The Most Efficient EX294 Pdf Dumps For Assured Success [2024]
We offers you the latest free online EX294 dumps to practice
Advantages of getting the RedHat EX294 Certification:
Following are some advantages, that a passed individual can get after getting the RedHat EX294 Certification:
Employability: The RHCE certification is the foundation for our highest level of certification-Red Hat Certified Architect (RHCA). It demonstrates competency in managing many systems using the Red Hat Ansible Automation Platform and executing common system administration tasks across a number of systems with Ansible.
Experience: Red Hat Certified Engineer certification validates the skill sets and experience required to support the Red Hat Enterprise Linux operating system on a variety of hardware platforms, including x86, x86_64, ARM, SPARC, and POWER.
Credibility: Red Hat Certified Engineer certification is accepted by most organizations as an indication of knowledge, expertise, and abilities. EX294 exam dumps can polish this expertise to be more competent.
Job security: Red Hat Certified Engineer certification is a requirement for the Red Hat Certified Architect certification.
Get to know about the RedHat EX294 Certification Exam?
RedHat EX294 is also known as the Red Hat Certified Engineer (RHCE) Exam. It examines your knowledge and skill in managing numerous systems using the Red Hat Ansible Automation Platform and execution of system tasks in a number of systems with Ansible. The expertise tested in the EX294 Exam is the base for system administration across many Red Hat products.
The Red Hat Ansible Automation Platform provides you with a powerful automation tool-set that helps you easily manage numerous systems and automate simple to complex tasks. With the Red Hat Ansible Automation Platform, you can define how each individual system is managed, from initial deployment to provisioning, configuring, and troubleshooting. You can also use Ansible to perform more complicated tasks, such as applying patches, configuring networks, and monitoring infrastructure. You can use EX294 exam dumps for the prep of the EX294 Exam, the hosts will assist you to manage nodes of the subjects and will help you to be well-prepared in a few months.
NEW QUESTION # 18
Create a playbook called timesvnc.yml in /home/sandy/ansible using rhel system role timesync. Set the time to use currently configured nip with the server 0.uk.pool.ntp.org. Enable burst. Do this on all hosts.
- A. Solution as:

- B. Solution as:

Answer: A
NEW QUESTION # 19
Create a playbook called web.yml as follows:
* The playbook runs on managed nodes in the "dev" host group
* Create the directory /webdev with the following requirements:
--> membership in the apache group
--> regular permissions: owner=r+w+execute, group=r+w+execute, other=r+execute
s.p=set group-id
* Symbolically link /var/www/html/webdev to /webdev
* Create the file /webdev/index.html with a single line of text that reads:
"Development"
--> it should be available on http://servera.lab.example.com/webdev/index.html
Answer:
Explanation:
Solution as:
# pwd
/home/admin/ansible/
# vim web.yml
---
- name:
hosts: dev
tasks:
- name: create group
yum:
name: httpd
state: latest
- name: create group
group:
name: apache
state: present
- name: creating directiory
file:
path: /webdev
state: directory
mode: '2775'
group: apache
- sefcontext:
target: '/webdev/index.html'
setype: httpd_sys_content_t
state: present
- name: Apply new SELinux file context to filesystem
command: restorecon -irv
- name: creating symbolic link
file:
src: /webdev
dest: /var/www/html/webdev
state: link
force: yes
- name: creating file
file:
path: /webdev/index.html
sate: touch
- name: Adding content to index.html file
copy:
dest: /webdev/index.html
content: "Development"
- name: add service to the firewall
firewalld:
service: http
permanent: yes
state: enabled
immediate: yes
- name: active http service
service:
name: httpd
state: restarted
enabled: yes
:wq
# ansible-playbook web.yml --syntax-check
# ansible-playbook web.yml
NEW QUESTION # 20
Install and configure ansible
User sandy has been created on your control node with the appropriate permissions already, do not change or modify ssh keys. Install the necessary packages to run ansible on the control node. Configure ansible.cfg to be in folder /home/sandy/ansible/ansible.cfg and configure to access remote machines via the sandy user. All roles should be in the path /home/sandy/ansible/roles. The inventory path should be in /home/sandy/ansible/invenlory.
You will have access to 5 nodes.
node1.example.com
node2.example.com
node3.example.com
node4.example.com
node5.example.com
Configure these nodes to be in an inventory file where node I is a member of group dev. nodc2 is a member of group test, node3 is a member of group proxy, nodc4 and node 5 are members of group prod. Also, prod is a member of group webservers.
