[Jun 10, 2022] Free MuleSoft Certified Architect MCIA-Level-1 Official Cert Guide PDF Download
MuleSoft MCIA-Level-1 Official Cert Guide PDF
For more info read reference:
NEW QUESTION 18
An organization is migrating all its Mule applications to Runtime Fabric (RTF). None of the Mule applications use Mule domain projects.
Currently, all the Mule applications have been manually deployed to a server group among several customer hosted Mule runtimes.
Port conflicts between these Mule application deployments are currently managed by the DevOps team who carefully manage Mule application properties files.
When the Mule applications are migrated from the current customer-hosted server group to Runtime Fabric (RTF), fo the Mule applications need to be rewritten and what DevOps port configuration responsibilities change or stay the same?
- A. NO, the Mule applications do NO need to be rewritten
DevOps NO LONGER needs to manage port conflicts between the Mule applications. - B. Yes, the Mule applications Must be rewritten
DevOps Must Still Manage port conflicts. - C. NO, The Mule applications do NOT need to be rewritten
DevOps MUST STILL manage port conflicts - D. Yes, the Mule applications Must be rewritten
DevOps No Longer needs to manage port conflicts between the Mule applications
Answer: C
NEW QUESTION 19
An organization will deploy Mule applications to CloudHub. Business requirements mandate that all application logs be stored ONLY in an external Splunk consolidated logging service and NOT in CloudHub.
In order to most easily store Mule application logs ONLY in Splunk, how must Mule application logging be configured in Runtime Manager, and where should the log4j2 Splunk appender be defined?
- A. Keep the default logging configuration in Runtime Manager
Define the Splunk appender in EACH Mule application's log4j2.xml file - B. Disable CloudHub logging in Runtime Manager
Define the Splunk appender in ONE global log4j2.xml file that is uploaded once to Runtime Manager to support all Mule application deployments - C. Disable CloudHub logging in Runtime Manager
Define the Splunk appender in EACH Mule application's log4j2.xml file - D. Keep the default logging configuration in Runtime Manager
Define the Splunk appender in ONE global log4j2.xml file that is uploaded once to Runtime Manager to support all Mule application deployments
Answer: B
Explanation:
Explanation/Reference:
NEW QUESTION 20
An integration Mute application is being designed to process orders by submitting them to a backend system for offline processing. Each order will be received by the Mute application through an HTTPS POST and must be acknowledged immediately. Once acknowledged, the order will be submitted to a backend system. Orders that cannot be successfully submitted due to rejections from the backend system will need to be processed manually (outside the backend system).
The Mule application will be deployed to a customer-hosted runtime and is able to use an existing ActiveMQ broker if needed.
The backend system has a track record of unreliability both due to minor network connectivity issues and longer outages.
What idiomatic (used for their intended purposes) combination of Mule application components and ActiveMQ queues are required to ensure automatic submission of orders to the backend system, while minimizing manual order processing?
- A. An On Error scope Non-persistent VM ActiveMQ Dead Letter Queue for manual processing
- B. Until Successful componentMuleSoft Object Store ActiveMQ is NOT needed or used
- C. An On Error scope MuleSoft Object Store ActiveMQ Dead Letter Queue for manual processing
- D. Until Successful component ActiveMQ long retry Queue ActiveMQ Dead Letter Queue for manual processing
Answer: A
NEW QUESTION 21
A Mule application uses the Database connector.
What condition can the Mule application automatically adjust to or recover from without needing to restart or redeploy the Mule application?
- A. One of the stored procedures being called by the Mule application has been renamed
- B. The credentials for accessing the database have been updated and the previous credentials are no longer valid
- C. The database server was unavailable for four hours due to a major outage but is now fully operational again
- D. The database server has been updated and hence the database driver library/JAR needs a minor version upgrade
Answer: C
Explanation:
* Any change in the application will require a restart except when the issue outside the app. For below situations , you would need to redeploy the code after doing necessary changes
-- One of the stored procedures being called by the Mule application has been renamed. In this case, in the Mule application you will have to do changes to accommodate the new stored procedure name.
-- Required redesign of Mule applications to follow microservice architecture principles. As code is changed, deployment is must
-- If the credentials changed and you need to update the connector or the properties.
