and account? (Choose two.)
- A. Use a unique managed service account.
- B. Add the account to the local administrators group.
- C. Use a guest account placed in a non-privileged users group.
- D. Enable and review account audit logs.
- E. Enforce least possible privileges for the account.
- F. Utilize a generic password for authenticating.
Answer: A,E
NEW QUESTION 69
The IT department needs to prevent users from installing untested applications. Which of the following would provide the BEST solution?
- A. Least privilege
- B. Account lockout
- C. Antivirus
- D. Job rotation
Answer: A
NEW QUESTION 70
A department head at a university resigned on the first day of the spring semester. It was subsequently determined that the department head deleted numerous files and directories from the server-based home directory while the campus was closed. Which of the following policies or procedures co have prevented this from occurring?
- A. Time-of-day restrictions
- B. Account expiration
- C. Offboarding
- D. Permission auditing and review
Answer: C
NEW QUESTION 71
A manager wants to distribute a report to several other managers within the company. Some of them reside in remote locations that are not connected to the domain but have a local server. Because there is sensitive data within the report and the size of the report is beyond the limit of the email attachment size, emailing the report is not an option. Which of the following protocols should be implemented to distribute the report securely? (Select three.)
- A. SSH
- B. HTTPS
- C. S/MIME
- D. FTPS
- E. SRTP
- F. SNMPv3
- G. LDAPS
Answer: A,B,D
NEW QUESTION 72
An employee on the Internet facing part of a company's website submits a 20-character phrase in a small textbox on a web form. The website returns a message back to the browser stating.
Of which of the following is this an example?
- A. Resources exhaustion
- B. Improper error handling
- C. Improperly configured account
- D. Buffer overflow
Answer: B
NEW QUESTION 73
A company is performing an analysis of the corporate enterprise network with the intent of identifying any one system, person, function, or service that, when neutralized, will cause or cascade disproportionate damage to the company's revenue, referrals, and reputation. Which of the following is an element of the BIA that this action is addressing?
- A. Risk register
- B. Value assessment
- C. Single point of failure
- D. Identification of critical systems
Answer: D
NEW QUESTION 74
Which of the following penetration testing concepts is an attacker MOST interested in when placing the path of a malicious file in the Windows/CurrentVersion/Run registry key?
- A. Pivoting
- B. Escalation of privilege
- C. Persistence
- D. Active reconnaissance
Answer: B
NEW QUESTION 75
An auditor wants to test the security posture of an organization by running a tool that will display the following:
Which of the following commands should be used?
- A. nbtstat
- B. ipconfig
- C. arp
- D. nc
Answer: A
NEW QUESTION 76
Which of the following describes the BEST approach for deploying application patches?
- A. Test the patches in a test environment, apply them to the production systems, and then apply them to a staging environment.
- B. Test the patches in a staging environment, develop against them in the development environment, and then apply them to the production systems.
- C. Apply the patches to the production systems, apply them in a staging environment, and then test all of them in a testing environment
- D. Apply the patches to systems in a testing environment, then to systems in a staging environment, and finally to production systems
Answer: D
NEW QUESTION 77
DRAG DROP
You have been tasked with designing a security plan for your company. Drag and drop the appropriate security controls on the floor plan.
