Free Certified Ethical Hacker 312-50v10 Ultimate Study Guide (Updated 745 Questions)
Get to the Top with 312-50v10 Practice Exam Questions
Module 11: Session Hijacking
In the framework of this subject area, the students need to demonstrate their understanding of session hijacking concepts; application level session hijacking; network level session hijacking; session hijacking tools; session hijacking penetration testing; session hijacking countermeasures.
Module 7: Malware Threats
To tackle the questions associated with this subject, the applicants must be conversant with the basic malware and malware propagation methods; Trojans, their kinds, and how to infect systems; viruses, their kinds, and how they infect files; computer worms; malware analysis processes; various techniques to identify malware; malware countermeasures; malware penetration testing.
NEW QUESTION 419
Why containers are less secure that virtual machine?
- A. Host OS on containers has a larger surface attack.
- B. A compromise container may cause a CPU starvation of the host.
- C. Containers may fulfill disk space of the host.
- D. Containers are attached to the same virtual network.
Answer: B
NEW QUESTION 420
It is a kind of malware (malicious software) that criminals install on your computer so they can lock it from a remote location. This malware generates a pop-up window, webpage, or email warning from what looks like an official authority. It explains that your computer has been locked because of possible illegal activities on it and demands payment before you can access your files and programs again.
Which of the following terms best matches the definition?
- A. Ransomware
- B. Adware
- C. Riskware
- D. Spyware
Answer: A
Explanation:
Explanation
Ransomware is a type of malware that can be covertly installed on a computer without knowledge or intention of the user that restricts access to the infected computer system in some way, and demands that the user pay a ransom to the malware operators to remove the restriction. Some forms of ransomware systematically encrypt files on the system's hard drive, which become difficult or impossible to decrypt without paying the ransom for the encryption key, while some may simply lock the system and display messages intended to coax the user into paying. Ransomware typically propagates as a Trojan.
References: https://en.wikipedia.org/wiki/Ransomware
NEW QUESTION 421
Which of the following security operations is used for determining the attack surface of an organization?
- A. Reviewing the need for a security clearance for each employee
- B. Running a network scan to detect network services in the corporate DMZ
- C. Training employees on the security policy regarding social engineering
- D. Using configuration management to determine when and where to apply security patches
Answer: B
Explanation:
Explanation
For a network scan the goal is to document the exposed attack surface along with any easily detected vulnerabilities.
References:
http://meisecurity.com/home/consulting/consulting-network-scanning/
NEW QUESTION 422
ICMP ping and ping sweeps are used to check for active systems and to check
- A. the number of hops an ICMP ping takes to reach a destination.
- B. if ICMP ping traverses a firewall.
- C. the route that the ICMP ping took.
- D. the location of the switchport in relation to the ICMP ping.
Answer: B
NEW QUESTION 423
Which of the following is an example of an asymmetric encryption implementation?
- A. SHA1
- B. MD5
- C. PGP
- D. 3DES
Answer: C
NEW QUESTION 424
This phase will increase the odds of success in later phases of the penetration test. It is also the very first step in Information Gathering and it will tell you the "landscape" looks like. What is the most important phase of ethical hacking in which you need to spend a considerable amount of time?
- A. gaining access
- B. footprinting
- C. network mapping
- D. escalating privileges
Answer: B
NEW QUESTION 425
You have successfully gained access to a Linux server and would like to ensure that the succeeding outgoing traffic from this server will not be caught by Network-Based Intrusion Detection Systems (NIDS).
What is the best way to evade the NIDS?
- A. Alternate Data Streams
- B. Out of band signaling
- C. Protocol Isolation
- D. Encryption
Answer: D
NEW QUESTION 426
Which of the following Bluetooth hacking techniques does an attacker use to send messages to users
without the recipient's consent, similar to email spamming?
- A. Bluejacking
- B. Bluesniffing
- C. Bluesnarfing
- D. Bluesmacking
Answer: A
NEW QUESTION 427
An attacker has been successfully modifying the purchase price of items purchased on the company's web site.
The security administrators verify the web server and Oracle database have not been compromised directly.
They have also verified the Intrusion Detection System (IDS) logs and found no attacks that could have caused this. What is the mostly likely way the attacker has been able to modify the purchase price?
