312-50v10 Dumps 2022 - New EC-COUNCIL 312-50v10 Exam Questions
Free 312-50v10 braindumps download (312-50v10 exam dumps Free Updated)
Module 4: Enumeration
The objective covers your knowledge of enumeration concepts; various methods for NetBIOS enumeration; various methods for SNMP enumeration; various methods for LDAP enumeration various methods for NTP enumeration; various methods DNS and SMTP enumeration countermeasures; enumeration PEN testing.
NEW QUESTION 180
What attack is used to crack passwords by using a precomputed table of hashed passwords?
- A. Dictionary Attack
- B. Brute Force Attack
- C. Rainbow Table Attack
- D. Hybrid Attack
Answer: C
Explanation:
Explanation
NEW QUESTION 181
The following is part of a log file taken from the machine on the network with the IP address of 192.168.1.106: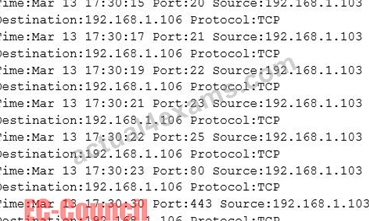
What type of activity has been logged?
- A. Port scan targeting 192.168.1.106
- B. Teardrop attack targeting 192.168.1.106
- C. Port scan targeting 192.168.1.103
- D. Denial of service attack targeting 192.168.1.103
Answer: A
NEW QUESTION 182
What is a successful method for protecting a router from potential smurf attacks?
- A. Placing the router in broadcast mode
- B. Installing the router outside of the network's firewall
- C. Disabling the router from accepting broadcast ping messages
- D. Enabling port forwarding on the router
Answer: C
NEW QUESTION 183
Trinity needs to scan all hosts on a /16 network for TCP port 445 only. What is the fastest way she can accomplish this with Nmap? Stealth is not a concern.
- A. nmap -s 445 -sU -T5 10.1.0.0/16
- B. nmap -sn -sF 10.1.0.0/16 445
- C. nmap -p 445 -n -T4 -open 10.1.0.0/16
- D. nmap -p 445 -max -Pn 10.1.0.0/16
Answer: C
NEW QUESTION 184
Which statement best describes a server type under an N-tier architecture?
- A. A group of servers at a specific layer
- B. A single server at a specific layer
- C. A group of servers with a unique role
- D. A single server with a specific role
Answer: C
NEW QUESTION 185
Eve stole a file named secret.txt, transferred it to her computer and she just entered these commands:
What is she trying to achieve?
- A. She is using ftp to transfer the file to another hacker named John.
- B. She is using John the Ripper to crack the passwords in the secret.txt file
- C. She is using John the Ripper to view the contents of the file.
- D. She is encrypting the file.
Answer: B
NEW QUESTION 186
The practical realities facing organizations today make risk response strategies essential. Which of the following is NOT one of the five basic responses to risk?
- A. Avoid
- B. Delegate
- C. Mitigate
- D. Accept
Answer: B
NEW QUESTION 187
Which of the following descriptions is true about a static NAT?
- A. A static NAT uses a one-to-many mapping.
- B. A static NAT uses a many-to-many mapping.
- C. A static NAT uses a many-to-one mapping.
- D. A static NAT uses a one-to-one mapping.
Answer: D
NEW QUESTION 188
An attacker has installed a RAT on a host. The attacker wants to ensure that when a user attempts to go to
"www.MyPersonalBank.com", that the user is directed to a phishing site.
Which file does the attacker need to modify?
- A. Networks
- B. Hosts
- C. Sudoers
- D. Boot.ini
Answer: B
Explanation:
Explanation
The hosts file is a computer file used by an operating system to map hostnames to IP addresses. The hosts file contains lines of text consisting of an IP address in the first text field followed by one or more host names.
References: https://en.wikipedia.org/wiki/Hosts_(file)
NEW QUESTION 189
The network administrator at Spears Technology, Inc has configured the default gateway Cisco router's access-list as below:
You are hired to conduct security testing on their network.
You successfully brute-force the SNMP community string using a SNMP crack tool.
The access-list configured at the router prevents you from establishing a successful connection.
You want to retrieve the Cisco configuration from the router. How would you proceed?
- A. Use the Cisco's TFTP default password to connect and download the configuration file
- B. Run a network sniffer and capture the returned traffic with the configuration file from the router
- C. Run Generic Routing Encapsulation (GRE) tunneling protocol from your computer to the router masking your IP address
- D. Send a customized SNMP set request with a spoofed source IP address in the range -
192.168.1.0
Answer: B,D
NEW QUESTION 190
Which of the following incident handling process phases is responsible for defining rules, collaborating human workforce, creating a back-up plan, and testing the plans for an organization?