Answer:
Explanation:
In/home/sandy/ansible/ansible.cfg
[defaults]
inventory=/home/sandy/ansible/inventory
roles_path=/home/sandy/ansible/roles
remote_user= sandy
host_key_checking=false
[privilegeescalation]
become=true
become_user=root
become_method=sudo
become_ask_pass=false
In /home/sandy/ansible/inventory
[dev]
node 1 .example.com
[test]
node2.example.com
[proxy]
node3 .example.com
[prod]
node4.example.com
node5 .example.com
[webservers:children]
prod
NEW QUESTION # 21
Create a playbook /home/bob /ansible/motd.yml that runs on all inventory hosts and docs the following: The playbook should replaee any existing content of/etc/motd in the following text. Use ansible facts to display the FQDN of each host On hosts in the dev host group the line should be "Welcome to Dev Server FQDN".
On hosts in the webserver host group the line should be "Welcome to Apache Server FQDN".
On hosts in the database host group the line should be "Welcome to MySQL Server FQDN".
- A. /home/sandy/ansible/apache.yml
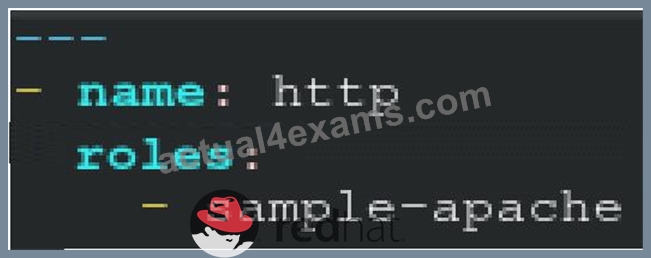
/home/sandy/ansible/roles/sample-apache/tasks/main.yml - B. /home/sandy/ansible/apache.yml
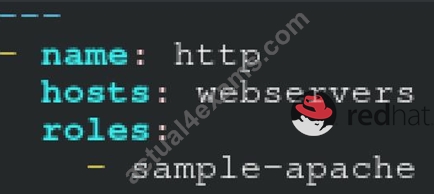
/home/sandy/ansible/roles/sample-apache/tasks/main.yml
Answer: B
NEW QUESTION # 22
Install and configure Ansible on the control-node control.realmX.example.com as
follows:
-------------------------------------------------------------------------------------------
--> Install the required packages
--> Create a static inventory file called /home/admin/ansible/inventory as follows:
node1.realmX.example.com is a member of the dev host group
node2.realmX.example.com is a member of the test host group
node3.realmX.example.com & node4.realmX.example.com are members of the prod
host group
node5.realmX.example.com is a member of the balancers host group.
prod group is a member of the webservers host group
--> Create a configuration file called ansible.cfg as follows:
--> The host inventory file /home/admin/ansible/inventory is defined
--> The location of roles used in playbooks is defined as /home/admin/ansible/ roles
Answer:
Explanation:
Solution as:
Through physical host, login to workstation.lab.example.com with user root.
# ssh [email protected]
# hostname
workstation.lab.example.com
# yum install platform-python*
# su - admin
# pwd
/home/admin/
# vim .vimrc
# mkdir -p ansible/roles
# cd ansible
# vim inventory
[dev]
servera.lab.example.com
[test]
serverb.example.com
[prod]
serverc.example.com
serverd.example.com
[balancer]
serverd.lab.example.com
[webservers:children]
prod
:!wq
# vim ansible.cfg
[defaults]
inventory = ./inventory
role_path = ./roles
remote_user = admin
ask_pass = false
[privilege_escalation]
become = true
become_method = sudo
become_user = root
become_ask_pass = false
:!wq
# ansible all --list-hosts
NEW QUESTION # 23
Create a role called sample-apache in /home/sandy/ansible/roles that enables and starts httpd, enables and starts the firewall and allows the webserver service. Create a template called index.html.j2 which creates and serves a message from /var/www/html/index.html Whenever the content of the file changes, restart the webserver service.
Welcome to [FQDN] on [IP]
Replace the FQDN with the fully qualified domain name and IP with the ip address of the node using ansible facts. Lastly, create a playbook in /home/sandy/ansible/ called apache.yml and use the role to serve the index file on webserver hosts.