Instructions: All objects must be used and all place holders must be filled. Order does not matter. When you have completed the simulation, please select the Done button to submit.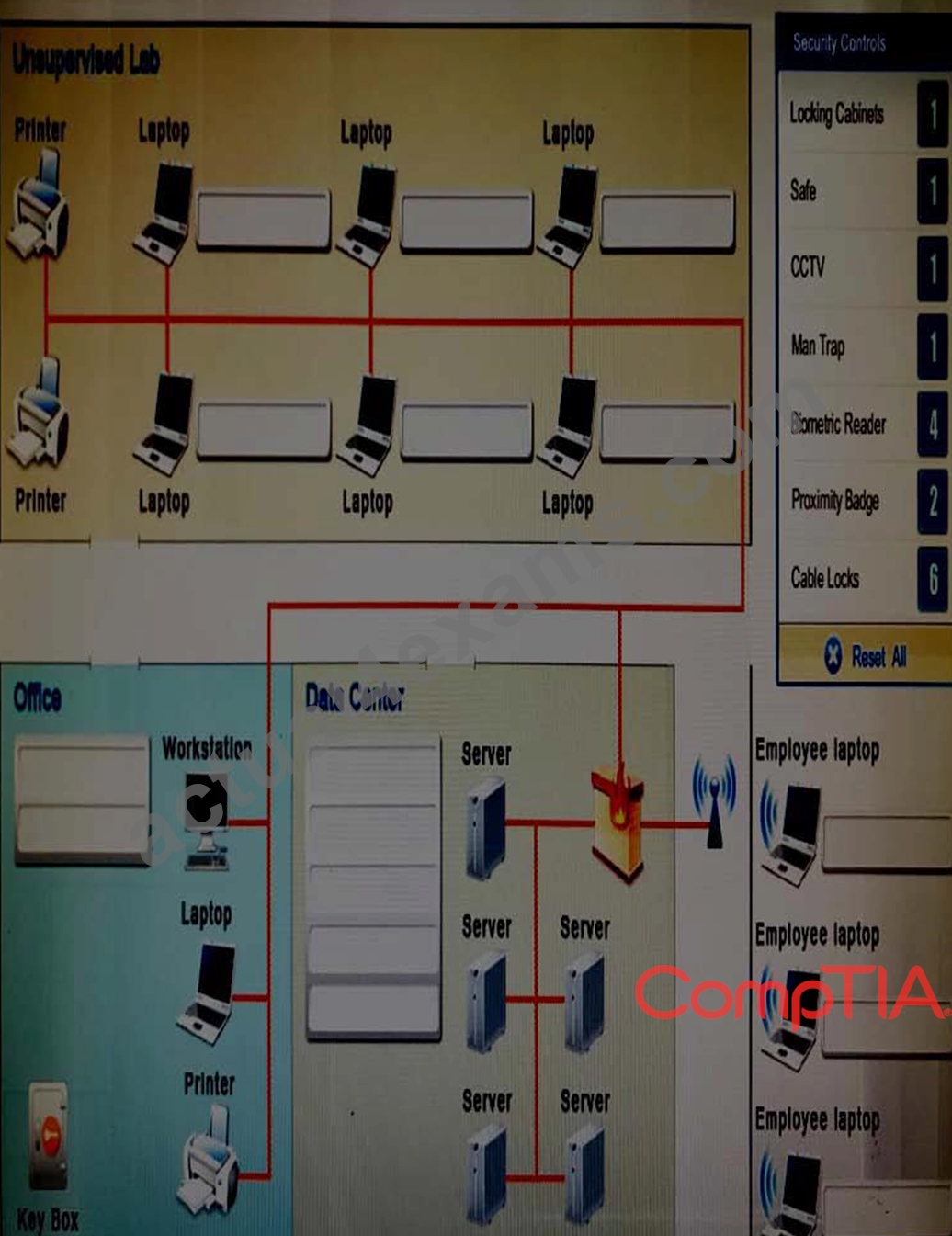
Answer:
Explanation: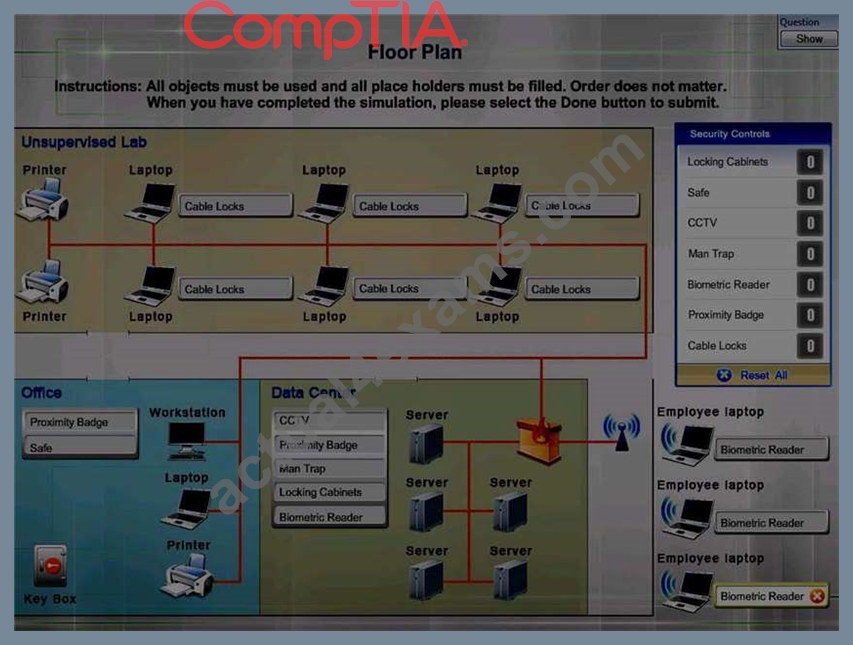
Cable locks - Adding a cable lock between a laptop and a desk prevents someone from picking it up and walking away Proximity badge + reader Safe is a hardware/physical security measure Mantrap can be used to control access to sensitive areas. CCTV can be used as video surveillance.