- A. Identification phase
- B. Recovery phase
- C. Preparation phase
- D. Containment phase
Answer: C
NEW QUESTION 191
The network administrator contacts you and tells you that she noticed the temperature on the internal wireless router increases by more than 20% during weekend hours when the office was closed. She asks you to investigate the issue because she is busy dealing with a big conference and she doesn't have time to perform the task.
What tool can you use to view the network traffic being sent and received by the wireless router?
- A. Netcat
- B. Nessus
- C. Netstat
- D. Wireshark
Answer: D
Explanation:
Explanation
Wireshark is a Free and open source packet analyzer. It is used for network troubleshooting, analysis, software and communications protocol development, and education.
NEW QUESTION 192
A pen-tester is configuring a Windows laptop for a test. In setting up Wireshark, what river and library are required to allow the NIC to work in promiscous mode?
- A. Winprom
- B. Winpsw
- C. Libpcap
- D. Winpcap
Answer: D
NEW QUESTION 193
Joseph was the Web site administrator for the Mason Insurance in New York, who's main Web site was located at www.masonins.com. Joseph uses his laptop computer regularly to administer the Web site. One night, Joseph received an urgent phone call from his friend, Smith. According to Smith, the main Mason Insurance web site had been vandalized! All of its normal content was removed and replaced with an attacker's message ''Hacker Message: You are dead! Freaks!" From his office, which was directly connected to Mason Insurance's internal network, Joseph surfed to the Web site using his laptop. In his browser, the Web site looked completely intact.
No changes were apparent. Joseph called a friend of his at his home to help troubleshoot the problem. The Web site appeared defaced when his friend visited using his DSL connection. So, while Smith and his friend could see the defaced page, Joseph saw the intact Mason Insurance web site. To help make sense of this problem, Joseph decided to access the Web site using hisdial-up ISP. He disconnected his laptop from the corporate internal network and used his modem to dial up the same ISP used by Smith. After his modem connected, he quickly typed www.masonins.com in his browser to reveal the following web page: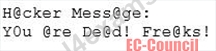
After seeing the defaced Web site, he disconnected his dial-up line, reconnected to the internal network, and used Secure Shell (SSH) to log in directly to the Web server. He ran Tripwire against the entire Web site, and determined that every system file and all the Web content on the server were intact. How did the attacker accomplish this hack?
- A. DNS poisoning
- B. SQL injection
- C. ARP spoofing
- D. Routing table injection
Answer: A
NEW QUESTION 194
Bob, your senior colleague, has sent you a mail regarding a deal with one of the clients. You are requested to accept the offer and you oblige. After 2 days. Bob denies that he had ever sent a mail. What do you want to
""know"" to prove yourself that it was Bob who had send a mail?
- A. Authentication
- B. Confidentiality
- C. Non-Repudiation
- D. Integrity
Answer: C
NEW QUESTION 195
Which of the following is the BEST way to defend against network sniffing?
- A. Using encryption protocols to secure network communications
- B. Use Static IP Address
- C. Register all machines MAC Address in a Centralized Database
- D. Restrict Physical Access to Server Rooms hosting Critical Servers
Answer: A
Explanation:
Explanation
A way to protect your network traffic from being sniffed is to use encryption such as Secure Sockets Layer (SSL) or Transport Layer Security (TLS). Encryption doesn't prevent packet sniffers from seeing source and destination information, but it does encrypt the data packet's payload so that all the sniffer sees is encrypted gibberish.
References:
http://netsecurity.about.com/od/informationresources/a/What-Is-A-Packet-Sniffer.htm
NEW QUESTION 196
Jimmy is standing outside a secure entrance to a facility. He is pretending to have a tense conversation on
his cell phone as an authorized employee badges in. Jimmy, while still on the phone, grabs the door as it
begins to close.
What just happened?
- A. Phishing
- B. Tailgating
- C. Masquerading
- D. Whaling
Answer: B
NEW QUESTION 197
If executives are found liable for not properly protecting their company's assets and information systems, what type of law would apply in this situation?
- A. Criminal
- B. Common
- C. Civil
- D. International
Answer: C
NEW QUESTION 198
......
Verified 312-50v10 dumps Q&As - Pass Guarantee Exam Dumps Test Engine: https://www.actual4exams.com/312-50v10-valid-dump.html
312-50v10 Dumps for Pass Guaranteed - Pass 312-50v10 Exam: https://drive.google.com/open?id=1GZVxf9lAf5RJcYAcHhOZHDsVdLS2ioUk