- A. By using SQL injection
- B. By using cross site scripting
- C. By utilizing a buffer overflow attack
- D. By changing hidden form values
Answer: D
NEW QUESTION 428
This asymmetry cipher is based on factoring the product of two large prime numbers.
What cipher is described above?
- A. RSA
- B. SHA
- C. MD5
- D. RC5
Answer: A
Explanation:
Explanation
RSA is based on the practical difficulty of factoring the product of two large prime numbers, the factoring problem.
Note: A user of RSA creates and then publishes a public key based on two large prime numbers, along with an auxiliary value. The prime numbers must be kept secret. Anyone can use the public key to encrypt a message, but with currently published methods, if the public key is large enough, only someone with knowledge of the prime numbers can feasibly decode the message.
References: https://en.wikipedia.org/wiki/RSA_(cryptosystem)
NEW QUESTION 429
Which of the following parameters describe LM Hash (see exhibit):
Exhibit: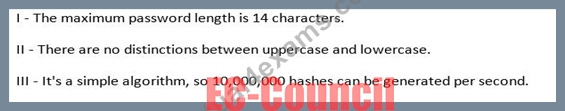
- A. I and II
- B. II
- C. I, II, and III
- D. I
Answer: C
Explanation:
The LM hash is computed as follows:
1. The user's password is restricted to a maximum of fourteen characters.
2. The user's password is converted to uppercase.
Etc.
14 character Windows passwords, which are stored with LM Hash, can be cracked in five seconds.
References: https://en.wikipedia.org/wiki/LM_hash
NEW QUESTION 430
Which of the following is an advantage of utilizing security testing methodologies to conduct a security audit?
- A. They provide a repeatable framework.
- B. They are available at low cost.
- C. They are subject to government regulation.
- D. Anyone can run the command line scripts.
Answer: A
NEW QUESTION 431
Which of the following is not a Bluetooth attack?
- A. Bluejacking
- B. Bluedriving
- C. Bluesnarfing
- D. Bluesmacking
Answer: B
Explanation:
Explanation/Reference:
NEW QUESTION 432 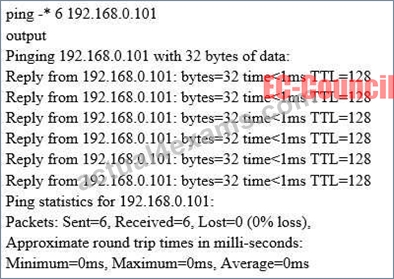
What does the option * indicate?
- A. t
- B. s
- C. n
- D. a
Answer: C
NEW QUESTION 433
You have compromised a server on a network and successfully opened a shell. You aimed to identify all operating systems running on the network. However, as you attempt to fingerprint all machines in the network using the nmap syntax below, it is not going through.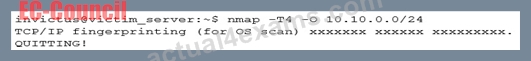
What seems to be wrong?
- A. The nmap syntax is wrong.
- B. This is a common behavior for a corrupted nmap application.
- C. OS Scan requires root privileges.
- D. The outgoing TCP/IP fingerprinting is blocked by the host firewall.
Answer: C
Explanation:
Explanation
You requested a scan type which requires root privileges.
References:
http://askubuntu.com/questions/433062/using-nmap-for-information-regarding-web-host
NEW QUESTION 434
Which of the following guidelines or standards is associated with the credit card industry?
- A. Health Insurance Portability and Accountability Act (HIPAA)
- B. Sarbanes-Oxley Act (SOX)
- C. Payment Card Industry Data Security Standards (PCI DSS)
- D. Control Objectives for Information and Related Technology (COBIT)
Answer: C
NEW QUESTION 435
Websites and web portals that provide web services commonly use the Simple Object Access Protocol SOAP.
Which of the following is an incorrect definition or characteristics in the protocol?
- A. Exchanges data between web services
- B. Based on XML
- C. Only compatible with the application protocol HTTP
- D. Provides a structured model for messaging
Answer: C
NEW QUESTION 436
......
Pass EC-COUNCIL 312-50v10 exam - questions - convert Tets Engine to PDF: https://www.actual4exams.com/312-50v10-valid-dump.html
Use Real 312-50v10 Dumps Free Sample Questions and Practice Test Engine : https://drive.google.com/open?id=1GZVxf9lAf5RJcYAcHhOZHDsVdLS2ioUk