-- The credentials for accessing the database have been updated and the previous credentials are no longer valid. In this situation you need to restart or redeploy depending on how credentials are configured in Mule application.
* So Correct answer is The database server was unavailable for four hours due to a major outage but is now fully operational again as this is the only external issue to application.
NEW QUESTION 22
What limits if a particular Anypoint Platform user can discover an asset in Anypoint Exchange?
- A. The type of the asset in Anypoint Exchange
- B. The existence of a public Anypoint Exchange portal to which the asset has been published
- C. The business groups to which the user belongs
- D. If Design Center and RAML were both used to create the asset
Answer: A
Explanation:
Explanation/Reference: https://docs.mulesoft.com/exchange/to-find-info
NEW QUESTION 23
What metrics about API invocations are available for visualization in custom charts using Anypoint Analytics?
- A. Request size, number of requests, JDBC Select operation result set size
- B. Request size, number of requests, response size, response time
- C. Request size, number of requests, JDBC Select operation response time
- D. Request size, request HTTP verbs, response time
Answer: B
NEW QUESTION 24
A new Mule application under development must implement extensive data transformation logic. Some of the data transformation functionality is already available as external transformation services that are mature and widely used across the organization; the rest is highly specific to the new Mule application.
The organization follows a rigorous testing approach, where every service and application must be extensively acceptance tested before it is allowed to go into production.
What is the best way to implement the data transformation logic for this new Mule application while minimizing the overall testing effort?
- A. Implement transformation logic in the new Mule application using DataWeave, invoking existing transformation services when possible
- B. Implement and expose all transformation logic as microservices using DataWeave, so it can be reused by any application component that needs it, including the new Mule application
- C. Implement transformation logic in the new Mule application using DataWeave, replicating the transformation logic of existing transformation services
- D. Extend the existing transformation services with new transformation logic and invoke them from the new Mule application
Answer: D
NEW QUESTION 25
Refer to the exhibit.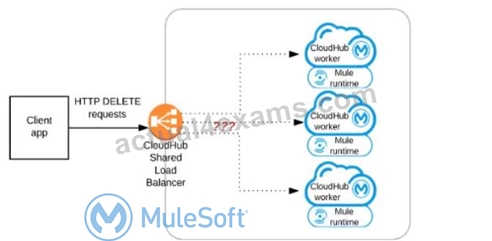
A Mule application has an HTTP Listener that accepts HTTP DELETE requests. This Mule application Is deployed to three CloudHub workers under the control of the CloudHub Shared Load Balancer.
A web client makes a sequence of requests to the Mule application's public URL.
How is this sequence of web client requests distributed among the HTTP Listeners running in the three CloudHub workers?
- A. Each request is routed (scattered) to ALL three CloudHub workers at the same time
- B. Each request is routed to the PRIMARY CloudHub worker in the PRIMARY Availability Zone (AZ)
- C. Each request is routed to ONE ARBiTRARY CloudHub worker in the PRIMARY Availability Zone (AZ)
- D. Each request Is routed to ONE ARBiTRARY CloudHub worker out of ALL three CloudHub workers
Answer: D
NEW QUESTION 26
Refer to the exhibit.
A Mule application is being designed to expose a SOAP web service to its clients.
What language is typically used inside the web service's interface definition to define the data structures that the web service Is expected to exchange with its clients?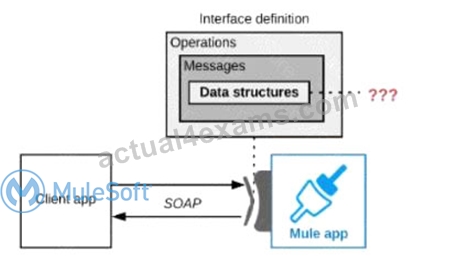
- A. RAMI
- B. WSDL
- C. XSD
- D. JSON Schema
Answer: B
NEW QUESTION 27
Refer to the exhibit.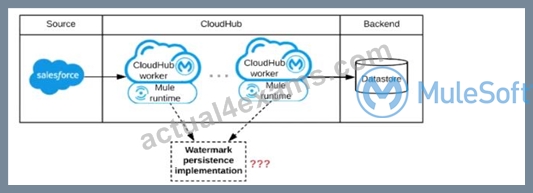
A Mule application is being designed to be deployed to several CIoudHub workers. The Mule application's integration logic is to replicate changed Accounts from Satesforce to a backend system every 5 minutes.