Answer:
Explanation:
/home/sandy/ansible/apache.yml
/home/sandy/ansible/roles/sample-apache/tasks/main.yml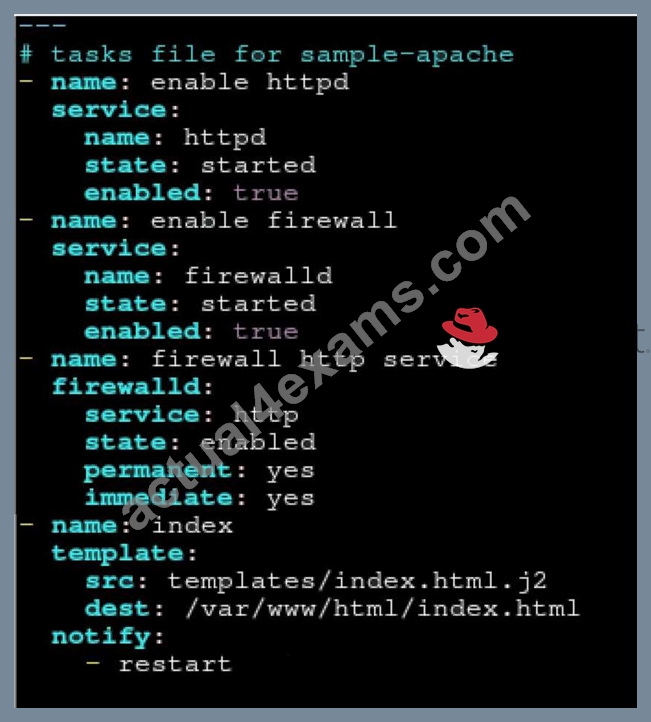
/home/sandy/ansible/roles/sample-apache/templates/index.html.j2
In /home/sandy/ansible/roles/sample-apache/handlers/main.yml
NEW QUESTION # 24
Create a playbook called issue.yml in /home/sandy/ansible which changes the file /etc/issue on all managed nodes: If host is a member of (lev then write "Development" If host is a member of test then write "Test" If host is a member of prod then write "Production"
Answer:
Explanation:
Solution as: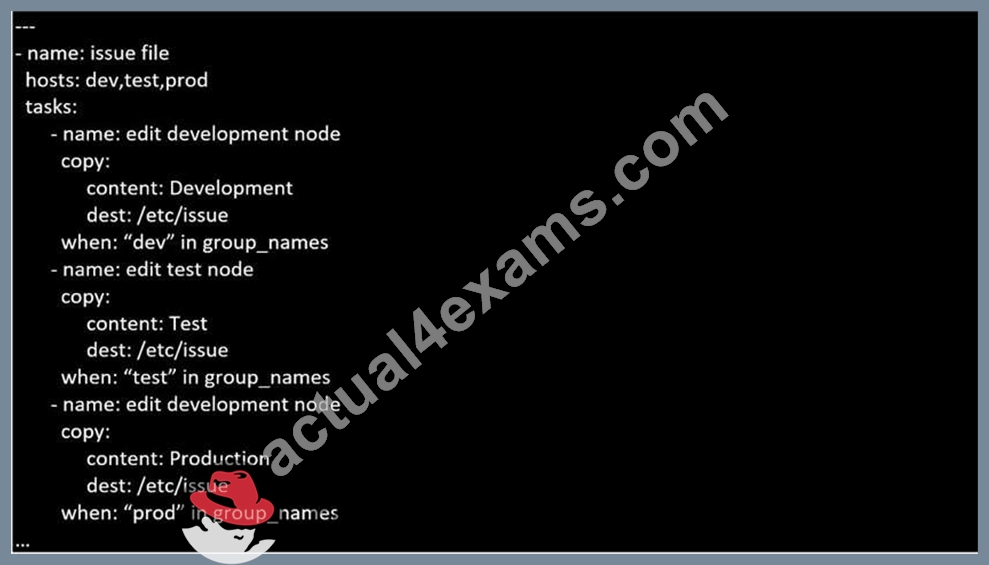
NEW QUESTION # 25
Modify file content.