Biometric reader can be used to control and prevent unauthorized access. Locking cabinets can be used to protect backup media, documentation and other physical artefacts.
NEW QUESTION 78
A forensic expert is given a hard drive from a crime scene and is asked to perform an investigation. Which of the following is the FIRST step the forensic expert needs to take the chain of custody?
- A. Create a hash of the hard rive
- B. Make a forensic copy
- C. Recover the hard drive data
- D. Update the evidence log
Answer: D
NEW QUESTION 79
SIMULATION
You have just received some room and WiFi access control recommendations from a security consulting company. Click on each building to bring up available security controls. Please implement the following requirements:
The Chief Executive Officer's (CEO) office had multiple redundant security measures installed on the door to the office. Remove unnecessary redundancies to deploy three-factor authentication, while retaining the expensive iris render.
The Public Cafe has wireless available to customers. You need to secure the WAP with WPA and place a passphrase on the customer receipts.
In the Data Center you need to include authentication from the "something you know" category and take advantage of the existing smartcard reader on the door.
In the Help Desk Office, you need to require single factor authentication through the use of physical tokens given to guests by the receptionist.
The PII Office has redundant security measures in place. You need to eliminate the redundancy while maintaining three-factor authentication and retaining the more expensive controls.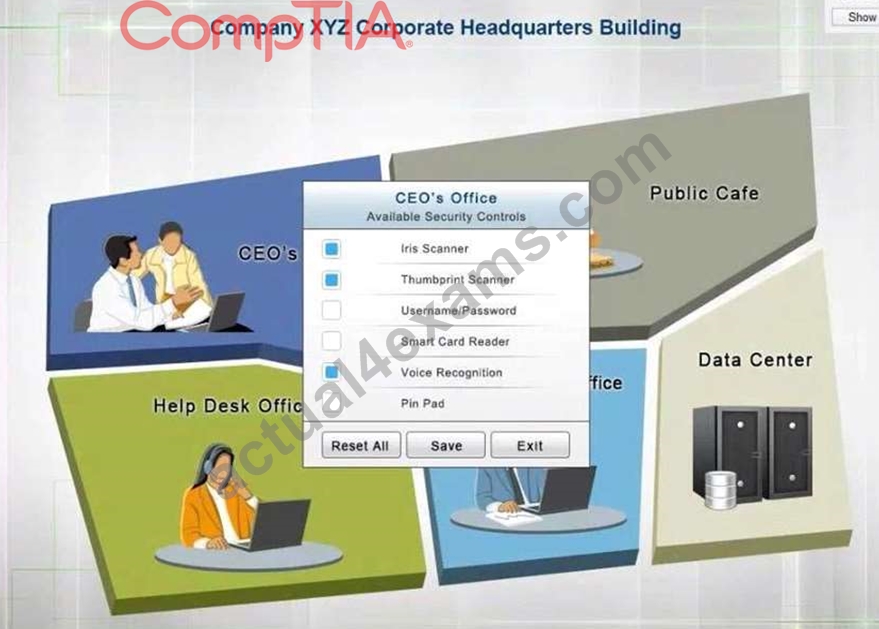