A watermark will be used to only retrieve those Satesforce Accounts that have been modified since the last time the integration logic ran.
What is the most appropriate way to implement persistence for the watermark in order to support the required data replication integration logic?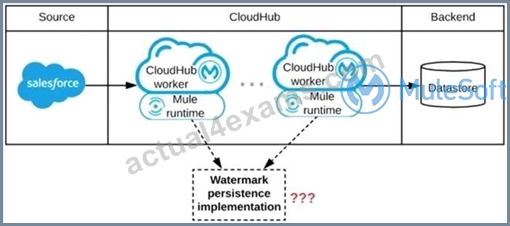
- A. Persistent Anypoint MQ Queue
- B. Persistent Object Store
- C. Persistent VM Queue
- D. Persistent Cache Scope
Answer: B
Explanation:
* An object store is a facility for storing objects in or across Mule applications. Mule uses object stores to persist data for eventual retrieval.
* Mule provides two types of object stores:
1) In-memory store - stores objects in local Mule runtime memory. Objects are lost on shutdown of the Mule runtime.
2) Persistent store - Mule persists data when an object store is explicitly configured to be persistent.
In a standalone Mule runtime, Mule creates a default persistent store in the file system. If you do not specify an object store, the default persistent object store is used.
MuleSoft Reference: https://docs.mulesoft.com/mule-runtime/3.9/mule-object-stores
NEW QUESTION 28
Mule applications need to be deployed to CloudHub so they can access on-premises database systems. These systems store sensitive and hence tightly protected data, so are not accessible over the internet.
What network architecture supports this requirement?
- A. An Anypoint VPC connected to the on-premises network using an IPsec tunnel or AWS DirectConnect, plus matching firewall rules in the VPC and on-premises network
- B. Static IP addresses for the Mule applications deployed to the CloudHub Shared Worker Cloud, plus matching firewall rules and IP whitelisting in the on-premises network
- C. Relocation of the database systems to a DMZ in the on-premises network, with Mule applications deployed to the CloudHub Shared Worker Cloud connecting only to the DMZ
- D. An Anypoint VPC with one Dedicated Load Balancer fronting each on-premises database system, plus matching IP whitelisting in the load balancer and firewall rules in the VPC and on-premises network
Answer: A
Explanation:
https://docs.mulesoft.com/runtime-manager/vpc-connectivity-methods-concept
NEW QUESTION 29
Additional nodes are being added to an existing customer-hosted Mule runtime cluster to improve performance. Mule applications deployed to this cluster are invoked by API clients through a load balancer.
What is also required to carry out this change?
- A. A new load balancer must be provisioned to allow traffic to the new nodes in a round-robin fashion
- B. External monitoring tools or log aggregators must be configured to recognize the new nodes
- C. API implementations using an object store must be adjusted to recognize the new nodes and persist to them
- D. New firewall rules must be configured to accommodate communication between API clients and the new nodes
Answer: C
Explanation:
Explanation/Reference: https://www.folkstalk.com/2019/11/mulesoft-integration-and-platform.html
NEW QUESTION 30
What aspect of logging is only possible for Mule applications deployed to customer-hosted Mule runtimes, but NOT for Mule applications deployed to CloudHub?
- A. To log certain messages to a custom log category
- B. To directly referenceone shared and customized log4j2.xml file from multiple Mule applications
- C. To change tog4j2 tog levels in Anypoint Runtime Manager without having to restart the Mule application
- D. To send Mule application log entries to Splunk
Answer: B
NEW QUESTION 31
A set of integration Mule applications, some of which expose APIs, are being created to enable a new business process. Various stakeholders may be impacted by this. These stakeholders are a combination of semi-technical users (who understand basic integration terminology and concepts such as JSON and XML) and technically skilled potential consumers of the Mule applications and APIs.
What Is an effective way for the project team responsible for the Mule applications and APIs being built to communicate withthese stakeholders using Anypoint Platform and its supplied toolset?