------------------------
Create a playbook called /home/admin/ansible/modify.yml as follows:
* The playbook runs on all inventory hosts
* The playbook replaces the contents of /etc/issue with a single line of text as
follows:
--> On hosts in the dev host group, the line reads: "Development"
--> On hosts in the test host group, the line reads: "Test"
--> On hosts in the prod host group, the line reads: "Production"
Answer:
Explanation:
Solution as:
# pwd
/home/admin/ansible
# vim modify.yml
---
- name:
hosts: all
tasks:
- name:
copy:
content: "Development"
dest: /etc/issue
when: inventory_hostname in groups['dev']
- name:
copy:
content: "Test"
dest: /etc/issue
when: inventory_hostname in groups['test']
- name:
copy:
content: "Production"
dest: /etc/issue
when: inventory_hostname in groups['prod']
:wq
# ansible-playbook modify.yml --syntax-check
# ansible-playbook modify.yml
NEW QUESTION # 26
Create a role called apache in "/home/admin/ansible/roles" with the following
requirements:
--> The httpd package is installed, enabled on boot, and started.
--> The firewall is enabled and running with a rule to allow access to the web server.
--> template file index.html.j2 is used to create the file /var/www/html/index.html
with the output:
Welcome to HOSTNAME on IPADDRESS
--> Where HOSTNAME is the fqdn of the managed node and IPADDRESS is the IP-Address of
the managed node.
note: you have to create index.html.j2 file.
--> Create a playbook called httpd.yml that uses this role and the playbook runs on
hosts in the webservers host group.
Answer:
Explanation:
Solution as:
----------
# pwd
/home/admin/ansible/roles/
# ansible-galaxy init apache
# vim apache/vars/main.yml
---
# vars file for apache
http_pkg: httpd
firewall_pkg: firewalld
http_srv: httpd
firewall_srv: firewalld
rule: http
webpage: /var/www/html/index.html
template: index.html.j2
:wq!
# vim apache/tasks/package.yml
---
- name: Installing packages
yum:
name:
- "{{http_pkg}}"
- "{{firewall_pkg}}"
state: latest
:wq!
# vim apache/tasks/service.yml
---
- name: start and enable http service
service:
name: "{{http_srv}}"
enabled: true
state: started
- name: start and enable firewall service
service:
name: "{{firewall_srv}}"
enabled: true
state: started
:wq!
# vim apache/tasks/firewall.yml
---
- name: Adding http service to firewall
firewalld:
service: "{{rule}}"
state: enabled
permanent: true
immediate: true
:wq!
# vim apache/tasks/webpage.yml
---
- name: creating template file
template:
src: "{{template}}"
dest: "{{webpage}}"
notify: restart_httpd
!wq
# vim apache/tasks/main.yml
# tasks file for apache
- import_tasks: package.yml
- import_tasks: service.yml
- import_tasks: firewall.yml
- import_tasks: webpage.yml
:wq!
# vim apache/templates/index.html.j2
Welcome to {{ ansible_facts.fqdn }} on {{ ansible_facts.default_ipv4.address }}
# vim apache/handlers/main.yml
---
# handlers file for apache
- name: restart_httpd
service:
name: httpd
state: restarted
:wq!
# cd ..
# pwd
/home/admin/ansible/
# vim httpd.yml
---
- name: Including apache role
hosts: webservers
pre_tasks:
- name: pretask message
debug:
msg: 'Ensure webserver configuration'
roles:
- ./roles/apache
post_tasks:
- name: Check webserver
uri:
url: "http://{{ ansible_facts.default_ipv4.address }}"
return_content: yes
status_code: 200
:wq!
# ansible-playbook httpd.yml --syntax-check
# ansible-playbook httpd.yml
# curl http://serverx
NEW QUESTION # 27
Create a file called requirements.yml in /home/sandy/ansible/roles to install two roles. The source for the first role is geerlingguy.haproxy and geerlingguy.php. Name the first haproxy-role and the second php-role. The roles should be installed in /home/sandy/ansible/roles.
- A. in /home/sandy/ansible/roles
vim requirements.yml
Run the requirements file from the roles directory:
ansible-galaxy install -r requirements.yml -p /home/sandy/ansible/roles - B. in /home/sandy/ansible/roles
vim requirements.yml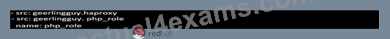
Run the requirements file from the roles directory:
ansible-galaxy install -r requirements.yml -p /home/sandy/ansible/roles
Answer: A
NEW QUESTION # 28
Create a playbook called timesvnc.yml in /home/sandy/ansible using rhel system role timesync. Set the time to use currently configured nip with the server 0.uk.pool.ntp.org. Enable burst. Do this on all hosts.