Instructions: The original security controls for each office can be reset at any time by selecting the Reset button. Once you have met the above requirements for each office, select the Save button. When you have completed the entire simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.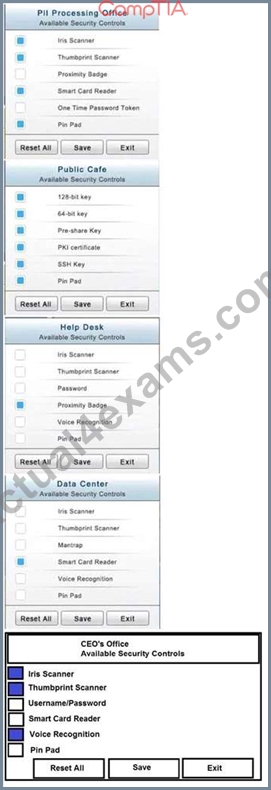
Answer:
Explanation: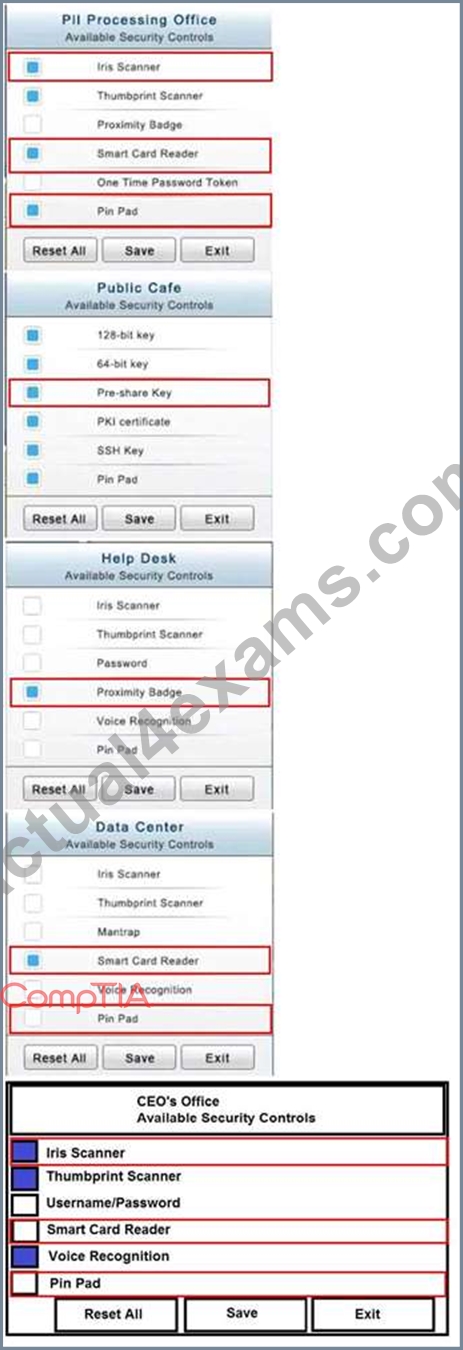
NEW QUESTION 80
A security analyst is asked to check the configuration of the company's DNS service on the server. Which of the following command line tools should the analyst use to perform the Initial assessment?
- A. tcpdump
- B. ipconfig/ifconfig
- C. nslookup/dlg
- D. traced
Answer: D
NEW QUESTION 81
An administrator is configuring access to information located on a network file server named "Bowman".
The files are located in a folder named "BalkFiles". The files are only for use by the "Matthews" division and should be read-only. The security policy requires permissions for shares to be managed at the file system layer and also requires those permissions to be set according to a least privilege model. Security policy for this data type also dictates that administrator-level accounts on the system have full access to the files.
The administrator configures the file share according to the following table:
Which of the following rows has been misconfigured?
- A. Row 3
- B. Row 5
- C. Row 1
- D. Row 2
- E. Row 4
Answer: E
NEW QUESTION 82
......
Get ready to pass the SY0-501 Exam right now using our Security+ Exam Package: https://www.actual4exams.com/SY0-501-valid-dump.html