- A. Create Anypoint Exchange entries with pages elaborating the integration design, including API notebooks (where applicable) to help the stakeholders understand and interact with the Mule applications and APIs at various levels of technical depth
- B. Use Anypoint Design Center to implement the Mule applications and APIs and give the various stakeholders access to these Design Center projects, so they can collaborate and provide feedback
- C. Use Anypoint Exchange to register the various Mule applications and APIs and share the RAML definitions with the stakeholders, so they can be discovered
- D. Capture documentation about the Mule applications and APIs inline within the Mule integration flows and use Anypoint Studio's Export Documentation feature to provide an HTML version of this documentation to the stakeholders
Answer: A
NEW QUESTION 32
Refer to the exhibit.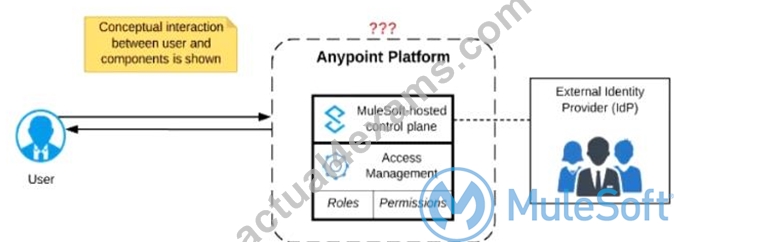
Anypoint Platform supports role-based access control (RBAC) to features of the platform. An organization has configured an external Identity Provider for identity management with Anypoint Platform.
What aspects of RBAC must ALWAYS be controlled from the Anypoint Platform control plane and CANNOT be controlled via the external Identity Provider?
- A. Assigning Anypoint Platform role(s) to a user
- B. Removing a user's access to Anypoint Platform when they no longer work for the organization
- C. Controlling the business group within Anypoint Platform to which the user belongs
- D. Assigning Anypoint Platform permissions to a role
Answer: D
NEW QUESTION 33
Refer to the exhibit.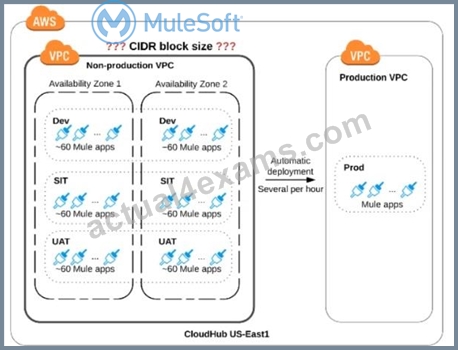
An organization is sizing an Anypoint VPC for the non-production deployments of those Mule applications that connect to the organization's on-premises systems. This applies to approx. 60 Mule applications. Each application is deployed to two CloudHub i workers. The organization currently has three non-production environments (DEV, SIT and UAT) that share this VPC. The AWS region of the VPC has two AZs.
The organization has a very mature DevOps approach which automatically progresses each application through all non-production environments before automatically deploying to production. This process results in several Mule application deployments per hour, using CloudHub's normal zero-downtime deployment feature.
What is a CIDR block for this VPC that results in the smallest usable private IP address range?
- A. 10.0.0.0/24 (256 IPs)
- B. 10.0.0.0/22 (1024 IPs)
- C. 10.0.0.0/26 (64 IPS)
- D. 10.0.0.0/25 (128 IPs)
Answer: B
NEW QUESTION 34
A company is building an application network and has deployed four Mule APIs: one experience API, one process API, and two system APIs. The logs from all the APIs are aggregated in an external log aggregation tool. The company wants to trace messages that are exchanged between multiple API implementations. What is the most idiomatic (based on its intended use) identifier that should be used to implement Mule event tracing across the multiple API implementations?
- A. Mule correlation ID
- B. Mule event ID
- C. Client's IP address
- D. DataWeave UUID
Answer: A
Explanation:
Correct answer is Mule correlation ID By design, Correlation Ids cannot be changed within a flow in Mule 4 applications and can be set only at source. This ID is part of the Event Context and is generated as soon as the message is received by the application. When a HTTP Request is received, the request is inspected for "X-Correlation-Id" header. If "X-Correlation-Id" header is present, HTTP connector uses this as the Correlation Id. If "X-Correlation-Id" header is NOT present, a Correlation Id is randomly generated. For Incoming HTTP Requests: In order to set a custom Correlation Id, the client invoking the HTTP request must set "X-Correlation-Id" header. This will ensure that the Mule Flow uses this Correlation Id. For Outgoing HTTP Requests: You can also propagate the existing Correlation Id to downstream APIs. By default, all outgoing HTTP Requests send "X-Correlation-Id" header. However, you can choose to set a different value to "X-Correlation-Id" header or set "Send Correlation Id" to NEVER.