Answer:
Explanation:
Solution as:
NEW QUESTION # 29
Create a playbook called hwreport.yml that produces an output file called /root/
hwreport.txt on all managed nodes with the following information:
------------------------------------------------------------------------------------------------------
--> Inventory host name
--> Total memory in MB
--> BIOS version
--> Size of disk device vda
--> Size of disk device vdb
Each line of the output file contains a single key-value pair.
* Your playbook should:
--> Download the file hwreport.empty from the URL http://classroom.example.com/
hwreport.empty and
save it as /root/hwreport.txt
--> Modify with the correct values.
note: If a hardware item does not exist, the associated value should be set to NONE
----------------------------------------------------------------------------------------------
while practising you to create these file hear. But in exam have to download as per
questation.
hwreport.txt file consists.
my_sys=hostname
my_BIOS=biosversion
my_MEMORY=memory
my_vda=vdasize
my_vdb=vdbsize
Answer:
Explanation:
Solution as:
# pwd
/home/admin/ansible
# vim hwreport.yml
- name:
hosts: all
ignore_errors: yes
tasks:
- name: download file
get_url:
url: http://classroom.example.com/content/ex407/hwreport.empty
dest: /root/hwreport.txt
- name: vdasize
replace:
regexp: "vdasize"
replace: "{{ ansible_facts.devices.vda.size }}"
dest: /root/hwreport.txt
register: op1
- debug:
var: op1
- name: none
replace:
regexp: "vdasize"
replace: NONE
dest: /root/hwreport.txt
when:
op1.failed == true
- name: vdbsize
replace:
regexp: "vdbsize"
replace: "{{ ansible_facts.devices.vdb.size }}"
dest: /root/hwreport.txt
register: op2
- debug:
var: op2
- name: none
replace:
regexp: "vdbsize"
replace: NONE
dest: /root/hwreport.txt
when:
op2.failed == true
- name: sysinfo
replace:
regexp: "{{item.src}}"
replace: "{{item.dest}}"
dest: /root/hwreport.txt
loop:
- src: "hostname"
dest: "{{ ansible_facts.fqdn }}"
- src: "biosversion"
dest: "{{ ansible_facts.bios_version }}"
- src: "memory"
dest: "{{ ansible_facts.memtotal_mb }}"
:wq!
# ansible-playbook hwreport.yml --syntax-check
# ansible-playbook hwreport.yml
NEW QUESTION # 30
Create a playbook called regulartasks.yml which has the system that append the date to /root/datefile every day at noon. Name is job 'datejob'
Answer:
Explanation:
Solution as:
NEW QUESTION # 31
Create a file called specs.empty in home/bob/ansible on the local machine as follows:
HOST=
MEMORY=
BIOS=
VDA_DISK_SIZE=
VDB_DISK_SIZE=
Create the playbook /home/bob/ansible/specs.yml which copies specs.empty to all remote nodes' path /root/specs.txt. Using the specs.yml playbook then edit specs.txt on the remote machines to reflect the appropriate ansible facts.
Answer:
Explanation:
Solution as:
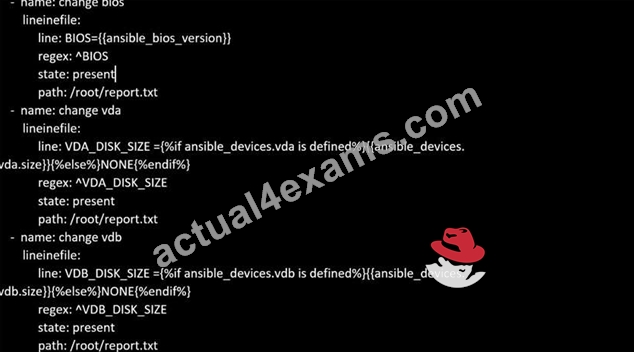
NEW QUESTION # 32
Create an ansible vault password file called lock.yml with the password reallysafepw in the /home/sandy/ansible directory. In the lock.yml file define two variables. One is pw_dev and the password is 'dev' and the other is pw_mgr and the password is 'mgr' Create a regular file called secret.txt which contains the password for lock.yml.