NEW QUESTION 35
A Mule application is being designed to perform product orchestration. The Mule application needs to join together the responses from an Inventory API and a Product Sales History API with the least latency.
To minimize the overall latency, what is the most idiomatic (used for its intended purpose) design to call each API request in the Mule application?
- A. Call each API request in a separate Async scope
- B. Call each API request in a separate lookup call from a DataWeave reduce operator
- C. Call each API request in a separate route of a Parallel For Each scope
- D. Call each API request in a separate route of a Scatter-Gather
Answer: D
NEW QUESTION 36
An organization is evaluating using the CloudHub shared Load Balancer (SLB) vs creating a CloudHub dedicated load balancer (DLB). They are evaluating how this choice affects the various types of certificates used by CloudHub deplpoyed Mule applications, including MuleSoft-provided, customer-provided, or Mule application-provided certificates.
What type of restrictions exist on the types of certificates that can be exposed by the CloudHub Shared Load Balancer (SLB) to external web clients over the public internet?
- A. Only MuleSoft-provided certificates are exposed.
- B. Only customer-provided self-signed certificates are exposed.
- C. Only underlying Mule application certificates are exposed (pass-through)
- D. Only customer-provided wildcard certificates are exposed.
Answer: A
Explanation:
https://docs.mulesoft.com/runtime-manager/dedicated-load-balancer-tutorial
NEW QUESTION 37
......
Difficulty in Writing MuleSoft mcia - Level 1: MuleSoft Certified Integration Architect - Level 1 Exam
MuleSoft mcia - Level 1: MuleSoft Certified Integration Architect - Level 1 is a prestigious certification one could be graced with. But adverse to general notion certifying with MuleSoft is not that challenging if the candidates have utilized proper study preparation material to pass the MuleSoft mcia - Level 1: MuleSoft Certified Integration Architect - Level 1 exam with good grades. Actual4Exams consist of the foremost phenomenal and noteworthy questions answers and description that contents the complete course. Certification questions have a brilliant MuleSoft mcia - Level 1: MuleSoft Certified Integration Architect - Level 1 exam dumps with most recent and important questions and answers in PDF files. Actual4Exams are sure about the exactness and legitimacy of mcia-level-1 exam dumps which are getting validated by our MuleSoft certified experts. Candidates can easily pass the MuleSoft mcia - Level 1: MuleSoft Certified Integration Architect - Level 1 exam and get MuleSoft certification. These exam dumps are viewed as the best source to understand the MuleSoft mcia - Level 1: MuleSoft Certified Integration Architect - Level 1 well by simply pursuing examples questions and answers. If the candidate will practice the exam with mcia-level-1 exam dumps along with self-assessment to get the proper idea on MuleSoft accreditation and to crack the certification exam.
How to study the MuleSoft mcia - Level 1: MuleSoft Certified Integration Architect - Level 1 Exam
Preparation of certification exams could be covered with two resource types. The first one is the study guides, reference books, and study forums that are elaborated and appropriate for building information from the ground up. Apart from the video tutorials and lectures are a good option to ease the pain of through study and are relatively make the study process more interesting nonetheless these demand time and concentration from the learner. Smart candidates who wish to create a solid foundation altogether examination topics and connected technologies typically mix video lectures with study guides to reap the advantages of each, but practice exams or practice exam engines is one important study tool that goes typically unnoted by most candidates. Practice exams are designed with our experts to make exam prospects test their knowledge on skills attained in the course, as well as prospects become comfortable and familiar with the real exam environment. Statistics have indicated exam anxiety plays a much bigger role in a student's failure in the exam than the fear of the unknown. Actual4Exams expert team recommends preparing some notes on these topics along with it do not forget to practice MuleSoft mcia-level-1 exam dumps which had been written by our expert team, each of these can assist you loads to clear this exam with excellent marks.
Free MCIA-Level-1 Exam Dumps to Improve Exam Score: https://www.actual4exams.com/MCIA-Level-1-valid-dump.html