- A. ansible-vault create lock.yml
New Vault Password: reallysafepw
- B. ansible-vault create lock.yml
New Vault Password: reallysafepw
Confirm: reallysafepw
Answer: B
NEW QUESTION # 33
Create a file called packages.yml in /home/sandy/ansible to install some packages for the following hosts. On dev, prod and webservers install packages httpd, mod_ssl, and mariadb. On dev only install the development tools package. Also, on dev host update all the packages to the latest.
Answer:
Explanation:
Solution as: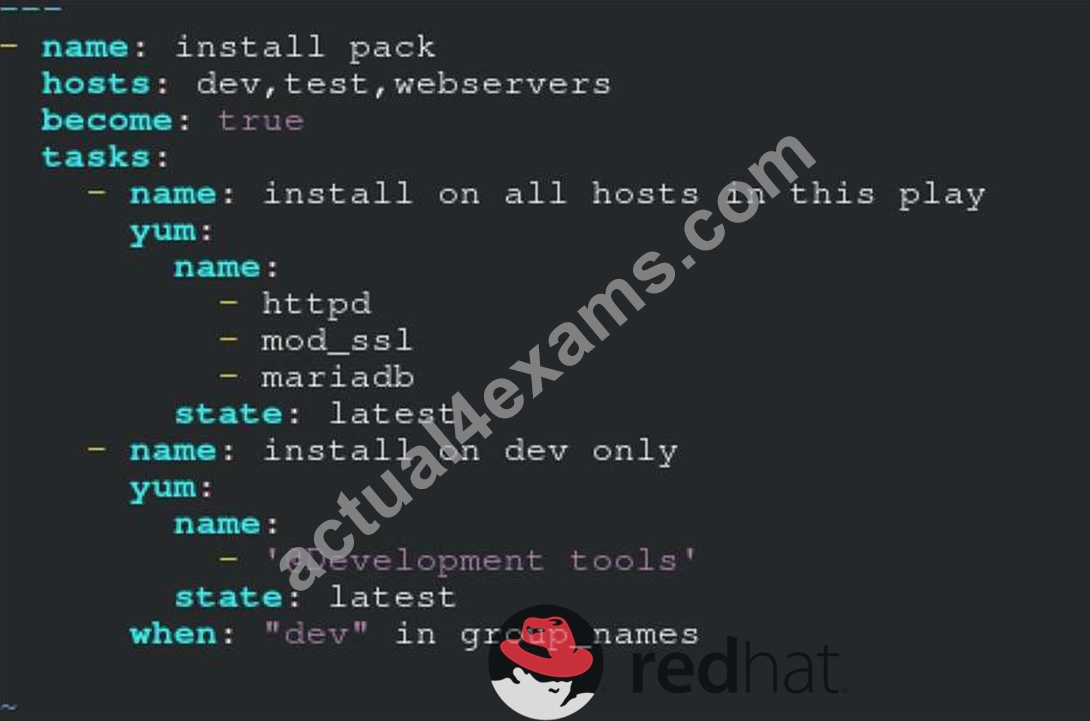
** NOTE 1 a more acceptable answer is likely 'present' since it's not asking to install the latest
state: present
** NOTE 2 need to update the development node
- name: update all packages on development node
yum:
name: '*'
state: latest
NEW QUESTION # 34
Create a file called specs.empty in home/bob/ansible on the local machine as follows:
HOST=
MEMORY=
BIOS=
VDA_DISK_SIZE=
VDB_DISK_SIZE=
Create the playbook /home/bob/ansible/specs.yml which copies specs.empty to all remote nodes' path /root/specs.txt. Using the specs.yml playbook then edit specs.txt on the remote machines to reflect the appropriate ansible facts.
- A. Solution as:


- B. Solution as:
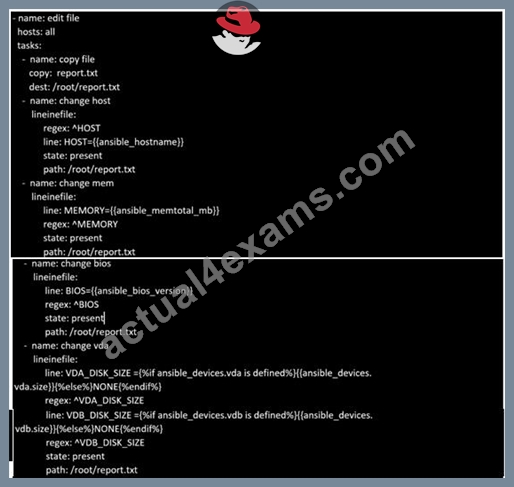
Answer: B
NEW QUESTION # 35
Create an empty encrypted file called myvault.yml in /home/sandy/ansible and set the password to notsafepw. Rekey the password to iwejfj2331.
- A. ansible-vault create myvault.yml
Create new password: notsafepw Confirm password: notsafepw ansible-vault rekey myvault.yml Current password: notsafepw New password: iwejfj2221 Confirm password: iwejfj2221 - B. ansible-vault create myvault.yml
Create new password: notsafepw Confirm password: notsafepw ansible-vault rekey myvault.yml Current password: notsafepw New password: iwejfj2331 Confirm password: iwejfj2221
Answer: A
NEW QUESTION # 36
Create a file called requirements.yml in /home/sandy/ansible/roles a file called role.yml in /home/sandy/ansible/. The haproxy-role should be used on the proxy host. And when you curl http://node3.example.com it should display "Welcome to node4.example.com" and when you curl again "Welcome to node5.example.com" The php-role should be used on the prod host.
Answer:
Explanation:
Solution as: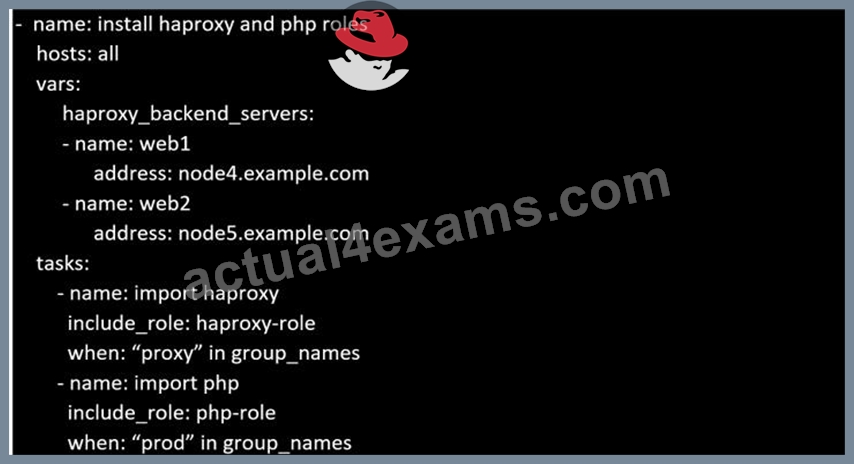
Check the proxy host by curl http://node3.example.com
NEW QUESTION # 37
Create Logical volumes with lvm.yml in all nodes according to following
requirements.
----------------------------------------------------------------------------------------
* Create a new Logical volume named as 'data'
* LV should be the member of 'research' Volume Group
* LV size should be 1500M
* It should be formatted with ext4 file-system.
--> If Volume Group does not exist then it should print the message "VG Not found"
--> If the VG can not accommodate 1500M size then it should print "LV Can not be
created with
following size", then the LV should be created with 800M of size.
--> Do not perform any mounting for this LV.
Answer:
Explanation:
Solution as:
# pwd
/home/admin/ansible
# vim lvm.yml
---
- name:
hosts: all
ignore_errors: yes
tasks:
- name:
lvol:
lv: data
vg: research
size: "1500"
- debug:
msg: "VG Not found"
when: ansible_lvm.vgs.research is not defined
- debug:
msg: "LV Can not be created with following size"
when: ansible_lvm.vgs.research.size_g < "1.5"
- name:
lvol:
lv: data
vg: research
size: "800"
when: ansible_lvm.vgs.research.size_g < "1.5"
- name:
filesystem:
fstype: ext4
dev: /dev/research/data
:wq!
# ansible-playbook lvm.yml --syntax-check
# ansible-playbook lvm.yml
NEW QUESTION # 38
Create a playbook called webdev.yml in 'home/sandy/ansible. The playbook will create a directory Avcbdev on dev host. The permission of the directory are 2755 and owner is webdev. Create a symbolic link from /Webdev to /var/www/html/webdev. Serve a file from Avebdev7index.html which displays the text "Development" Curl http://node1.example.com/webdev/index.html to test
Answer:
Explanation:
Solution as: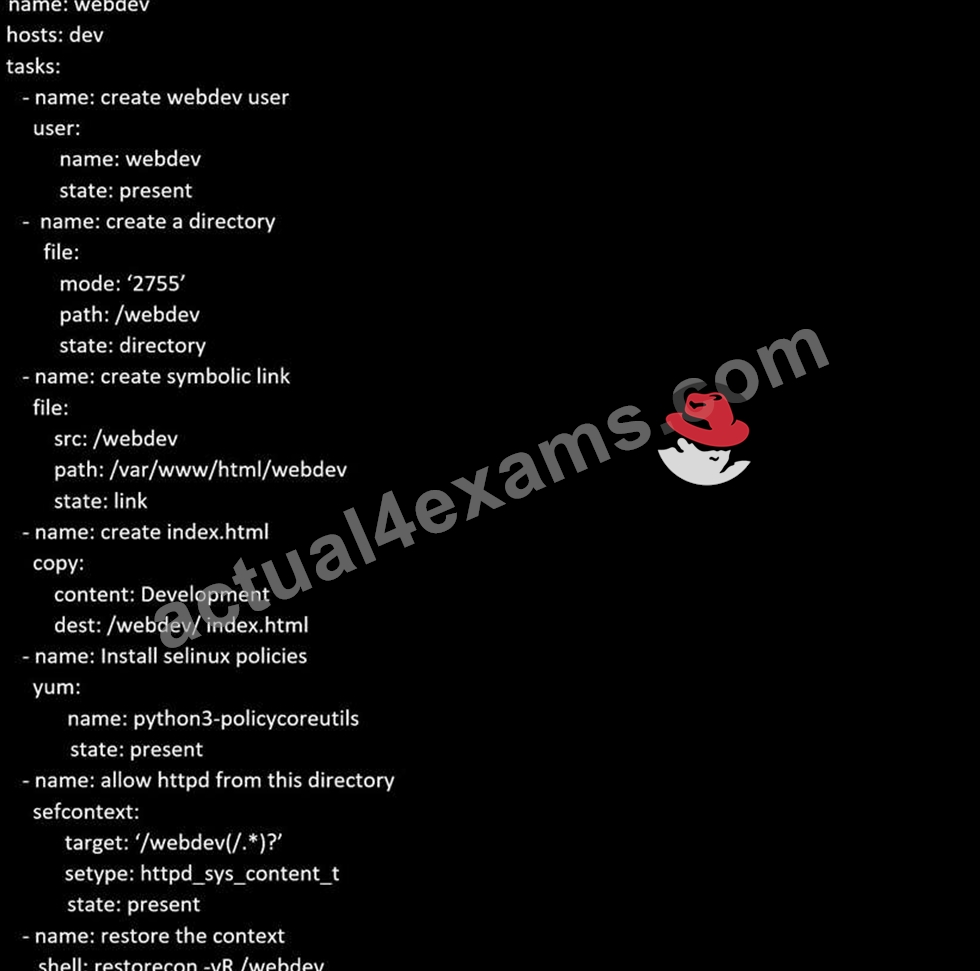
NEW QUESTION # 39
Create a playbook called packages.yml that:
----------------------------------------------
--> Installs the php and mariadb packages on hosts in the dev, test, and prod host
groups.
--> Installs the Development Tools package group on hosts in the dev host group.
--> Updates all packages to the latest version on hosts in the dev host group.
Answer:
Explanation:
Solution as:
# pwd
home/admin/ansible/
# vim packages.yml
---
- name: Install the packages
hosts: dev,test,prod
vars:
- php_pkg: php
- mariadb_pkg: mariadb
tasks:
- name: install the packages
yum:
name:
- "{{ php_pkg }}"
- "{{ mariadb_pkg }}"
state: latest
- name: install the devops tool packages
hosts: dev
tasks:
- name: install devepment tools
yum:
name: "@Development Tools"
state: latest
- name: upgrade all the packages
yum:
name: "*"
state: latest
exclude: kernel*
!wq
# ansible-playbook package.yml --syntax-check
# ansible-playbook package.yml
NEW QUESTION # 40
......
EX294 PDF 100% Cover Real Exam Questions: https://www.actual4exams.com/EX294-valid-dump.html
RedHat EX294 Real Exam Questions Guaranteed Updated Dump: https://drive.google.com/open?id=1fOFwCmxjdVGDLZEgTTB5CkCNWauBJBCJ

